Enumerating Active Directory
This room covers various Active Directory enumeration techniques, their use cases as well as drawbacks.

Task 1: Why AD Enumeration
Q1: I have completed the Breaching AD network and am ready to learn about AD enumeration techniques.
Ans1: No answer needed
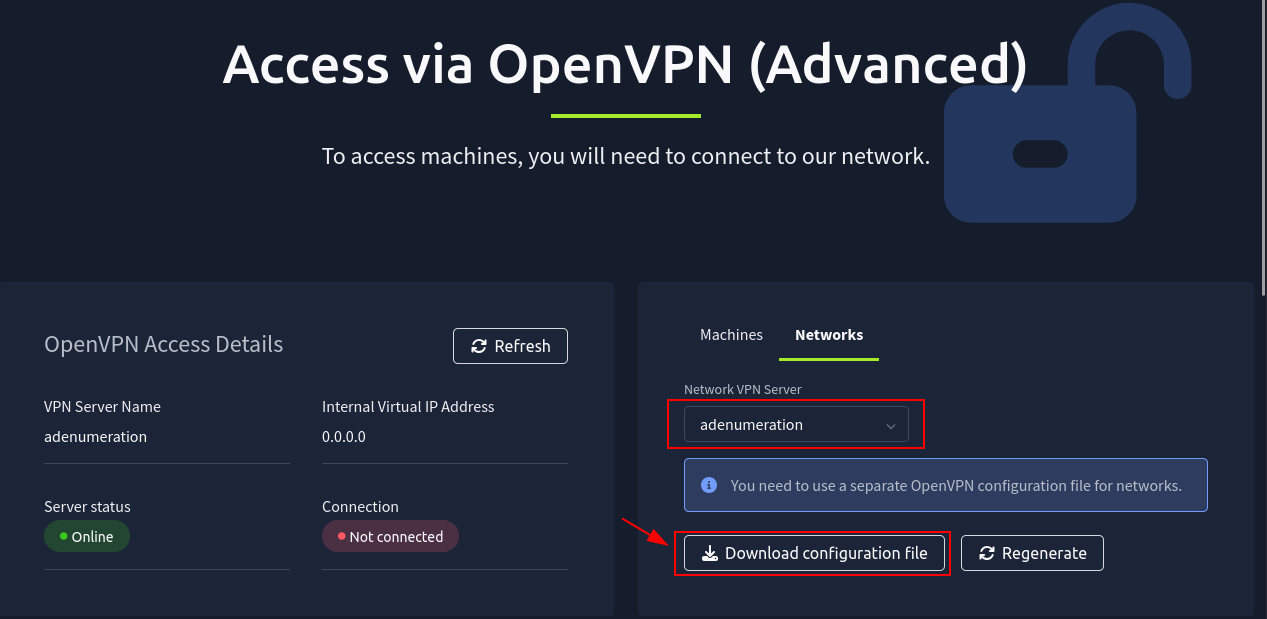
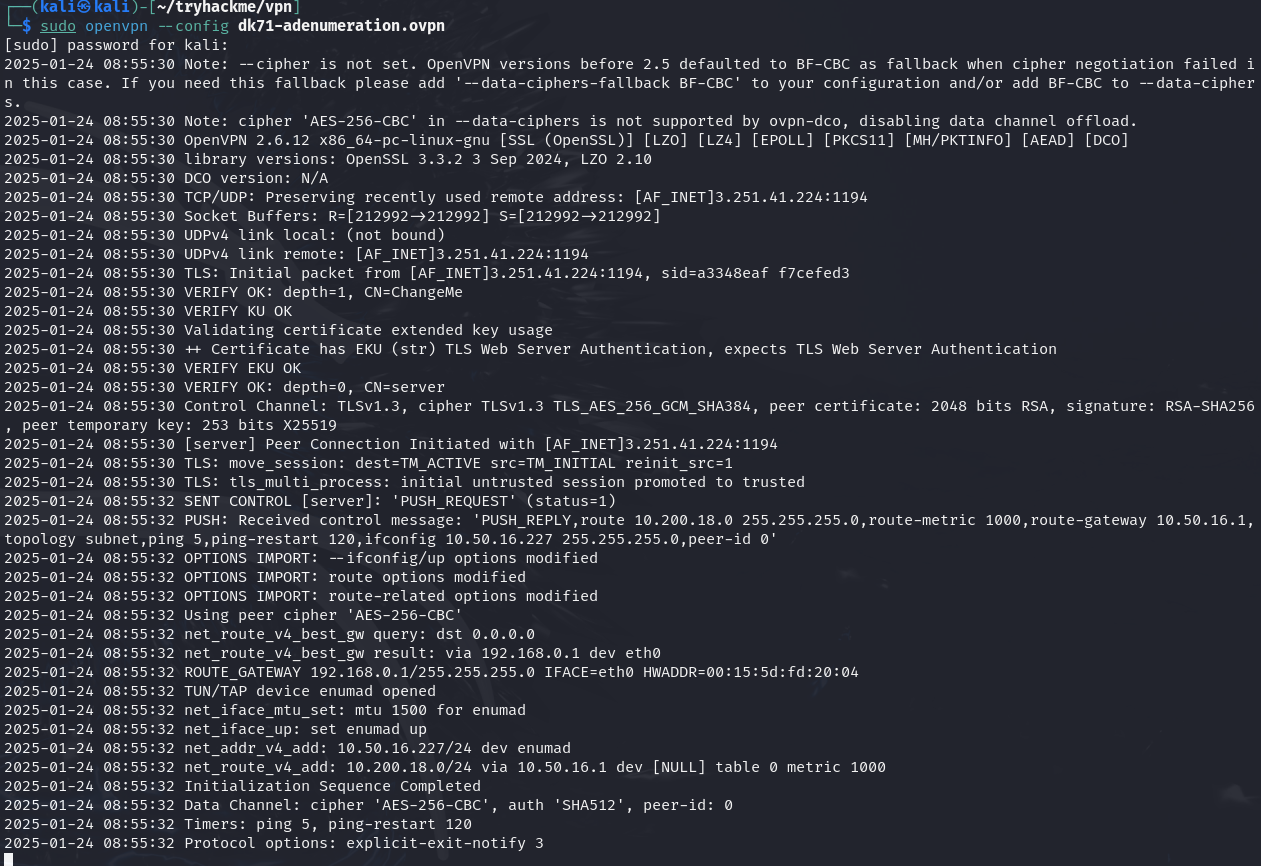
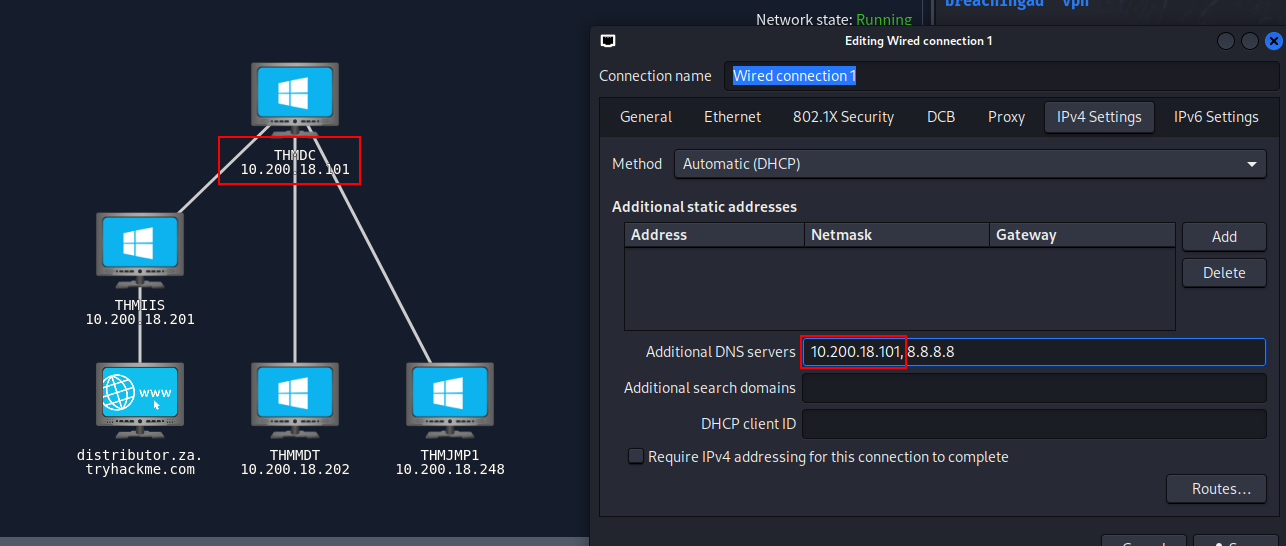
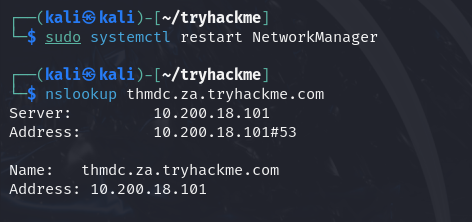
Q2: I have connected to the network and configured DNS.
Ans2: No answer needed
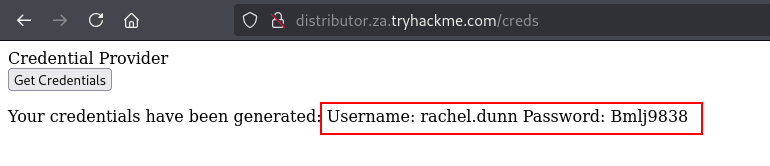
Q3: I have requested my credential pair from the distributor and verified that I can RDP and SSH into THMJMP1.
Ans3: No answer needed
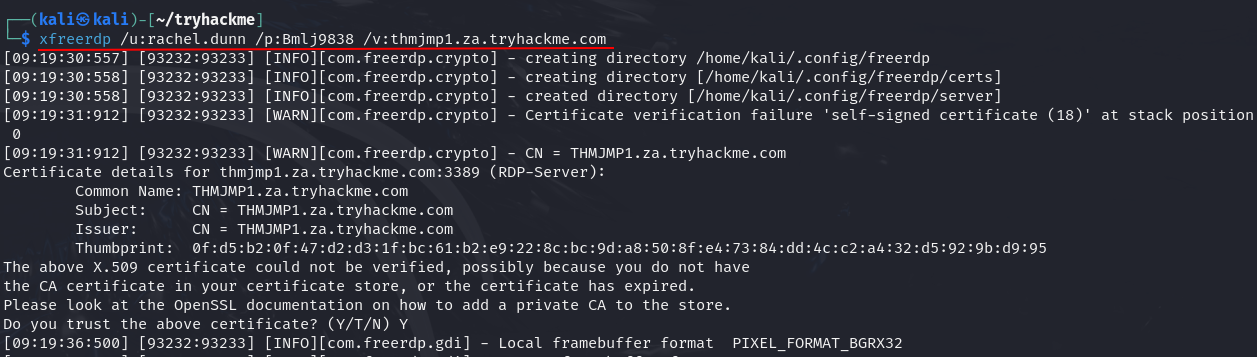
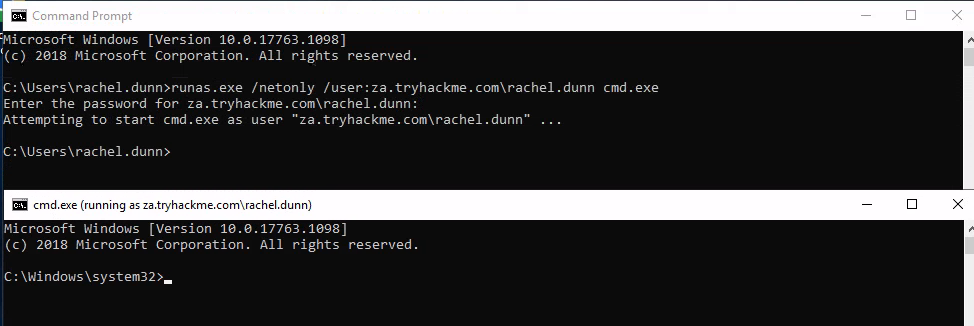
Task 2: Credential Injection
Q1: What native Windows binary allows us to inject credentials legitimately into memory?
Ans1: runas.exe
Q2: What parameter option of the runas binary will ensure that the injected credentials are used for all network connections?
Ans2: /netonly
Q3: What network folder on a domain controller is accessible by any authenticated AD account and stores GPO information?
Ans3: SYSVOL
Q4: When performing dir \za.tryhackme.com\SYSVOL, what type of authentication is performed by default?
Ans4: Kerberos Authentication
Task 3: Enumeration through Microsoft Management Console
Q1: How many Computer objects are part of the Servers OU?
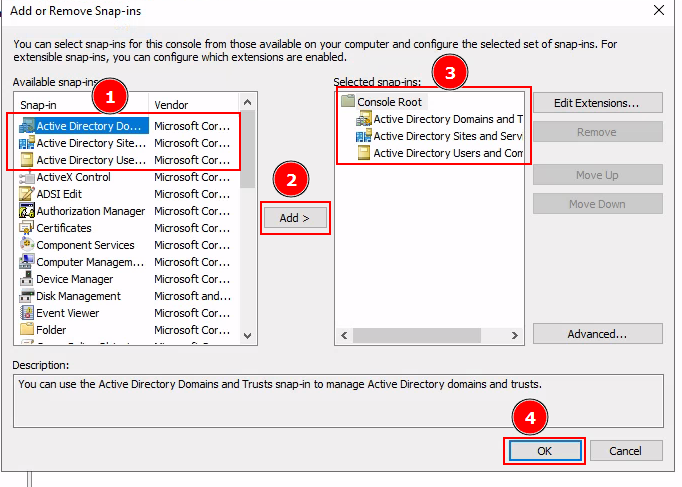

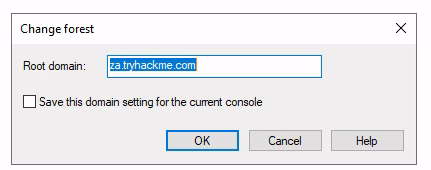
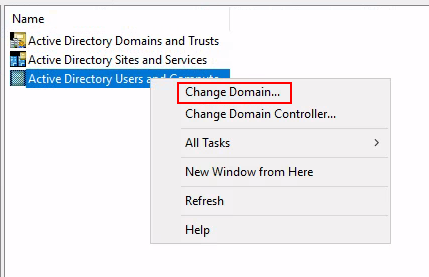
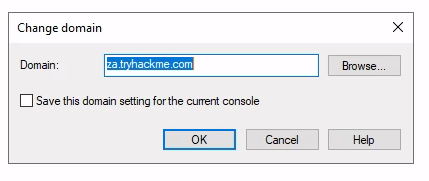
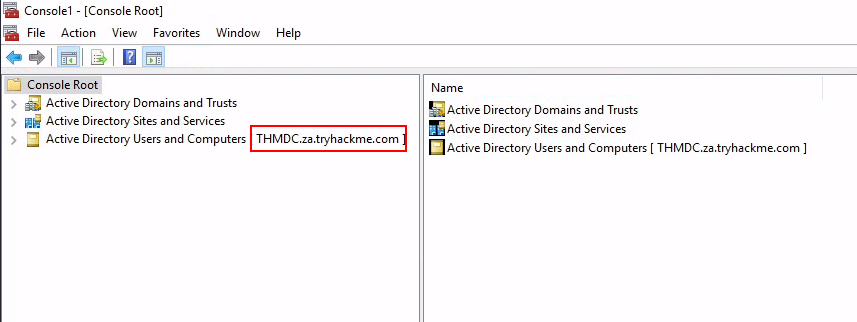
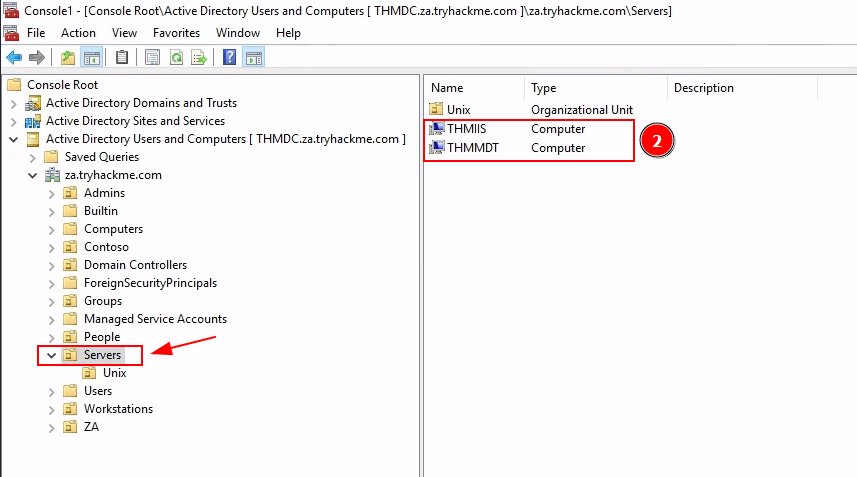
Ans1: 2
Q2: How many Computer objects are part of the Workstations OU?
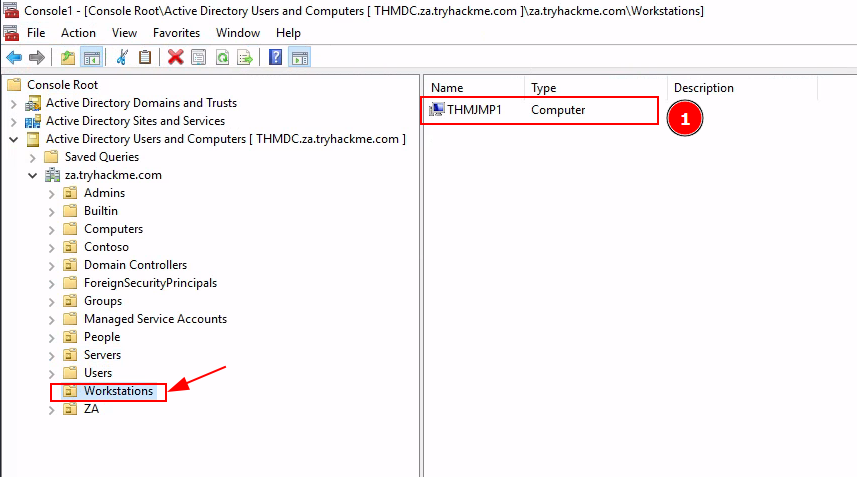
Ans2: 1
Q3: How many departments (Organisational Units) does this organisation consist of?
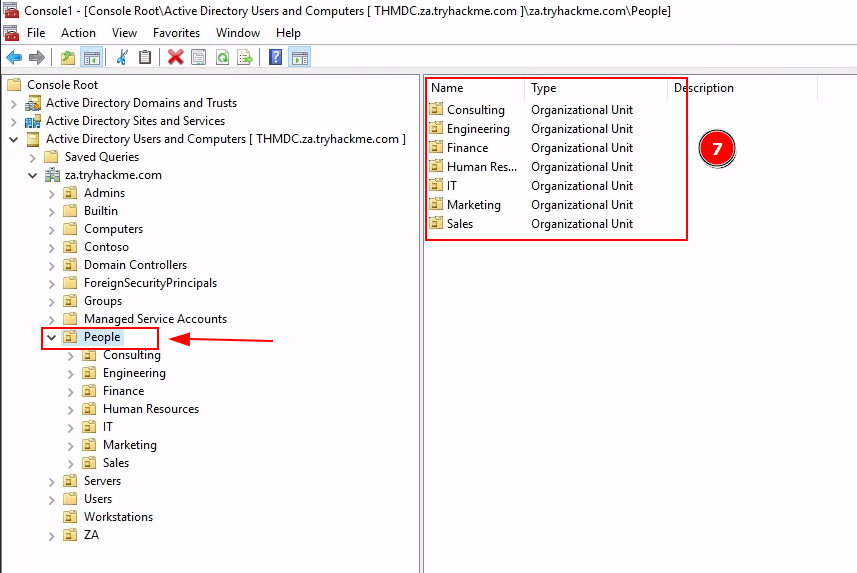
Ans3: 7
Q4: How many Admin tiers does this organisation have?
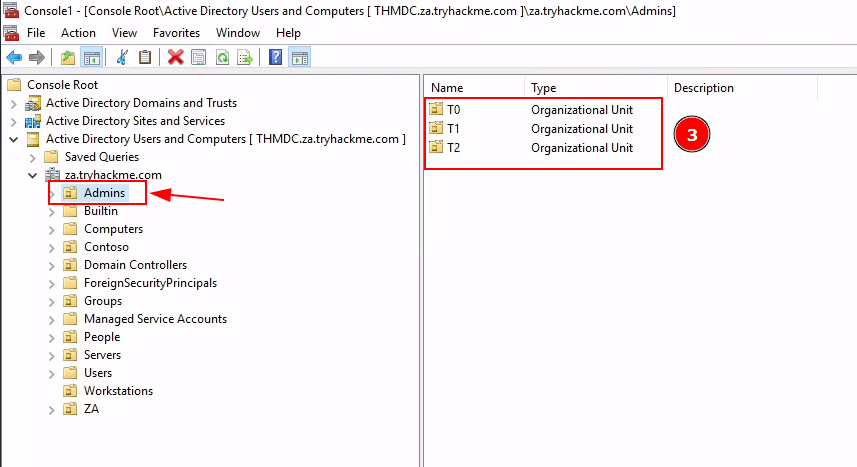
Ans4: 3
Q5: What is the value of the flag stored in the description attribute of the t0_tinus.green account?
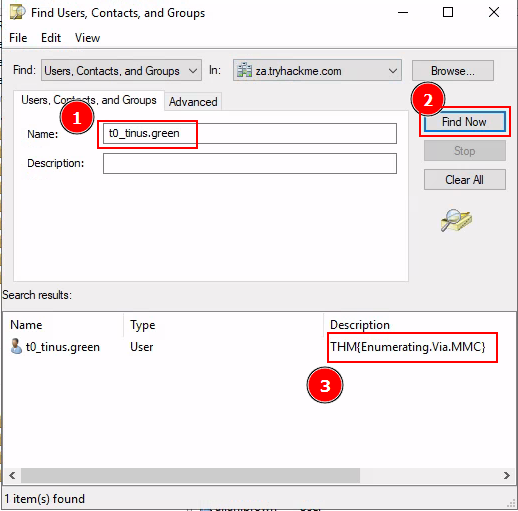
Ans5: THM{Enumerating.Via.MMC}
Task 4: Enumeration through Command Prompt
Q1: Apart from the Domain Users group, what other group is the aaron.harris account a member of?
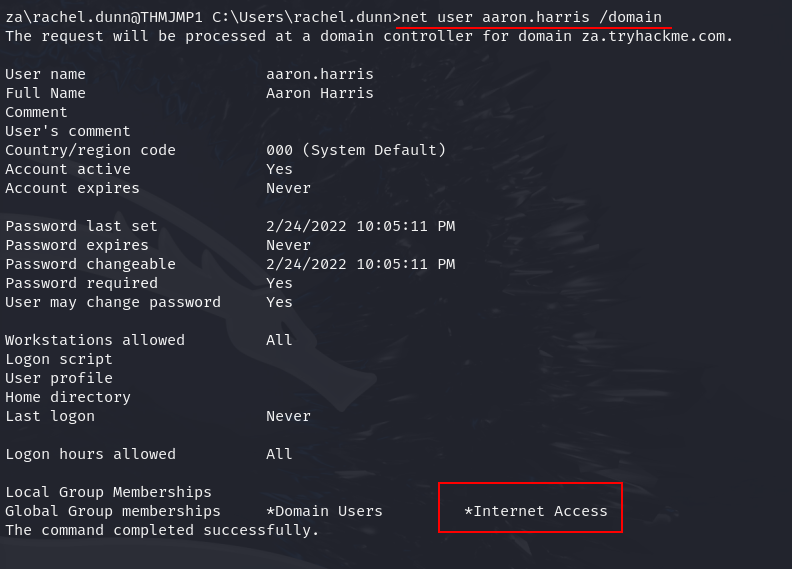
Ans1: Internet Access
Q2: Is the Guest account active? (Yay,Nay)
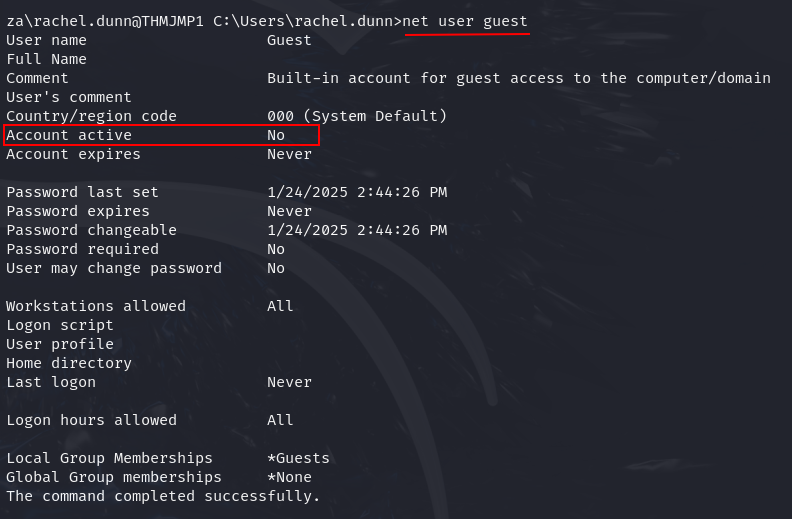
Ans2: Nay
Q3: How many accounts are a member of the Tier 1 Admins group?
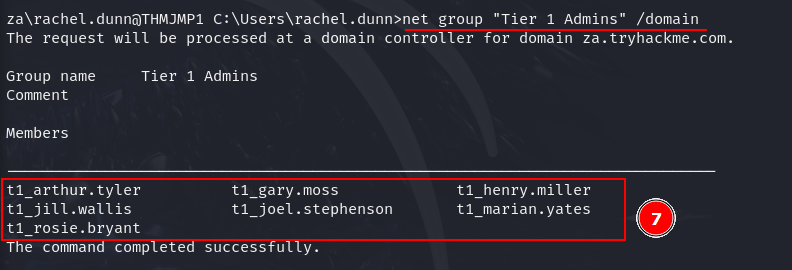
Ans3: 7
Q4: What is the account lockout duration of the current password policy in minutes?
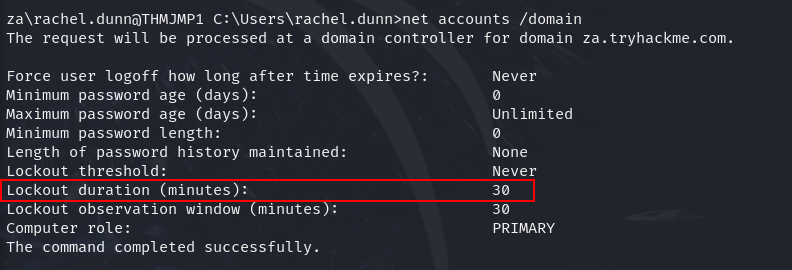
Ans4: 30
Task 5: Enumeration through PowerShell
Q1: What is the value of the Title attribute of Beth Nolan (beth.nolan)?
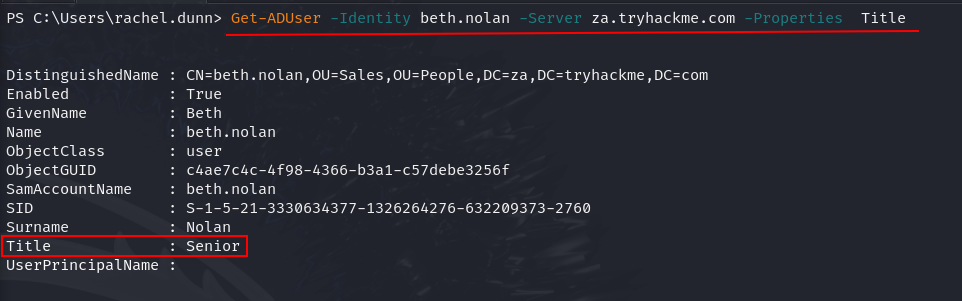
Ans1: Senior
Q2: What is the value of the DistinguishedName attribute of Annette Manning (annette.manning)?
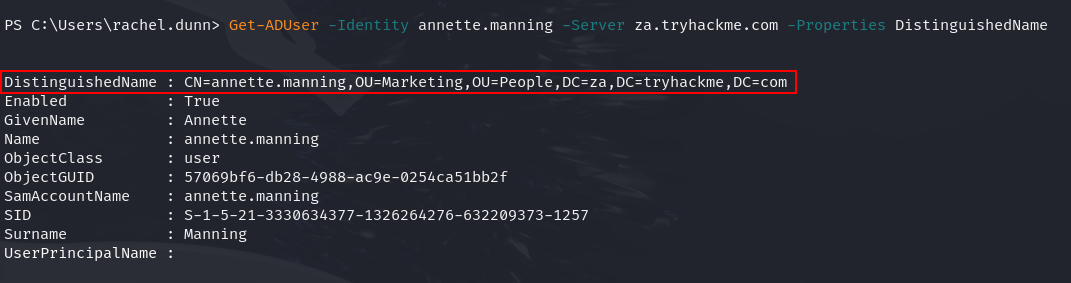
Ans2: CN=annette.manning,OU=Marketing,OU=People,DC=za,DC=tryhackme,DC=com
Q3: When was the Tier 2 Admins group created?
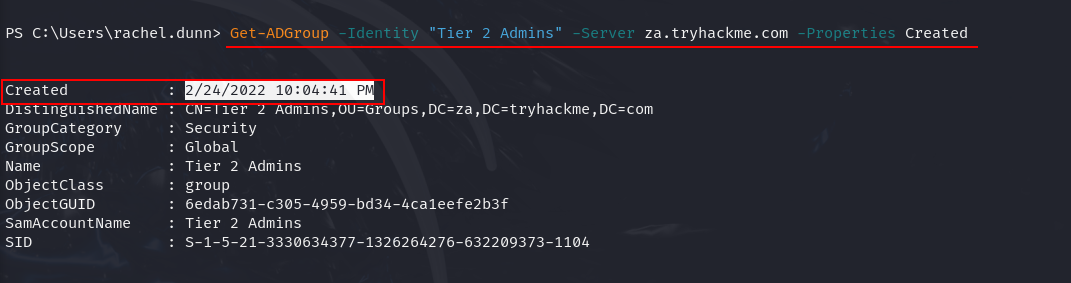
Ans3: 2/24/2022 10:04:41 PM
Q4: What is the value of the SID attribute of the Enterprise Admins group?
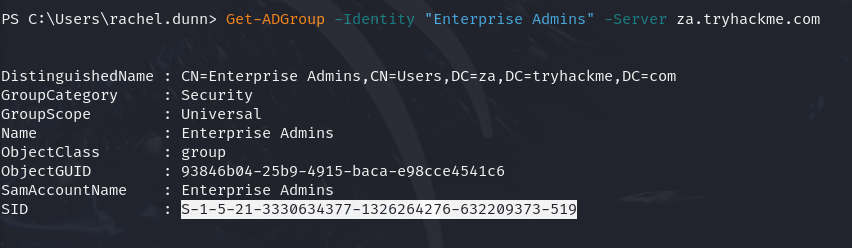
Ans4: S-1-5-21-3330634377-1326264276-632209373-519
Q5: Which container is used to store deleted AD objects?
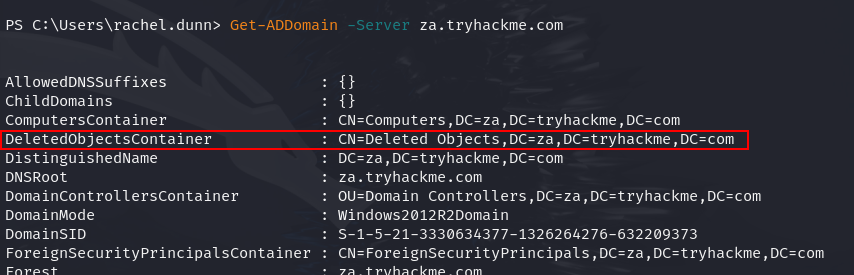
Ans5: CN=Deleted Objects,DC=za,DC=tryhackme,DC=com
Task 6: Enumeration through Bloodhound
Q1: What command can be used to execute Sharphound.exe and request that it recovers Session information only from the za.tryhackme.com domain without touching domain controllers?
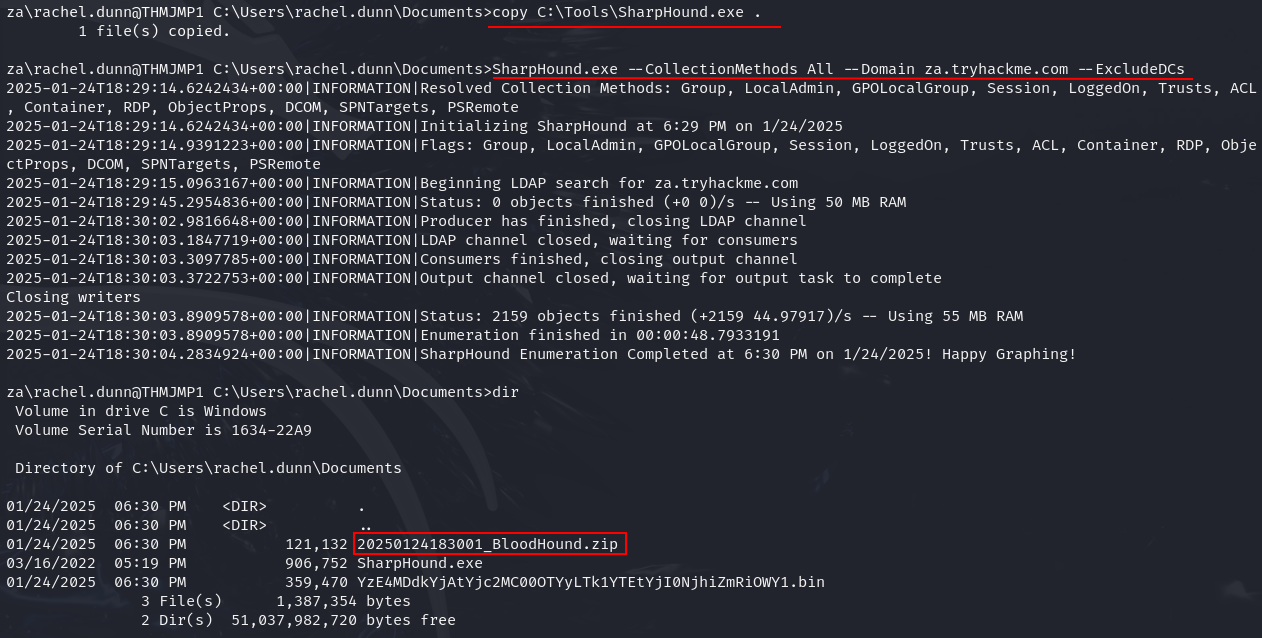
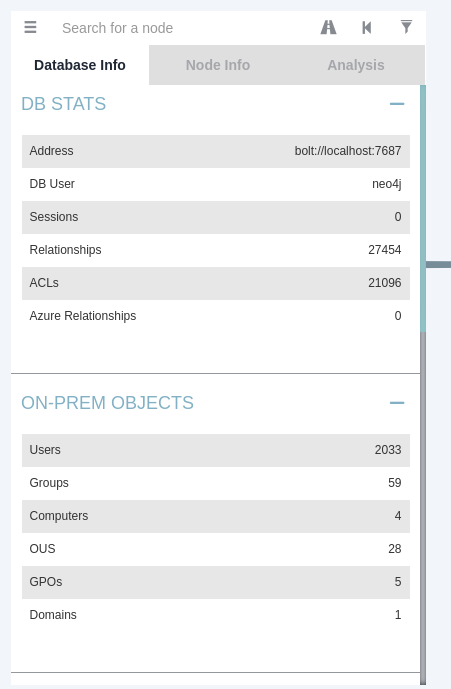
Ans1: Sharphound.exe –CollectionMethods Session –Domain za.tryhackme.com –ExcludeDCs
Q2: Apart from the krbtgt account, how many other accounts are potentially kerberoastable?
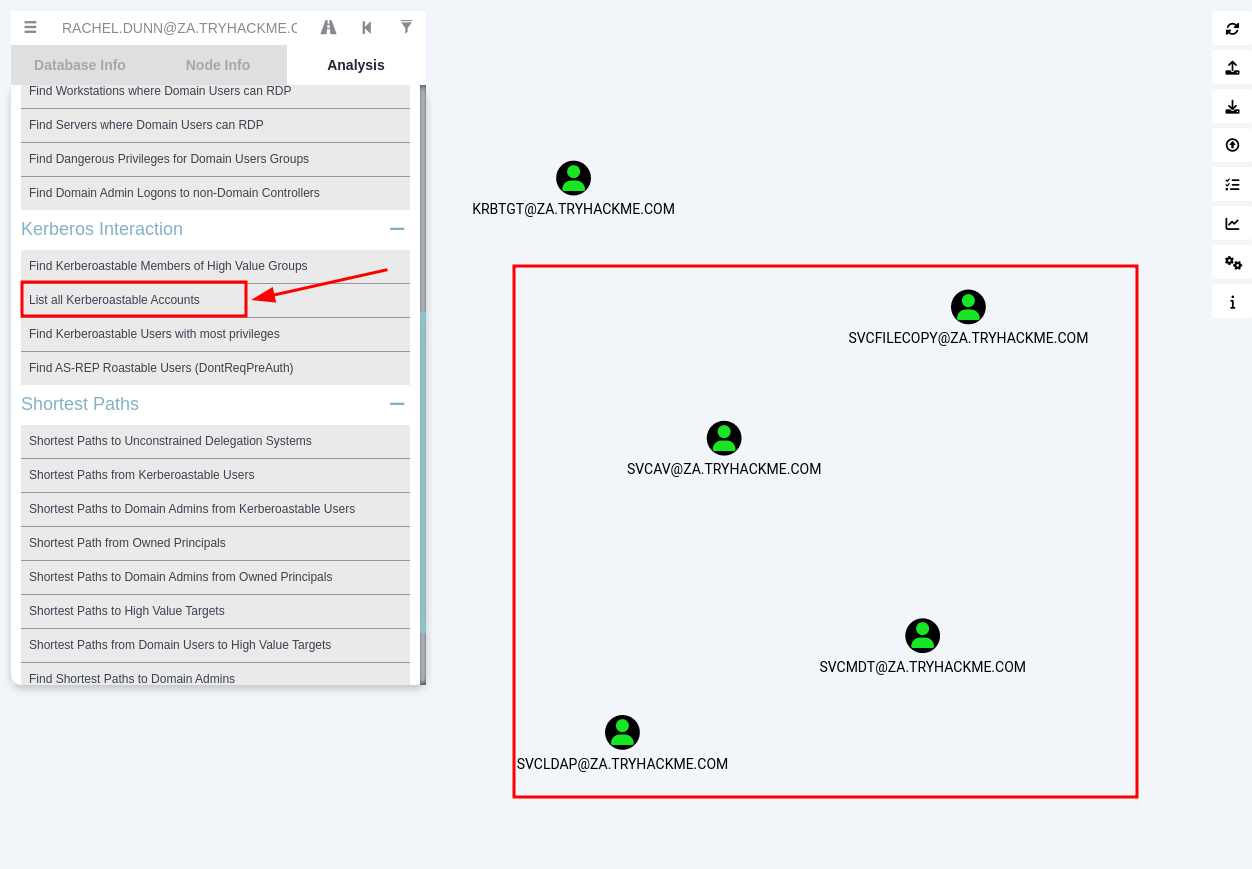
Ans2: 4
Q3: How many machines do members of the Tier 1 Admins group have administrative access to?
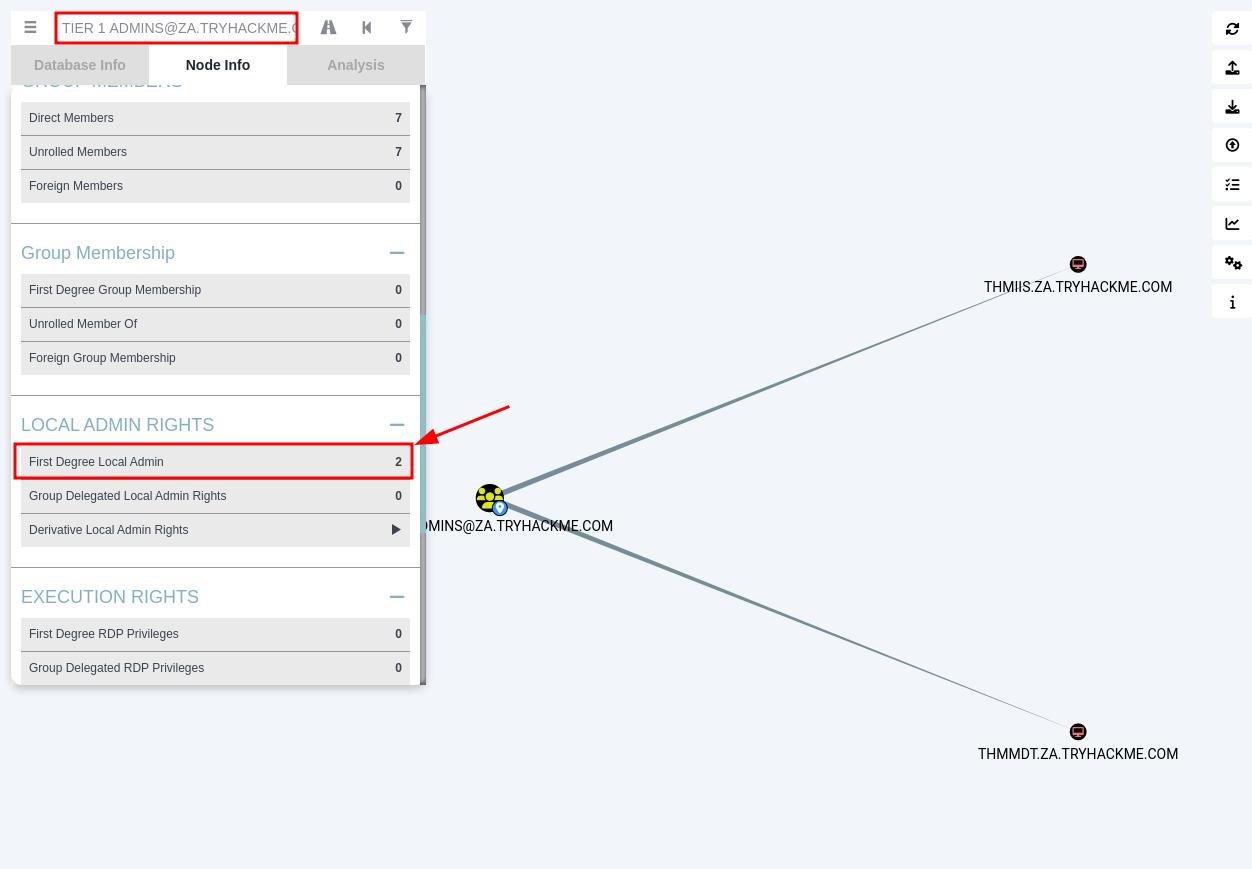
Ans3: 2
Q4: How many users are members of the Tier 2 Admins group?
Ans4: 15
Task 7: Conclusion
Q1: I understand AD enumeration and how we can possibly detect malicious AD enumeration.
Ans1: No answer needed

