Abusing Windows Internals
Leverage windows internals components to evade common detection solutions, using modern tool-agnostic approaches.

Task 1: Introduction
Q1: Start the provided machine and move on to the next tasks.
Ans1: No answer needed
Task 2: Abusing Processes
Q1: Identify a PID of a process running as THM-Attacker to target. Once identified supply the PID as an argument to execute shellcode-injector.exe located in the Injectors directory on the desktop.
Ans1: No answer needed
Q2: What flag is obtained after injecting the shellcode?
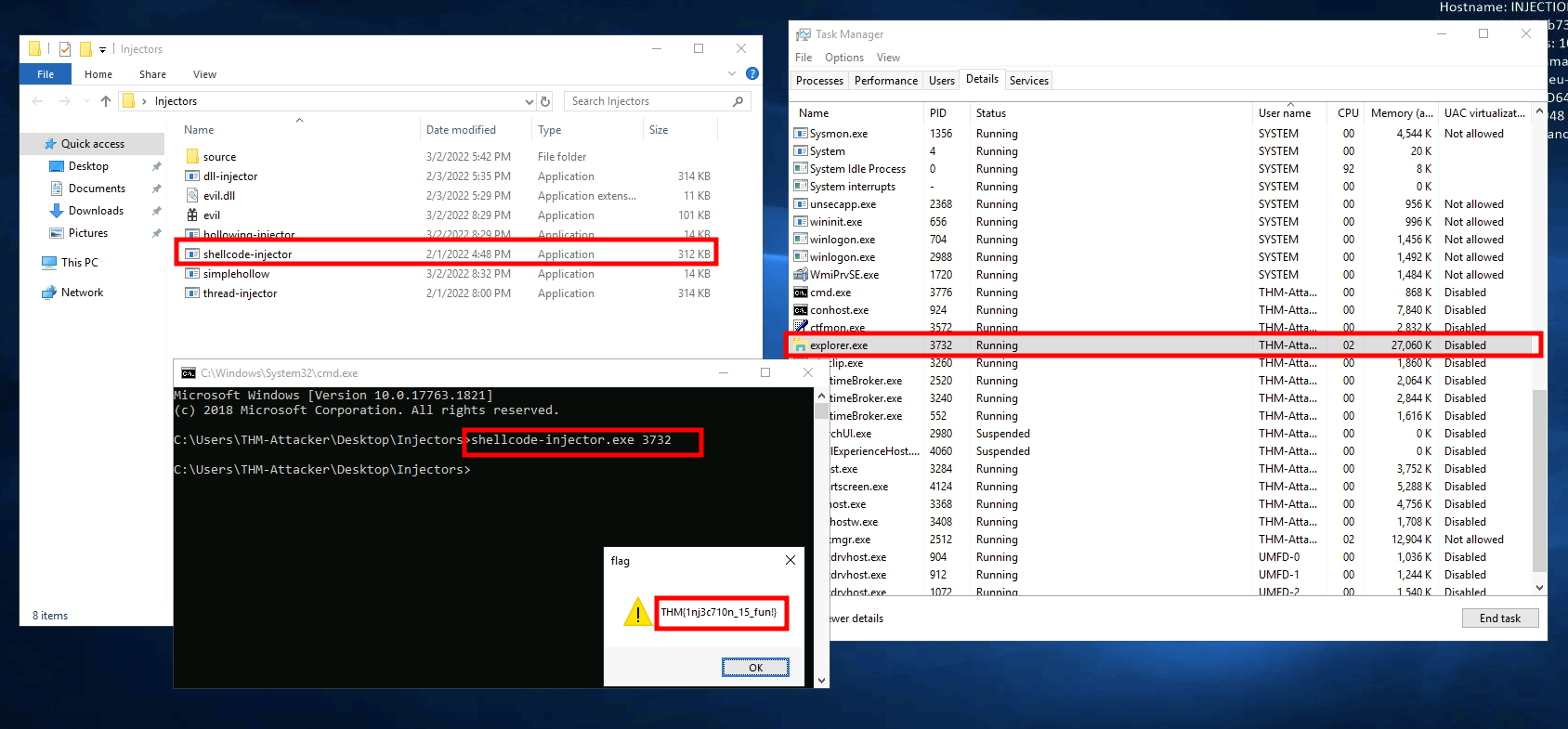
Ans2: THM{1nj3c710n_15_fun!}
Task 3: Expanding Process Abuse
Q1: Identify a PID of a process running as THM-Attacker to target. Supply the PID and executable name as arguments to execute hollowing-injector.exe located in the injectors directory on the desktop.
Ans1: No answer needed
Q2: What flag is obtained after hollowing and injecting the shellcode?
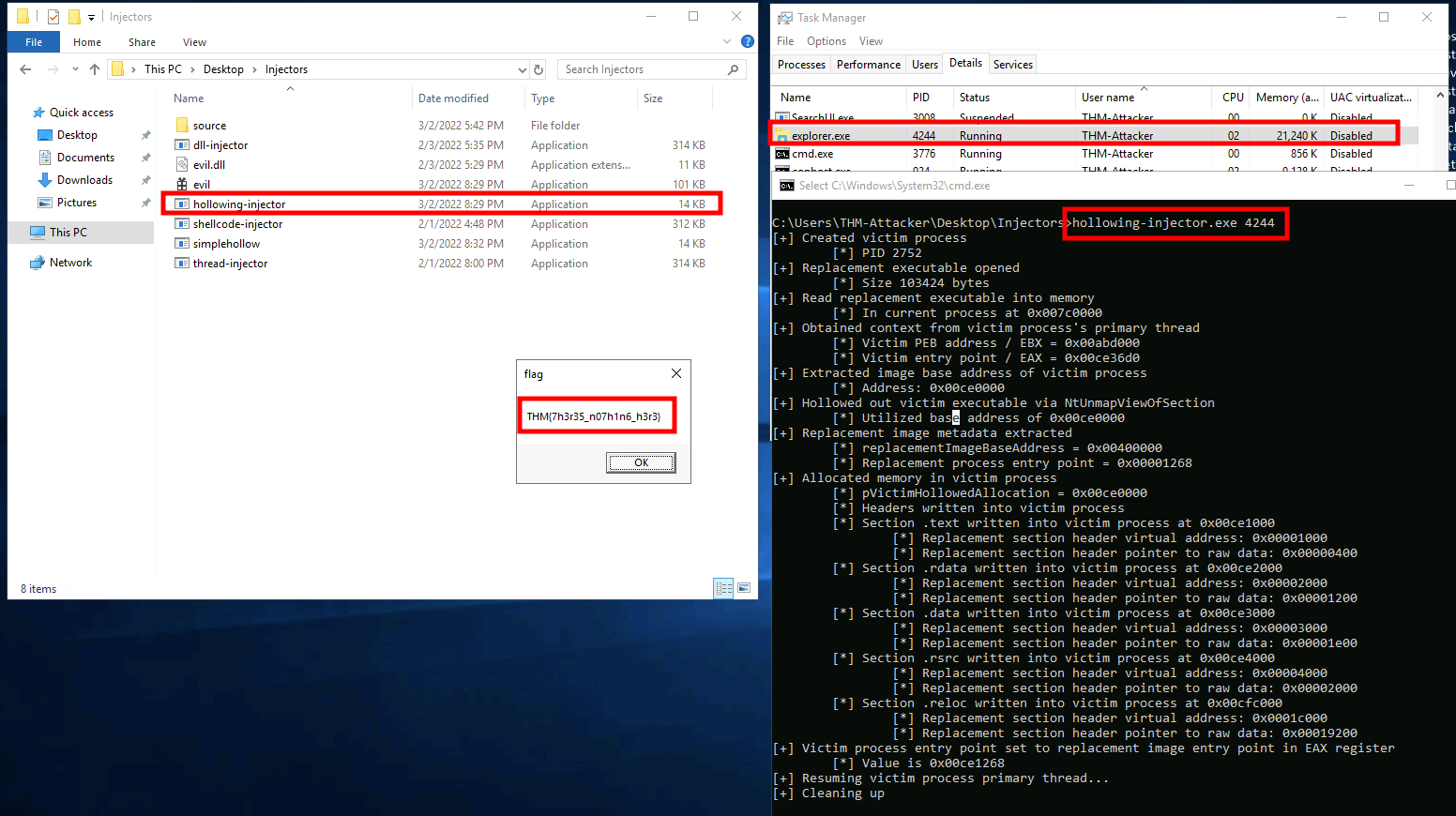
Ans2: THM{7h3r35_n07h1n6_h3r3}
Task 4: Abusing Process Components
Q1: Identify a PID of a process running as THM-Attacker to target. Supply the PID as an argument to execute thread-injector.exe located in the Injectors directory on the desktop.
Ans1: No answer needed
Q2: What flag is obtained after hijacking the thread?
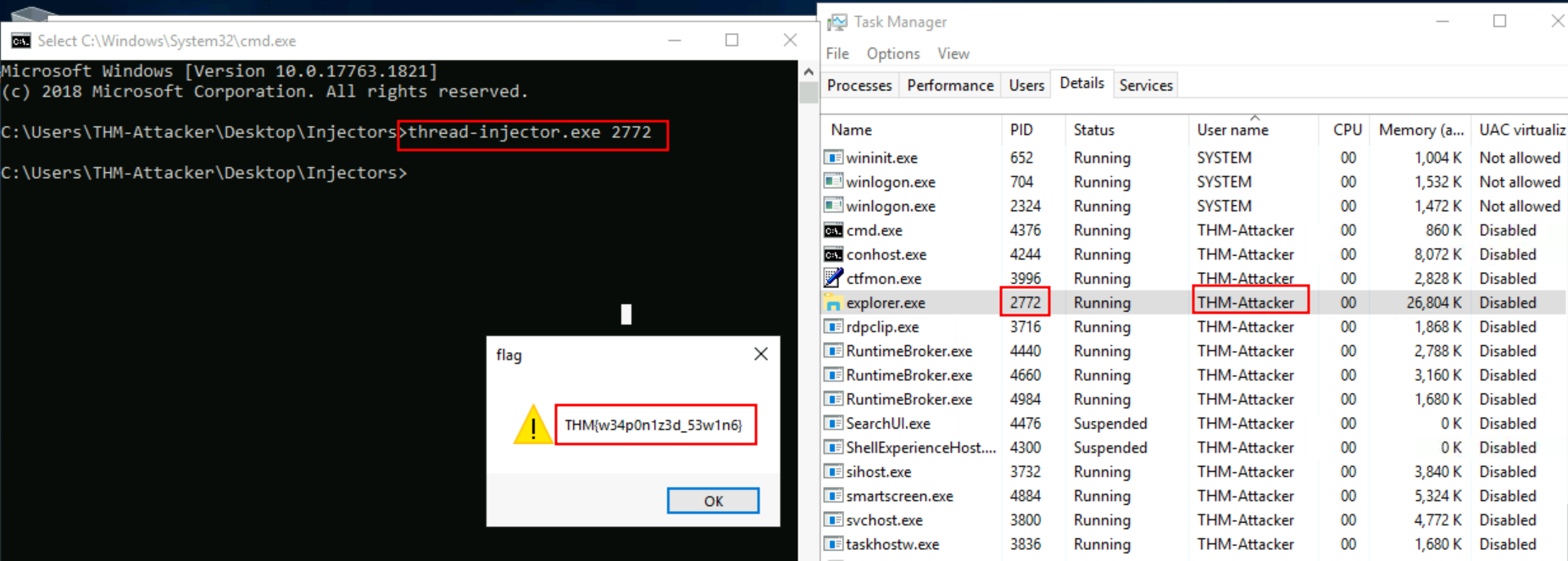
Ans2: THM{w34p0n1z3d_53w1n6}
Task 5: Abusing DLLs
Q1: Identify a PID and name of a process running as THM-Attacker to target. Supply the name and malicious DLL found in the Injectors directory as arguments to execute dll-injector.exe located in the Injectors directory on the desktop.
Ans1: No answer needed
Q2: What flag is obtained after injecting the DLL?

Ans2: THM{n07_4_m4l1c10u5_dll}
Task 6: Memory Execution Alternatives
Q1: What protocol is used to execute asynchronously in the context of a thread?
Ans1: Asynchronous Procedure Call
Q2: What is the Windows API call used to queue an APC function?
Ans2: QueueUserAPC
Q3: Can the void function pointer be used on a remote process? (y/n)
Ans3: n
Task 7: Case Study in Browser Injection and Hooking
Q1: What alternative Windows API call was used by TrickBot to create a new user thread?
Ans1: RtlCreateUserThread
Q2: Was the injection techniques employed by TrickBot reflective? (y/n)
Ans2: y
Q3: What function name was used to manually write hooks?
Ans3: write_hook_iter
Task 8: Conclusion
Q1: Read the above and continue learning!
Ans1: No answer needed

