Runtime Detection Evasion
Learn how to bypass common runtime detection measures, such as AMSI, using modern tool-agnostic approaches.

Task 1: Introduction
Q1: Start the provided machine and move on to the next tasks.
Ans1: No answer needed
Task 2: Runtime Detections
Q1: Read the above and answer the question below.
Ans1: No answer needed
Q2: What runtime detection measure is shipped natively with Windows?
Ans2: AMSI
Task 3: AMSI Overview
Q1: Read the above and answer the question below.
Ans1: No answer needed
Q2: What response value is assigned to 32768?
Ans2: AMSI_RESULT_DETECTED
Task 4: AMSI Instrumentation
Q1: Read the above and answer the question below.
Ans1: No answer needed
Q2: Will AMSI be instrumented if the file is only on disk? (Y/N)
Ans2: N
Task 5: PowerShell Downgrade
Q1: Read the above and practice downgrading PowerShell on the provided machine.
Ans1: No answer needed
Q2: Enter the flag obtained from the desktop after executing the command in cmd.exe.
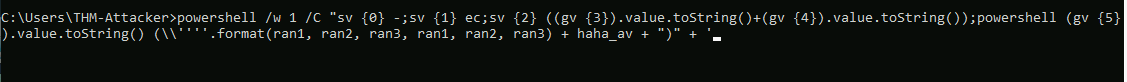
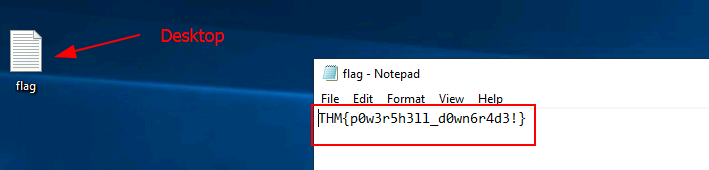
Ans2: THM{p0w3r5h3ll_d0wn6r4d3!}
Task 6: PowerShell Reflection
Q1: Read the above and practice leveraging the one-liner on the provided machine.To utilize the one-liner, you can run it in the same session as the desired malicious code or prepend it to the malicious code.
Ans1: No answer needed
Q2: Enter the flag obtained from the desktop after executing the command.
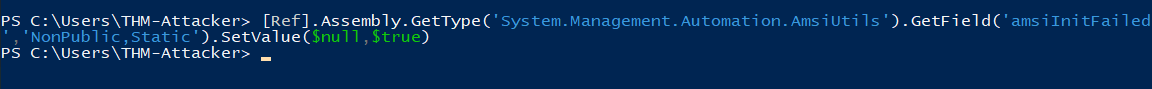
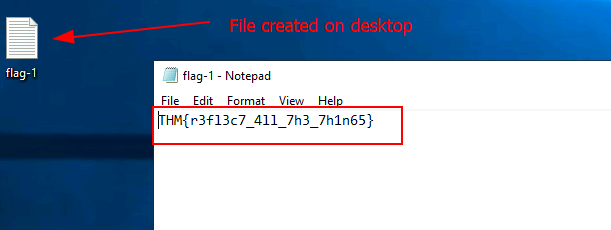
Ans2: THM{r3fl3c7_4ll_7h3_7h1n65}
Task 7: Patching AMSI
Q1: Read the above and execute/observe the script on the provided machine.
Ans1: No answer needed
Q2: Enter the flag obtained from the desktop after executing the command.
Ans2: THM{p47ch1n6_15n7_ju57_f0r_7h3_600d_6uy5}
Task 8: Automating for Fun and Profit
Q1: Read the above and continue to the next task.
Ans1: No answer needed
Task 9: Conclusion
Q1: Read the above and continue learning!
Ans1: No answer needed

